In this deployment, BGP is used for peering with ACI fabric and to exchange the virtual service routes. This deployment is mostly applicable for setups where BGP auto-scaling is required for virtual service scaling on SEs.
In vCenter write access mode, the NSX Advanced Load Balancer Controller is configured with a vCenter cloud connector. The Controller has write access permissions to vCenter and handles complete automation involved in creating Service Engines and placing them in the network. The Controller also scales the Service Engines based on the configured threshold.
For more information, see Installing NSX Advanced Load Balancer in VMware vSphere Environments.
The BGP peering and virtual service configuration remains the same as mentioned in the Network Policy Mode with NSX Advanced Load Balancer on No Access or Read Access VMware Cloud.
A port group with a static VLAN needs to exist in vCenter for the Service Engine Data vNICs. Use the SVI interface with static VLAN as L3out in the ACI fabric.
Monitoring
NSX Advanced Load Balancer Controller provides real-time analytics dashboards that provide application load balancing and security analytics in a single frame.
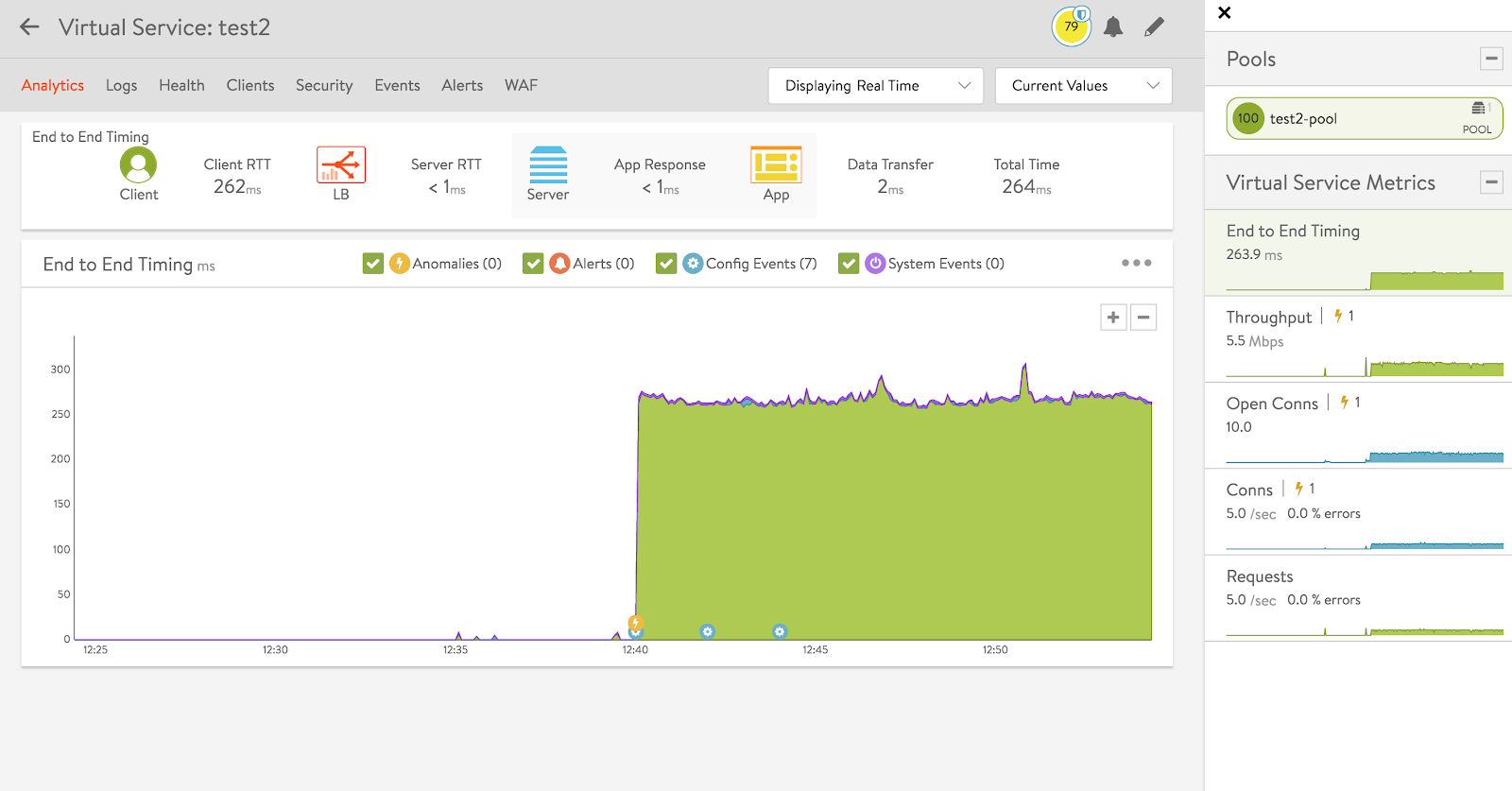
NSX Advanced Load Balancer virtual service real-time metrics provide details relating to transactions per second, delay, response times, etc.
