This section explains the AWS IPAM feature available while integrating NSX Advanced Load Balancer with AWS.
NSX Advanced Load Balancer integrates with Amazon Web Services (AWS) for providing IPAM services to applications running on instances in AWS.
If the cloud type is AWS, there is support for IPAM, by default, without the need for a separate IPAM configuration.
A separate IPAM configuration (as described below) is required only for cases where AWS provides the infrastructure service for other clouds, for instance, Mesos Cluster running on AWS instances.
AWS IPAM is supported only for North-South IPAM provider.
You need one of the following credentials for implementing AWS as the IPAM provider:
Identity and Access Management (IAM) roles
AWS customer account key
AWS IPAM Configuration Using IAM Role
If using the IAM role method to define access for NSX Advanced Load Balancer installation in AWS, use these steps to set up the IAM roles before beginning deployment of the Controller EC2 instance:
Navigate to .
-
Select AWS IPAM as type and Use IAM Roles as shown below:
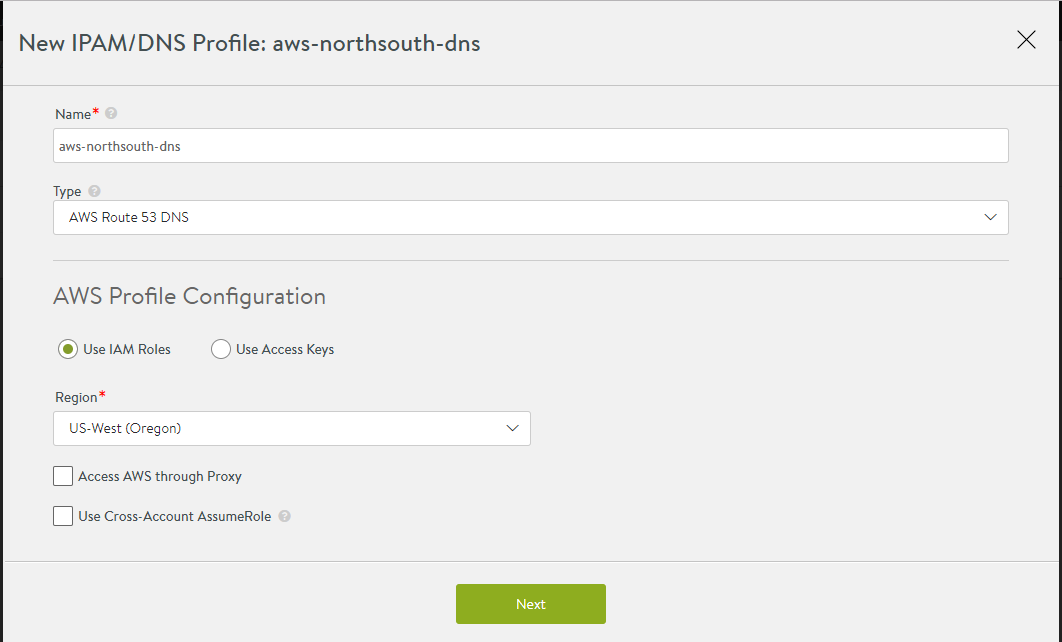
Click Next to configure VPCs.
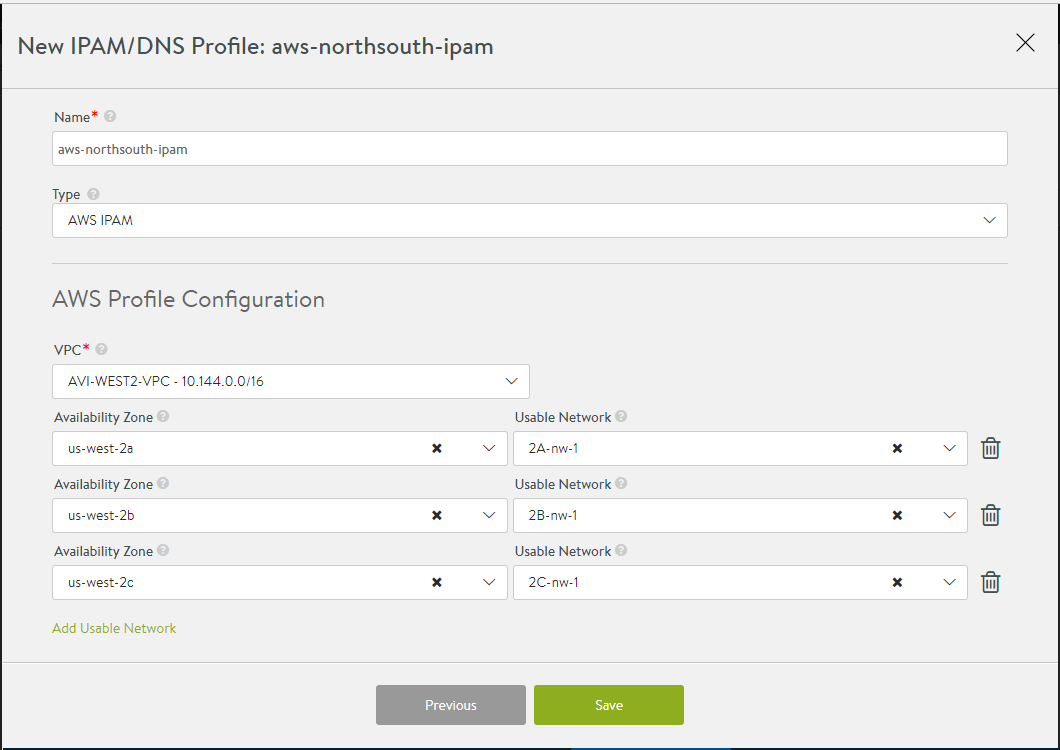
A drop-down of available VPCs in that region is displayed.
