The NSX Advanced Load Balancer can be used as the load balancer for Unified Access Gateways (UAG), Horizon Connection Servers and App Volume Managers deployed as part of the Horizon solution.
The following methods can be used for load balancing external traffic to UAG:
Deployment Method |
Recommended/ Legacy |
Remarks |
|---|---|---|
Single VIP with Two Virtual Services Using 307 Redirect Solution |
Recommended for the use cases in NAT Environment (Users behind NAT or UAG servers behind NAT) |
This method does not rely on source IP affinity, so it works well in the cases where there are clients behind a single NAT (an edge site) and all connections present the same source IP address. |
Recommended if requirement is to bypass NSX Advanced Load Balancer for secondary protocol |
||
Legacy |
It does not work well in the cases where there are clients behind NAT. |
|
Legacy |
||
Recommended for compliance use cases |
Required for HIPAA/NIST compliance and smart card authentication |
Single VIP with Two Virtual Services Using 307 Redirect
- Description
-
In this design, a single VIP configured on the NSX Advanced Load Balancer load balancer would be used for handling both primary protocols and secondary protocols. The virtual IP (VIP) will be listening on HTTPS:443 and on the required TCP/UDP ports for secondary protocols.
Load balancer routes secondary protocols to the same UAG appliance as that selected for the primary Horizon protocol using host header set as part of 307 redirect mechanism as discussed here. Since this does not rely on source IP affinity it works well in the cases where there are many clients behind a single NAT (an edge site) and all connections present the same source IP address. This is the recommended design option for UAG load balancing.
For more information, see Single VIP with two Virtual Services (Using 307 Redirect).
- Use Cases
-
All typical L7 deployments
- Advantages
-
Does not require multiple public virtual IP addresses.
Uses L7 virtual service for HTTPS-XML, enabling rich analytics and logs to and from NSX Advanced Load Balancer to provide insights into the connections
Is easy to configure and deploy.
(n+1) VIP Using 307 Redirect Solution
This method dedicates an individual virtual IP (VIP) to each appliance in addition to the primary load balanced NSX Advanced Load Balancer VIP. Only the initial request goes through NSX Advanced Load Balancer there are two UAG appliances, then three VIPs would be required. The primary Horizon protocol on HTTPS port 443 is load balanced on NSX Advanced Load Balancer to allocate the session to a specific UAG appliance, based on the health and the load.The secondary protocols can bypass the load balancers and go directly to the UAG. The blast and PCoIP External URLs must be configured to point to itself on each UAG In such deployments, only a single VIP for primary protocol is required.
For more information, see Load Balancing for Horizon Environments in (n+1) Mode using 307 Solution.
- Advantage
-
Does not rely on source IP affinity.
- Caveat
-
Requires an additional public-facing IP for each UAG appliance, in addition to the primary load balanced VIP.
Single VIP with Two Virtual Services
In this design, a single VIP configured on the NSX Advanced Load Balancer load balancer would be used for handling both primary protocols and secondary protocols. The virtual IP (VIP) will be listening on HTTPS:443 and on the required TCP/UDP ports for secondary protocols.
Load balancer routes secondary protocols to the same UAG appliance as that selected for the primary Horizon protocol using the Source IP affinity.
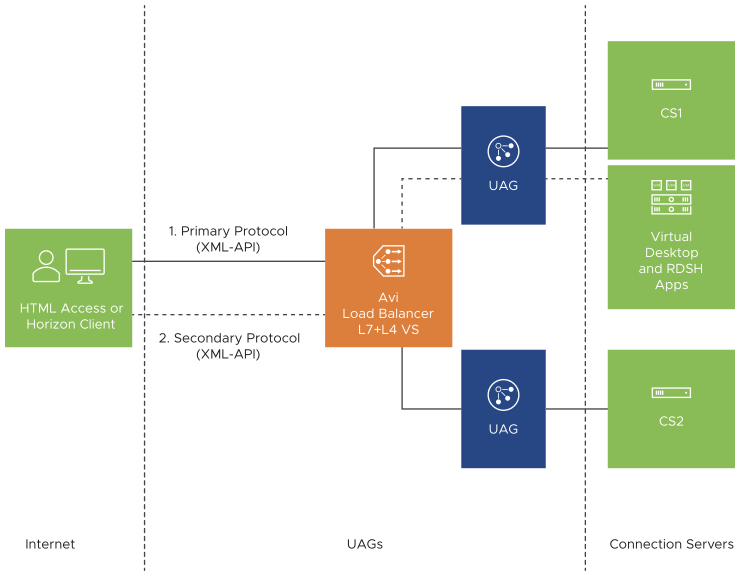
If Source IP affinity is not the optimum choice for your environment, refer to the other methods of deployment as applicable.
The tunnel external URL, blast external URL and the PCoIP (PC over IP) external URL must be configured to the load balancer VIP/Fully Qualified Domain Name (FQDN) on the UAG.
