This section discusses the steps to configure the Client SSL Certificate Validation using the NSX Advanced Load Balancer UI and CLI.
UI Configuration
The following are the steps to set the Client SSL Certificate Validation option:
Navigate to .
Edit a pre-existing profile or click Create to define new profile.
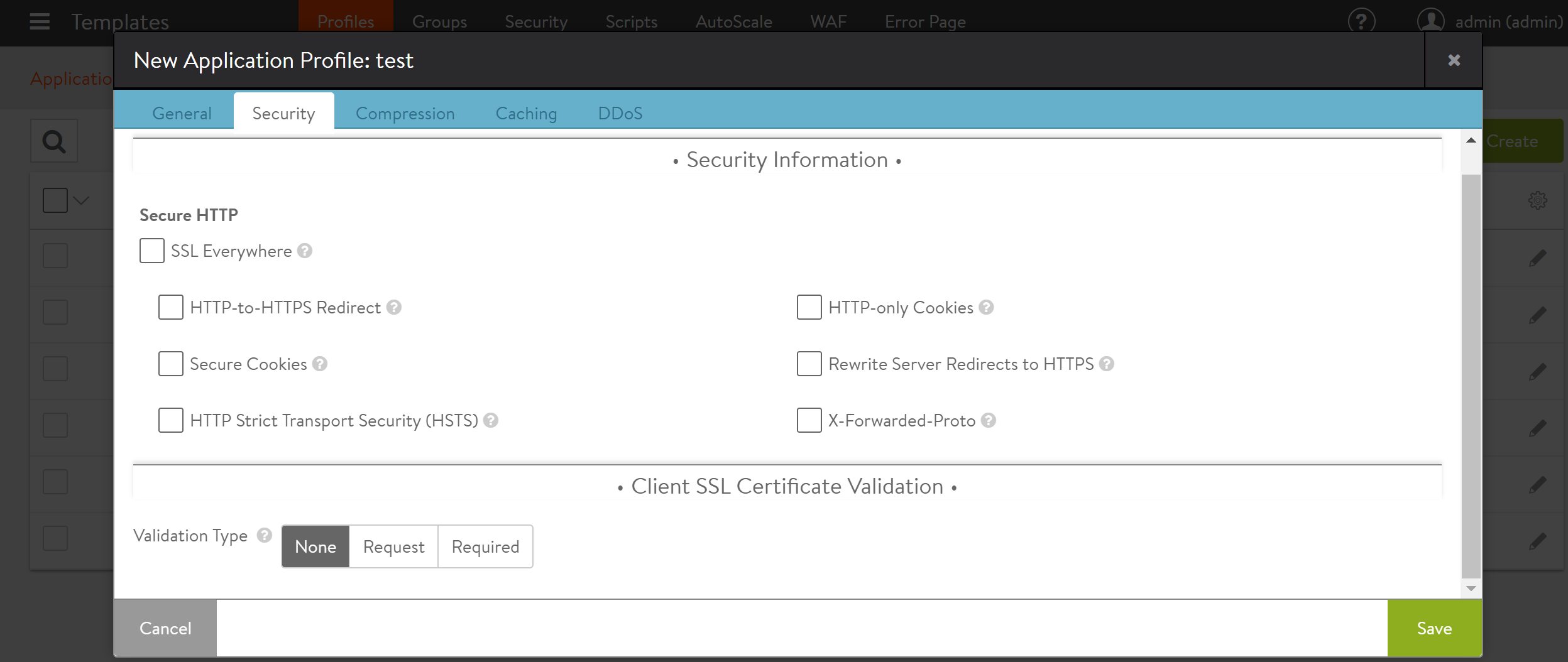
Click the Security tab available under the Security section while creating a new application profile.
The following are the Validation Type choices defined for client certificate verification:
None — Client certificate verification is not to be performed by NSX Advanced Load Balancer. This is the default value.
Request — NSX Advanced Load Balancer will request client certificates for verification, but it is not mandatory that the client provides them.
Required — Client certificates must be presented for verification.
CLI Configuration
The NSX Advanced Load Balancer CLI refers to the above-mentioned choices as modes. After the configure shell command one of three sub-commands is used:
[admin:10-130-180-138]: > configure applicationprofile my-profile [admin:10-130-180-138]: applicationprofile:http_profile> ssl_client_certificate_mode ssl_client_certificate_none [admin:10-130-180-138]: applicationprofile:http_profile> ssl_client_certificate_mode ssl_client_certificate_request [admin:10-130-180-138]: applicationprofile:http_profile> ssl_client_certificate_mode ssl_client_certificate_require
For an SSL communication through NSX Advanced Load Balancer using client certificate authentication, the client certificate is presented during the initial SSL handshake. This certificate is validated by NSX Advanced Load Balancer Controller in Request and Require modes.
If the SSL handshake is completed successfully, the validation type is set as Request, and a certificate is not presented by the client, the connection is established. However, if a client presents a certificate that is not valid for any of the reasons mentioned in the diagnostics section mentioned in the Linux Page, NSX Advanced Load Balancer sends an HTTP 400 response back immediately, even if the SSL handshake completes.
The allow_invalid_client_cert configuration option is supported to enable the processing of invalid client certificates.
Configure this function within a virtual service as shown below:
[admin:10-130-180-138]: > configure virtualservice *virtualservicename* [admin:10-130-180-138]: virtualservice> allow_invalid_client_cert
The default value is False, which means the request is not processed if the client presents an invalid certificate. If the value of the allow_invalid_client_cert flag is set as True, the responsibility to handle the invalid certificate scenario rests on you. You can use the avi.ssl.check_client_cert_validity() function to terminate the request or close the connection.
It is recommended to take action based on the specific errors even though the invalid certificate is allowed through NSX Advanced Load Balancer.
DataScript Function for Client Cert Validation
For more information, see the DataScript Function for Client Cert Validation topic in the VMwareNSX Advanced Load BalancerDataScript Guide.