In addition to the default legacy format, the NSX Advanced Load Balancer supports two other Syslog formats. This topic only applies to the formatting of the alerts sent out as Syslog messages from the Controller. It does not impact the formatting of the application logs or client logs directly streamed from the SEs.
Use the format option under alertsyslogconfig command to set the syslog format parameter. The following are the supported formats:
SYSLOG_LEGACYSYSLOG_RFC5424SYSLOG_JSONSYSLOG_RFC5425_ENHANCED
Use the format syslog_format command to configure the required format. The following is an example of configuring a syslog format of SYSLOG_JSON.
[admin:10-X-X-X]: > configure alertsyslogconfig Syslog-Test1 [admin:10-X-X-X]: alertsyslogconfig> syslog_servers New object being created [admin:10-X-X-X]: alertsyslogconfig:syslog_servers> syslog_server 10.1.1.1 [admin:10-X-X-X]: alertsyslogconfig:syslog_servers> syslog_server_port 516 [admin:10-X-X-X]: alertsyslogconfig:syslog_servers> format SYSLOG_JSON [admin:10-X-X-X]: alertsyslogconfig:syslog_servers> save [admin:10-X-X-X]: alertsyslogconfig> save +----------------------+--------------------------------------------------------+ | Field | Value | +----------------------+--------------------------------------------------------+ | uuid | alertsyslogconfig-d6d24aa4-085d-4204-8cd4-3ff24d7242a4 | | name | Syslog-Test1 | | syslog_servers[1] | | | syslog_server | 10.1.1.1 | | syslog_server_port | 516 | | udp | False | | format | SYSLOG_JSON | | tenant_ref | admin | +----------------------+--------------------------------------------------------+
Use the show alertsyslogconfig command to confirm the format currently set for the Syslog-Test1 object.
[admin:10-10-24-65]: > show alertsyslogconfig Syslog-Test1 +-----------------------------------------------------------------------------+ | Field | Value | +--------------------+--------------------------------------------------------+ | uuid | alertsyslogconfig-d4b2a910-7750-4d20-b5c7-0009816c7300 | | name | Syslog-Test1 | | syslog_servers[1] | | | syslog_server | 10.1.1.1 | | syslog_server_port | 516 | | udp | False | | format | SYSLOG_JSON | | tenant_ref | admin | +-----------------------------------------------------------------------------+
The following are the sample log messages for all the three formats:
SYSLOG_LEGACY
Sep 12 17:29:36 10.X.X.X [2018-09-12 17:29:36,398: Avi-Controller: INFO: ] [default: reason: Syslog for Config Events occured] At 2018-09-12 17:29:33+00:00 event CONFIG_UPDATE occurred on object default in tenant admin as Config update status is success (performed by user admin).`
SYSLOG_RFC5424
Sep 12 17:25:21 2018-09-12 17: 25:21,283 user-ctlr-nsx Avi-Controller - - - INFO [Syslog-Config: reason: Syslog for Config Events occured] At 2018-09-12 17:25:14+00:00 event CONFIG_UPDATE occurred on object Syslog-Config in tenant admin as Config Syslog-Config update status is success (performed by user admin).`
SYSLOG_JSON
Sep 12 17:28:21 2018-09-12 17: 28:21,436 user-ctlr-nsx Avi-Controller - - - INFO [default: reason: Syslog for Config Events occured] {"level": "ALERT_LOW", "timestamp": "2018-09-12 17:28:15", "obj_name": "default", "tenant_uuid": "admin", "summary": "Syslog for Config Events occured", "obj_key": "default", "reason": "threshold_exceeded", "obj_uuid": "default", "related_objects": ["default"], "threshold": 0, "events": [{"obj_type": "SYSTEMCONFIGURATION", "tenant_name": "", "event_id": "CONFIG_UPDATE", "related_uuids": ["default"], "event_details": {"config_update_details": {"status": "Success", "resource_name": "", "old_resource_data": "{\"email_configuration\": {\"disable_tls\": false, \"mail_server_port\": 25, \"mail_server_name\": \"localhost\", \"smtp_type\": \"SMTP_LOCAL_HOST\", \"from_email\": \"[email protected]\"}, \"global_tenant_config\": {\"se_in_provider_context\": true, \"tenant_access_to_provider_se\": true, \"tenant_vrf\": false}, \"uuid\": \"default\", \"dns_configuration\": {\"search_domain\": \"\"}, \"url\": \"https://10.X.X.X/api/systemconfiguration\", \"ssh_hmacs\": [\"[email protected]\", \"[email protected]\", \"[email