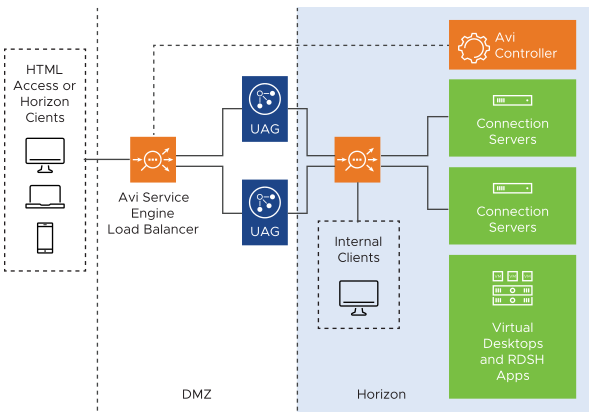
In a deployment with multiple connection servers, NSX Advanced Load Balancer can be used to load balance traffic to the connection servers as well.
The traffic can reach the connection server in the following ways:
For external clients, the traffic reaches connection servers through UAG.
For internal clients, the traffic reaches the connection servers directly.
On using SmartCard or SecureID with True SSO or RADIUS with TrueSSO as the authentication method, the UAG must communicate directly with connection servers without any load balancers in between.
External Clients Traffic
Horizon traffic from external clients on the internet first lands on UAG through the load balancer. The primary protocol traffic is sent to the connection server and the secondary protocols are sent directly to the virtual desktops or RDS hosts.

An L7 virtual service for port 443 with connection servers as the pool members can be configured with consistent hash with source IP as load balancing algorithm to ensure traffic from same UAG goes to same connection server if required. The NSX Advanced Load Balancer VIP must be entered as the connection server IP on the UAG. The SSL fingerprint configured on UAG would be that of NSX Advanced Load Balancer VIP which is in front of the connection servers.
From external clients through UAG
Horizon traffic from external clients is as shown below:
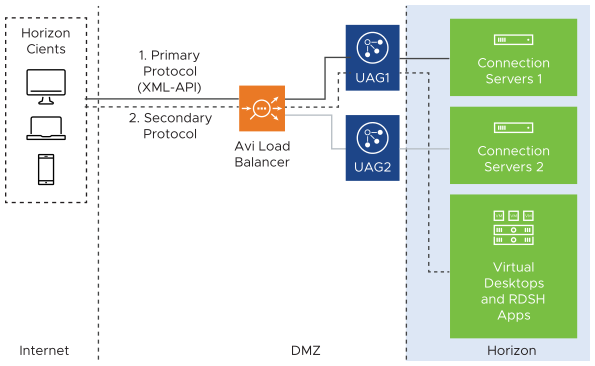
For the listed authentication methods used for Horizon, there must be no load balancers between the UAG and connection servers. The UAG must communicate directly with the connection servers as required for the authentication methods:
Smart card authentication
SecureID with True SSO
RADIUS with True SSO
Internal Client Traffic
NSX Advanced Load Balancer can be deployed in front of Connection Servers for internal clients. Typically, for internal clients, the primary protocol will be load balanced between connection servers while the secondary protocols are routed directly to the virtual desktops or RDS hosts, bypassing the load balancer.
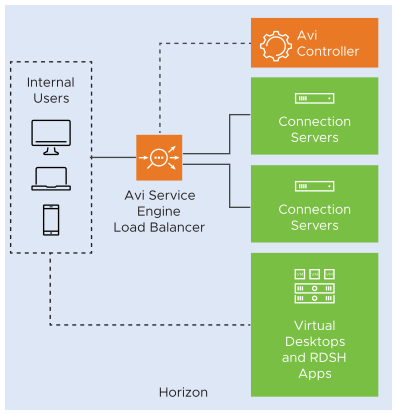
The same virtual service can be used for load balancing both internal and external clients to the connection servers as shown below: