This section explains the configuration, common deployment, and use case scenarios of the wildcard VIP.
In NSX Advanced Load Balancer, a virtual service is configured with an IP address as VIP and ports as services to load balance the client traffic from the external world. NSX Advanced Load Balancer processes the client connection or request against a list of settings, policies, and profiles, then load balances valid client traffic to a back-end application server listed as a pool member of the virtual service.
In addition to load balancing the client traffic to the application servers, NSX Advanced Load Balancer also provides supportability, manageability, and scalability to the application servers.
You can upgrade application servers with zero downtime when deployed with the NSX Advanced Load Balancer.
Wildcard VIP extends the capability of a virtual service to provide advanced load balancing services to network elements like firewalls and firewall devices.
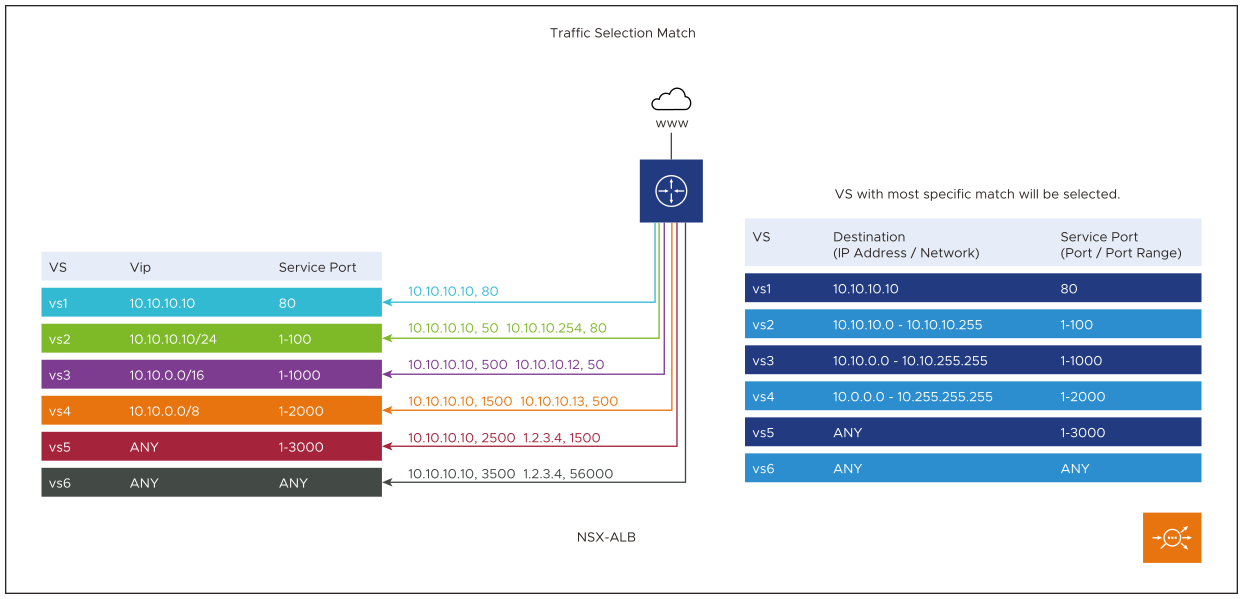
Wildcard VIP allows the network match configuration in a virtual service. The application virtual service accepts the connections destined to a VIP, whereas the wildcard VIP accepts the connections destined to a subnet and is configurable as CIDR notation.
Features Supported
The following profiles support wildcard virtual services:
Application Profile: System L4 application profile preserve_dest_port set only.
Supported Environments
The following environments support wildcard VIP:
Active/ Standby SE group, in a DPDK based environment
No access mode and LSC cloud
Public clouds do not support wildcard VIP, irrespective of dpdk-enabled environment.
Network Address Match
Network traffic match is configured to handle a huge range of incoming traffic. In a corporate network, it can be a subnet/ prefix configuration.
For example, it could be a prefix of 10.0.0.0/8 (to accept between 10.0.0.0 - 10.255.255.255) or 0.0.0.0/0 (to accept every incoming packet).
The following is a demonstration of wildcard VIP in deployment:
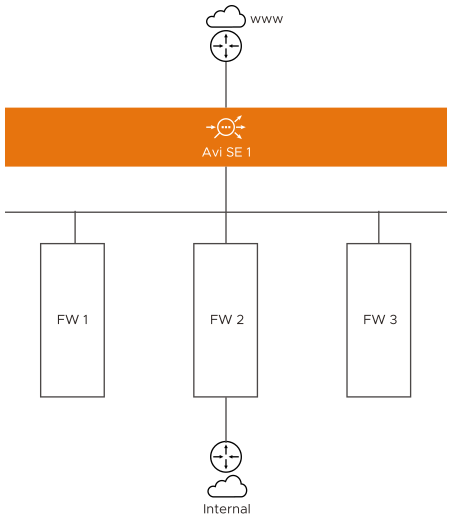
In this deployment mode, the wildcard virtual service is in the frontend, facing the client traffic. Three firewalls: FW1, FW2, and FW3 are configured as pool members. The wildcard virtual service load balances the traffic across the firewalls FW1, FW2, and FW3.
Firewalls are rarely the destination for the client traffic, and the traffic is expected to be transparently forwarded to the firewall. Hence, the traffic from the client must be sent as is to the pool member without any source address or a destination address translation (SNAT or DNAT) In such a deployment, the network address match is configured in the traffic selection criteria of the VIP. The wildcard VIP of the virtual service will only load balance the traffic to these firewalls without changing the client traffic.
Traffic Selection Criteria
With the introduction of network address match as part of the virtual service, the following combinations can be configured as the traffic selectors for the VIP:
Destination |
Service Port |
Virtual Service Configuration |
|---|---|---|
IP Address |
Port |
|
IP Address |
Any |
Service Port is in the range 1 - 65535 |
Network Address |
Port |
Prefix in ip_address (VIP) |
Network Address |
Any |
Prefix in ip_address, Service Port: 0 |
Any |
Port |
Prefix 0 in ip_address |
Any |
Any |
Prefix 0 in ip_address, Service Port 0 |
Currently only TCP/ UDP fast network profiles support Wildcard VIP.
In addition to the network port supported, with the network address match feature, you can configure all the aforesaid variants of the wildcard virtual service. If you configure multiple virtual services with varying combinations as specified in the table, the virtual service with the most specific match is selected in the same order of preference as listed in the table.