Select the appropriate VPC.
A drop-down of availability zones (AZ) in that region and a corresponding list of networks in each AZ is displayed. For multi-AZ virtual service applications, configure at least one network from each AZ for IPAM.
Click Save.
AWS IPAM Configuration Using Access Key
To configure AWS IPAM using Access Key,
Navigate to .
select AWS IPAM as the Type, then select Use Access Keys and enter the following information:
Access Key ID: AWS customer key ID
Secret Access Key: customer key
Select the AWS region into which the VIPs will be deployed
Select Access AWS through Proxy, if access to AWS endpoints requires a proxy server.
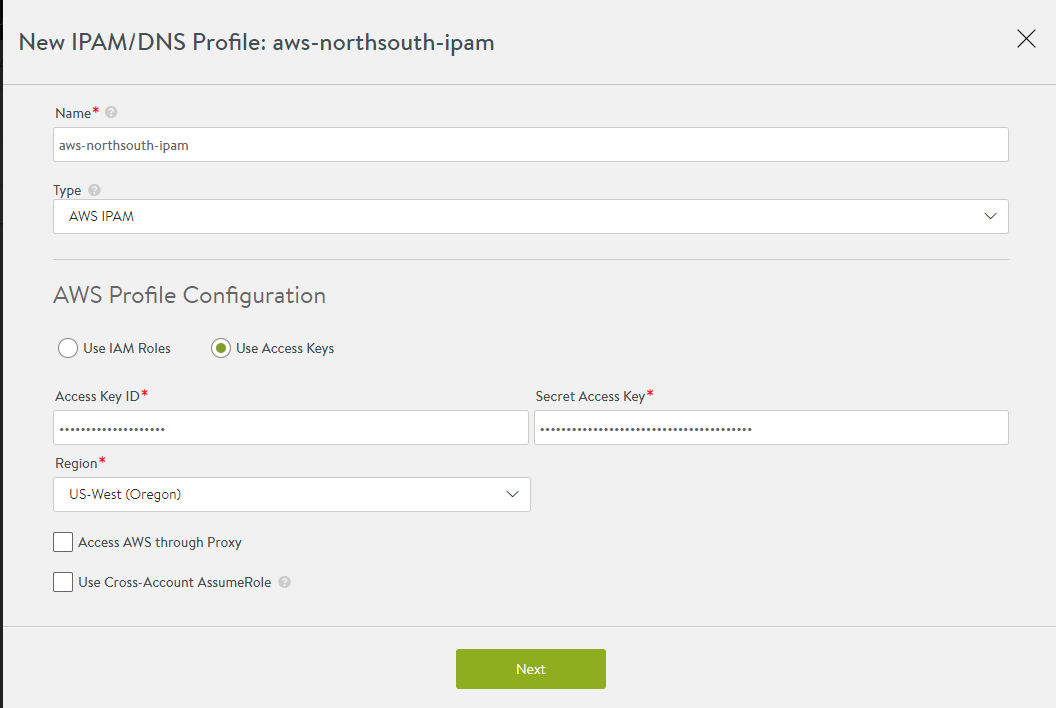
Select Use Cross-Account AssumeRole, if the AWS credentials or role is being leveraged to access across accounts. Click Next to configure VPCs.
A drop-down of available VPCs in that region is displayed.
Select the appropriate VPC.
A drop-down of availability zones (AZ) in that region and a corresponding list of networks in each AZ is displayed. For multi-AZ virtual service applications, configure at least one network from each AZ for IPAM.
Click Save.