- Caveat
-
Relies on source IP address affinity which might not always be possible. Source IP affinity does not work where there are many clients behind a single NAT (an edge site) and all connections present the same source IP address.
- Advantages
-
Does not require multiple public virtual IP addresses
Uses L7 virtual service for HTTPS-XML, enabling rich analytics and logs to and from NSX Advanced Load Balancer to provide insights into the connections
Is easy to configure and deploy
Using L7 for HTTPS XML and the tunnel enables the user to get rich analytics and logs to and from NSX Advanced Load Balancer to provide insights into the connections.
Single L4 Virtual Service
This configuration option uses a single Virtual IP (VIP) and the load balancing is done at the TCP or UDP level.
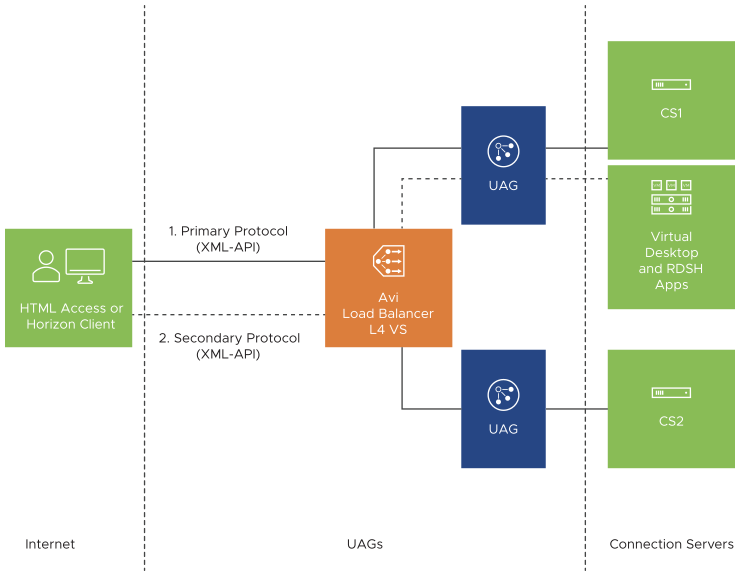
- Use Cases
-
If smart card authentication is required, where the client cert is passed directly from the client to UAG using TLS and there cannot be an intermediate TLS terminator
Where HIPAA or NIST compliance is needed. This deployment will be HIPAA or NIST compliant as the UAG terminates SSL
Where a single public VIP and standard port numbers are required as we can have source IP affinity between primary and secondary protocols
- Advantages
-
Does not require multiple public VIP addresses
Easy to configure and deploy
- Caveats
-
Rich analytics into the HTTPS-XML primary protocol will not be available on NSX Advanced Load Balancer
Relies on source IP address affinity which might not always be possible. Source IP affinity does not work where there are many clients behind a single NAT (an edge site) and all connections present the same source IP address
(n+1) VIP
If source IP affinity is not the desired option for an environment such as Horizon deployed on an edge site behind a single network address translated IP, then this approach could be used for load balancing Unified Access Gateway (UAG) with NSX Advanced Load Balancer.
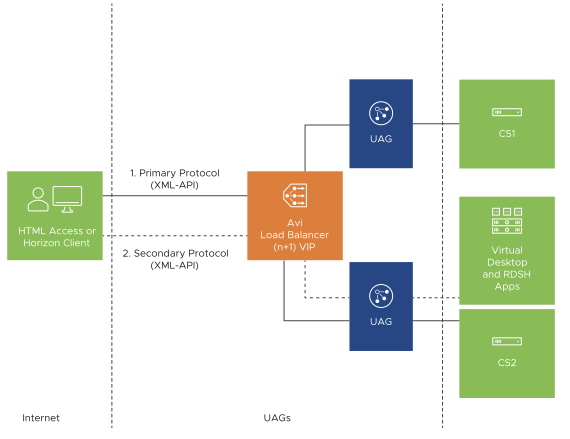
This method dedicates an individual virtual IP (VIP) to each appliance in addition to the primary load balanced NSX Advanced Load Balancer VIP. If there are two UAG appliances, then three VIPs would be required.
The primary Horizon protocol on HTTPS port 443 is load balanced on NSX Advanced Load Balancer to allocate the session to a specific UAG appliance, based on the health and the load.
The tunnel external URL, blast external URL and the PCoIP external URL must be configured to the respective UAG IP as the UAG directly receives the traffic bypassing the load balancer.
- Advantages
-
Does not rely on source IP affinity
Uses standard port numbers
- Caveats
-
Requires an additional public-facing VIP for each UAG appliance, in addition to the primary load balanced VIP
Using L7 for HTTPS-XML and the tunnel enables user to get rich analytics and logs to and from NSX Advanced Load Balancer to provide insights into the connections
The secondary protocols can bypass the load balancers and go directly to the UAG. The blast and PCoIP External URLs must be configured to point to itself on each UAG.
In such deployments, only a single VIP for primary protocol is required.