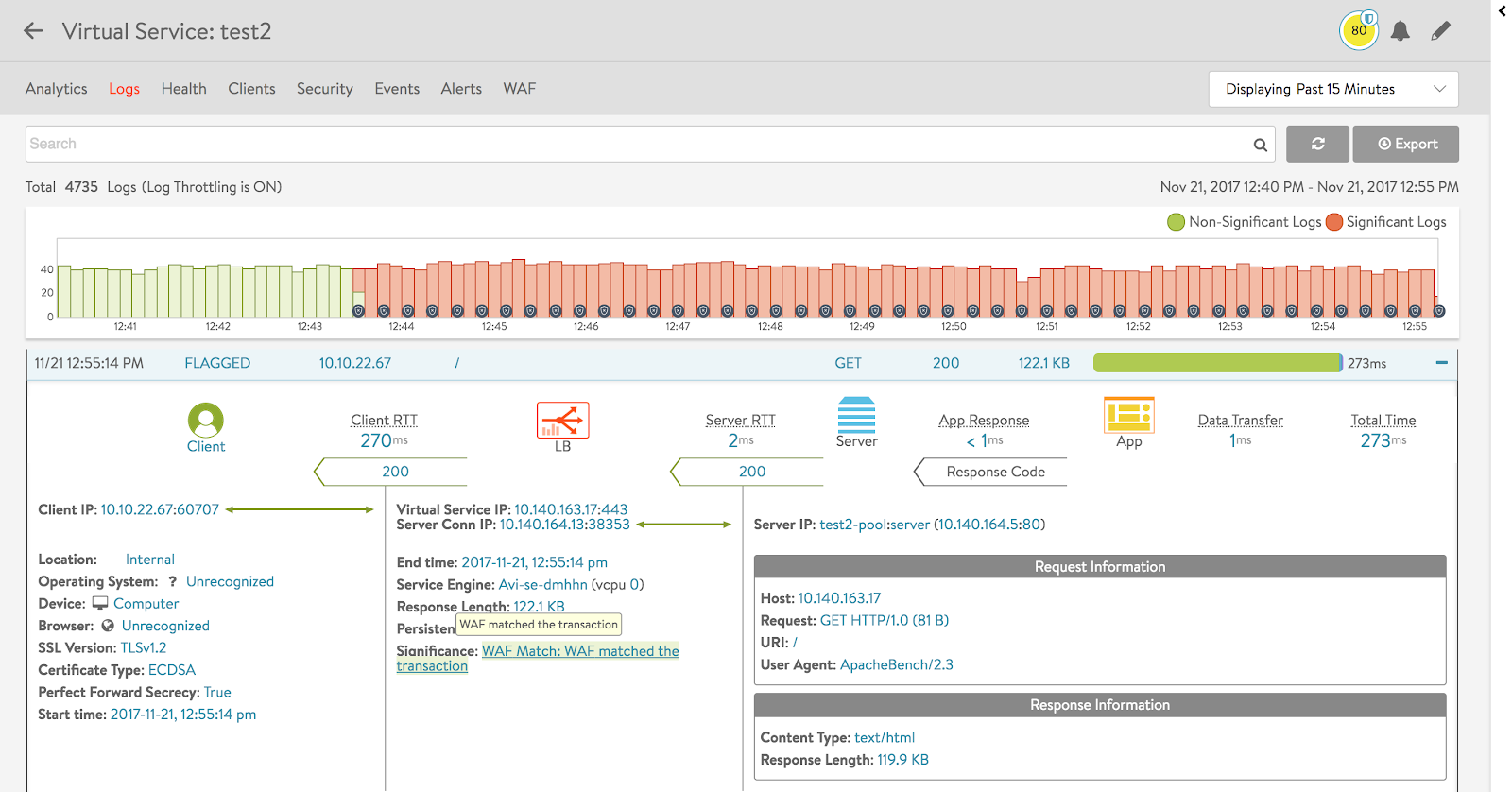
NSX Advanced Load Balancer logs provide a detailed view of each connection, as in the displayed case, where the client/virtual service/server end-to-end communication is displayed, which is used for troubleshooting.
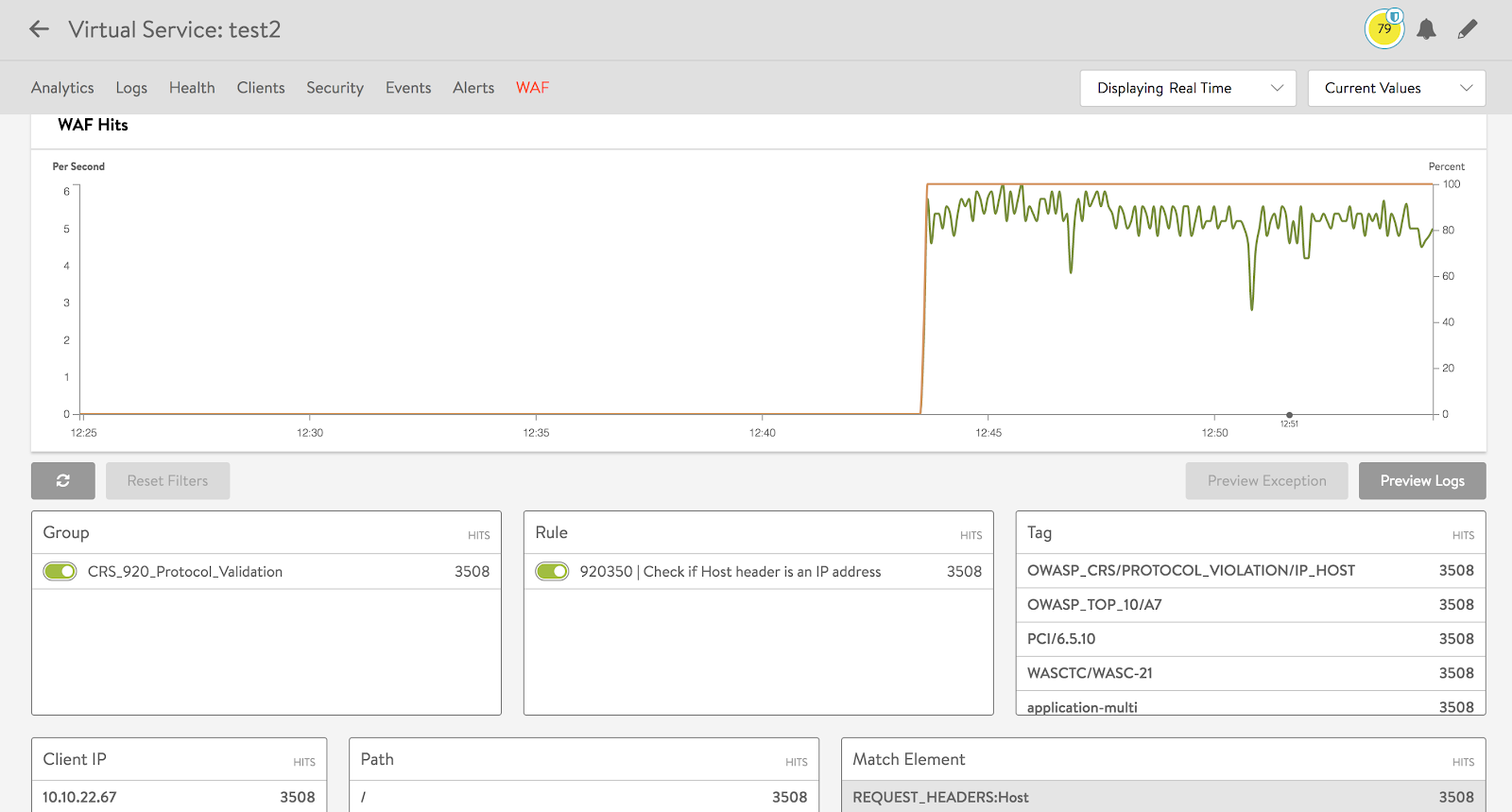
NSX Advanced Load Balancer WAF analytics provides information on real-time web security attacks on the virtual service.
The NSX Advanced Load Balancer Controller offers the following monitoring capabilities for Cisco ACI fabric:
Monitors Load Balancer (SE) and application server health.
Provides real-time application analytics.
Protects applications against L4-L7 DDoS attacks.
Monitors APIC EPG membership to automatically add or remove application instances from pools.
Performs Load Balancer auto-scaling based on real-time performance metrics (CPU, memory, bandwidth, connections, latency, etc).
Provides point-and-click simplicity for iWAF policies with central control.
Provides granular security insights on traffic flows and rule matches to enable precise policies using iWAF.