This section discusses the AWS User Cross-Account AssumeRole options available as the credential method for NSX Advanced Load Balancer deployment with AWS.
NSX Advanced Load Balancer supports deployment of Amazon Web Services (AWS) with multiple AWS accounts utilizing the IAM AssumeRole functionality.
IAM roles provide access across AWS accounts to the AWS resources/API from the respective accounts, instead of sharing user Access Key ID and Secret Access Key from different accounts.
While creating the AWS cloud-type, new option of Use Cross-Account AssumeRole is available on the NSX Advanced Load Balancer. The Use Cross-Account AssumeRole feature can be enabled if the AWS cloud needs to be created in an AWS account other than the one that hosts the Controller.
Use Case of Cross-Account Assume Role
Consider a hypothetical organization XYZ Corp with multiple AWS account IDs: IT – 123456789012 Prod – 112233445566.
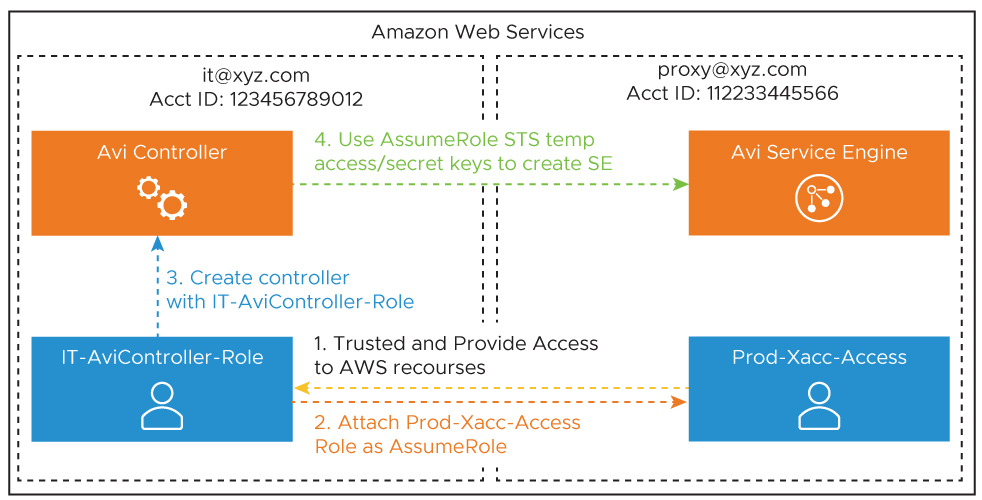
In a general deployment, the XYZ Corp would require an Access Key ID and Secret Access Key to create NSX Advanced Load Balancer Service Engine cloud in AWS for each account. Sharing the AWS access keys for respective accounts would be a security concern with this.
In addition to this, it would be cumbersome to track all the keys and update them. Instead AWS IAM Roles can be used in every account. The IAM roles feature provides access to the AWS resources or API access across AWS accounts.