The rules that match, add up to a request-based threshold. If the threshold is reached, the request is blocked. This topic explains the configuration and modification of multiple threshold limits.
Within the Service Engine, by default, multiple thresholds are set and can be changed.
Default thresholds setvar:tx.sql_injection_score_threshold=15, setvar:tx.xss_score_threshold=15, setvar:tx.rfi_score_threshold=5, setvar:tx.lfi_score_threshold=5, setvar:tx.rce_score_threshold=5, setvar:tx.command_injection_score_threshold=5, setvar:tx.php_injection_score_threshold=5, setvar:tx.http_violation_score_threshold=5, setvar:tx.trojan_score_threshold=5, setvar:tx.session_fixation_score_threshold=5, setvar:tx.inbound_anomaly_score_threshold=5, setvar:tx.outbound_anomaly_score_threshold=4
The most frequently used threshold is inbound_anomaly_score_threshold, which is used to deny in the default CRS rule 949110 - inbound anomaly score.
setvar:tx.critical_anomaly_score=5, setvar:tx.error_anomaly_score=4, setvar:tx.warning_anomaly_score=3, setvar:tx.notice_anomaly_score=2"
When the WAF Policy is executed, rules that match will add to the specific thresholds.
For example: 931120. Check for RFI (3/4).
setvar:tx.anomaly_score=+%{tx.critical_anomaly_score}
setvar:tx.rfi_score=+%{tx.critical_anomaly_score}
When all rules are evaluated, the rule 949110 - inbound anomaly score will check the threshold tx.anomaly_score and trigger and deny if it was reached.
SecRule TX:ANOMALY_SCORE "@ge %{tx.inbound_anomaly_score_threshold}" "msg:'Inbound Anomaly Score Exceeded (Total Score: %{TX.ANOMALY_SCORE})', severity:CRITICAL, phase:request, id:949110, t:none, deny, log, tag:'application-multi', tag:'language-multi', tag:'platform-multi', tag:'attack-generic', setvar:tx.inbound_tx_msg=%{tx.msg}, setvar:tx.inbound_anomaly_score=%{tx.anomaly_score}"
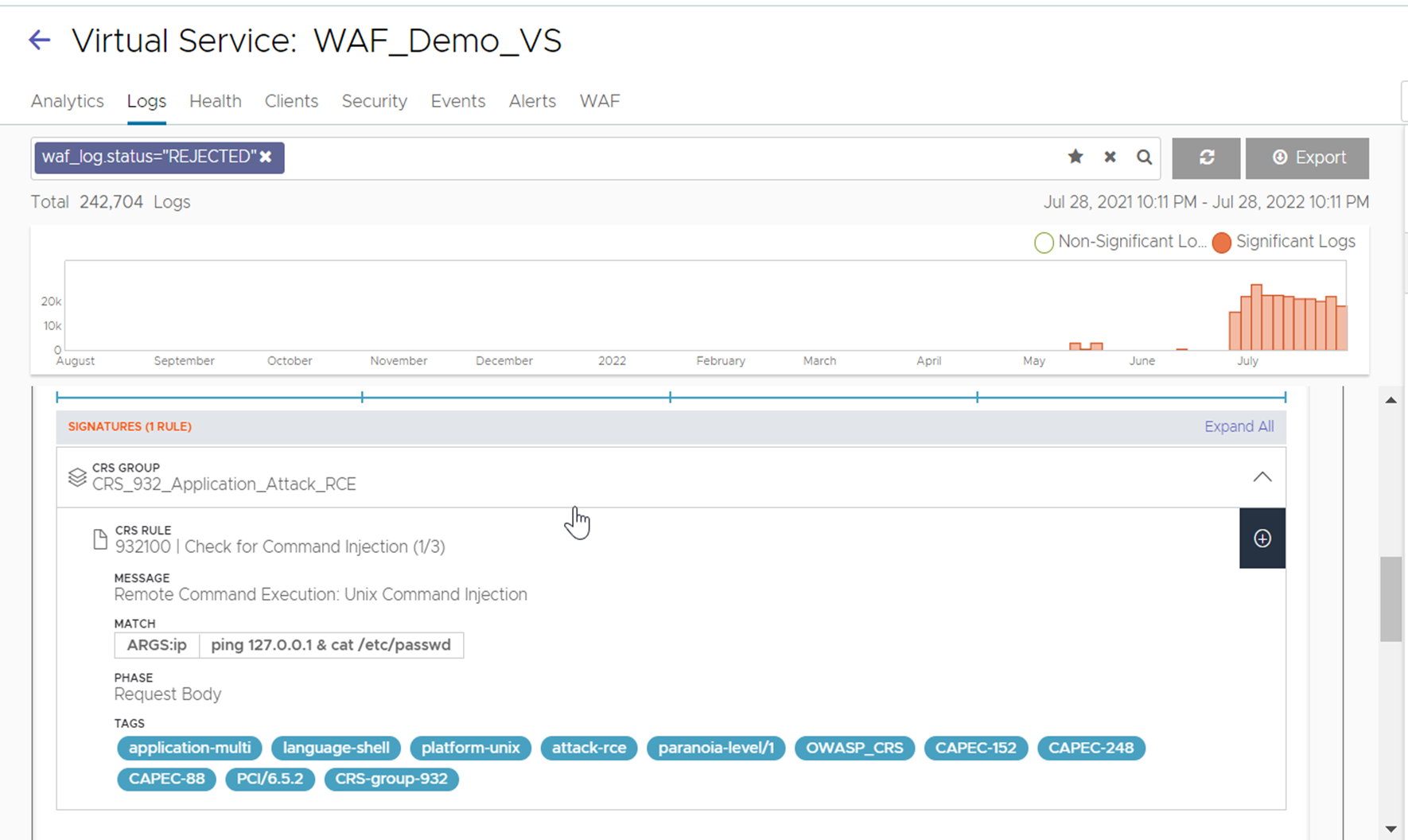
A log file entry is created.
To view the log:
Navigate to .
Click the virtual service mapped to the WAF Policy.
Click Logs.
Expand a Log entry and view the Signature CRS Rules.