protected]\", \"hmac-sha2-512\"], \"docker_mode\": false, \"snmp_configuration\": {\"version\": \"SNMP_VER2\", \"large_trap_payload\": false, \"sys_contact\": \"[email protected]\", \"community\": \"<sensitive>\"}, \"portal_configuration\": {\"use_uuid_from_input\": false, \"redirect_to_https\": true, \"sslprofile_ref\": \"https://10.X.X.X/api/sslprofile/sslprofile-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Standard-Portal\", \"disable_remote_cli_shell\": false, \"enable_clickjacking_protection\": true, \"sslkeyandcertificate_refs\": [\"https://10.Y.Y.Y/api/sslkeyandcertificate/sslkeyandcertificate-sslprofile-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Default-Portal-Cert\", \"https://10.X.X.X/api/sslkeyandcertificate/sslkeyandcertificate-sslprofile-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Default-Portal-Cert-EC256\"], \"enable_https\": true, \"allow_basic_authentication\": true, \"password_strength_check\": false, \"enable_http\": true}, \"ntp_configuration\": {\"ntp_servers\": [{\"server\": {\"type\": \"DNS\", \"addr\": \"0.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"1.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"2.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"3.us.pool.ntp.org\"}}]}, \"ssh_ciphers\": [\"aes128-ctr\", \"aes256-ctr\", \"arcfour256\", \"arcfour128\"], \"default_license_tier\": \"ENTERPRISE_18\", \"_last_modified\": \"1536773140367910\"}", "user": "admin", "new_resource_data": "{\"url\": \"https://10.X.X.X/api/systemconfiguration\", \"uuid\": \"default\", \"_last_modified\": \"1536773295406537\", \"email_configuration\": {\"disable_tls\": false, \"mail_server_port\": 25, \"mail_server_name\": \"localhost\", \"smtp_type\": \"SMTP_LOCAL_HOST\", \"from_email\": \"[email protected]\"}, \"global_tenant_config\": {\"se_in_provider_context\": true, \"tenant_access_to_provider_se\": true, \"tenant_vrf\": false}, \"dns_configuration\": {\"search_domain\": \"\"}, \"ssh_hmacs\": [\"[email protected]\", \"[email protected]\", \"[email protected]\", \"hmac-sha2-512\"], \"docker_mode\": false, \"portal_configuration\": {\"use_uuid_from_input\": false, \"redirect_to_https\": true, \"sslprofile_ref\": \"https://10.X.X.X/api/sslprofile/sslprofile-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Standard-Portal\", \"disable_remote_cli_shell\": false, \"enable_clickjacking_protection\": true, \"sslkeyandcertificate_refs\": [\"https://10.X.X.X/api/sslkeyandcertificate/sslkeyandcertificate-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Default-Portal-Cert\", \"https://10.X.X.X/api/sslkeyandcertificate/sslkeyandcertificate-aaaaaaa-bbbb-11cc-22dd-123456789123#System-Default-Portal-Cert-EC256\"], \"enable_https\": true, \"allow_basic_authentication\": true, \"password_strength_check\": false, \"enable_http\": true}, \"ntp_configuration\": {\"ntp_servers\": [{\"server\": {\"type\": \"DNS\", \"addr\": \"0.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"1.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"2.us.pool.ntp.org\"}}, {\"server\": {\"type\": \"DNS\", \"addr\": \"3.us.pool.ntp.org\"}}]}, \"ssh_ciphers\": [\"aes128-ctr\", \"aes256-ctr\", \"arcfour256\", \"arcfour128\"], \"default_license_tier\": \"ENTERPRISE_18\"}", "path": "/api/systemconfiguration/", "resource_type": "SystemConfiguration"}}, "event_description": "Config update status is success (performed by user admin)", "module": "CONFIG", "report_timestamp": "2018-09-12 17:28:15", "internal": "EVENT_EXTERNAL", "event_pages": ["EVENT_PAGE_ALL", "EVENT_PAGE_VS", "EVENT_PAGE_POOL", "EVENT_PAGE_SE", "EVENT_PAGE_AUDIT"], "context": "EVENT_CONTEXT_CONFIG", "obj_name": "default", "obj_uuid": "default", "tenant": "admin"}], "name": "Syslog-Config-Events-default-6600391043391638330-1536773295-19597741"} `
SYSLOG_RFC5425_ENHANCED
In the SYSLOG_RFC5425_ENHANCED mode, the syslog messages emitted from the Controller adhere to the format described in RFC5425. The syslog messages in this mode have the following format:
HEADER STRUCTURED-DATA MSG,
where the header is as described below:
PRI: Represents the facility and severity of the message, PRI = Facility * 8 + Severity.
VERSION: The version number of the syslog protocol standard. Currently this value is 1.
ISOTIMESTAMP: The time when the message was generated in the ISO 8601 format (yyyy-mm-ddThh:mm:ss+-ZONE).
HOSTNAME: The machine that originally sent the message.
Consider the example given below:
Dec 22 09:15:09 10.128.49.7 1 2020-12-22T09:15:09.936Z 10-128-49-7 Avi-Controller - - - INFO [Syslog-Config: reason: Syslog for Config Events occured] At 2020-12-22 09:13:33+00:00 event CONFIG_UPDATE occurred on object Syslog-Config in tenant admin as Config Syslog-Config update status is success (performed by user admin).
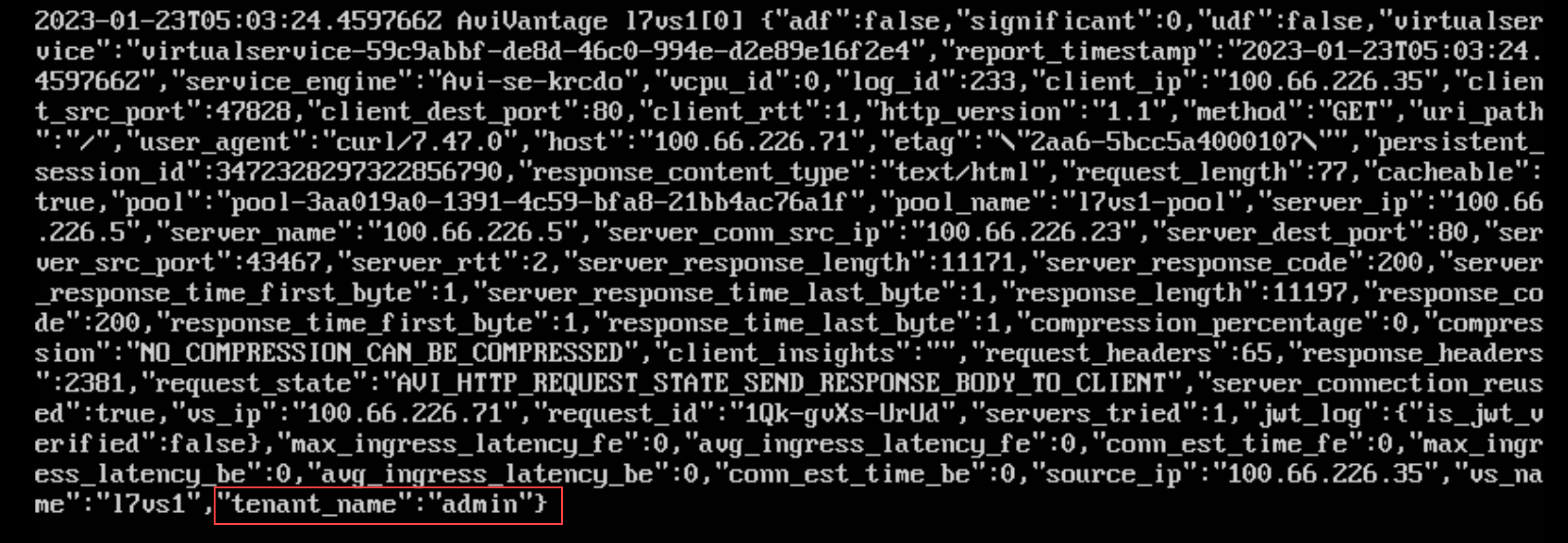
Starting with NSX Advanced Load Balancer 22.1.3, tenant_name is added to the Syslog formats when logs are streamed in an external server.