Online certificate status protocol (OCSP) stapling is an extension of the OCSP protocol. The validity of SSL/ TLS certificates can be checked using OCSP stapling. This section discusses OCSP Stapling in detail.
An SSL certificate can be revoked by the certificate authority (CA) before the scheduled expiration date. This implies that the certificate can no longer be trusted. This process of invalidating an issued SSL certification before expiry of the certificate validity is called certificate revocation.
It is critical for browsers and clients to detect if a certificate has been revoked and suggest a security warning. Certificate revocations are checked either using the Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP).
A CRL is a large list of certificates that have been revoked by the CA. When a client sends a request for an SSL connection to a virtual service, the NSX Advanced Load Balancer checks the CAs and CRL(s) in the PKI profile of the virtual service to verify whether the client certificate is still valid.
Downloading and updating the long list of serial numbers that have been revoked can be cumbersome. In the OCSP method, the client queries the status of a single certificate, instead of downloading and parsing an entire list. This results in lesser overhead on the client and network. Since OCSP requests are sent for each certificate, it can be an overhead for the OCSP responder, in case of high traffic.
OCSP Stapling
The RFC 2560 describes OCSP stapling, a new method for checking revoked certificates. In this method, when a certificate has to be verified, the browser issues an OCSP request with the serial number of the certificate to the OCSP responder. The OCSP responder looks up the CA database using the serial number and fetches the revocation status of the certificate corresponding to the serial number. It returns the revocation status of the certificate through a signed OCSP response.
The client does not have to communicate with the CA server each time to get the certificate status. The NSX Advanced Load Balancer retrieves the information and serves it to the client, on receiving a request.
In NSX Advanced Load Balancer, OCSP stapling can be enabled only on the Application certificates and the Root/ Intermediate certificates. For response, the OCSP response of only the Application certificate is stapled to the certificate in TLS/ SSL handshake. OCSP Stapling can be enabled and configured through the NSX Advanced Load Balancer UI and CLI.
Parameters in OCSP Stapling
This section introduces the parameters that can be configured to use the OCSP stapling feature in NSX Advanced Load Balancer.
Time Parameters
UI Field |
CLI Label |
Description |
|---|---|---|
Frequency Interval |
ocsp_req_interval |
Define the time interval between OCSP requests. |
Response Timeout |
ocsp_resp_timeout |
Define the time interval for which the Controller waits for the response from the CA. If there is no response from the responder, the failover mechanism is initiated. |
Fail Job Interval |
ocsp_job_fail_interval |
Use this option to schedule OCSP job at smaller intervals, when there is no response received within the Response (ocsp_req_interval) timeout. |
Max Tries |
max_tries |
Maximum number of times the failed OCSP jobs can be scheduled. |
Responder URL Action
In the absence of a response from the OCSP server, a failover mechanism is initiated. One of the following URL actions can be selected as a URL action.
UI Field |
Description |
|---|---|
Failover |
Select this method to strictly use user-configured URLs (responder_url_lists) instead of the CA configured URLs. |
Override |
Select this method to strictly use user-configured URLs (responder_url_lists) instead of the CA configured URLs. Select this method to try reaching the URLs found in AIA extension of the certificate first ocsp_responder_url_list_from_certs. If the system is unable to fetch a response, it falls back to the respondent URL list (responder_url_lists). |
If for any reason, the OCSP request cannot be processed, OCSPErrorStatus tracks the status errors to include failures in the OCSP workflow.
Using OCSP Stapling through the UI
OCSP stapling can be enabled through the NSX Advanced Load Balancer UI for Root/ Intermediate CA Certificates and Application Certificates.
OCSP stapling can be enabled only on Root/ Intermediate certificates and Application certificates, and not on controller certificates.
In case of application certificates, OCSP stapling is currently supported in the CSR and import modes. OCSP stapling cannot be enabled for self-signed certificates.
To enable OCSP stapling,
From the NSX Advanced Load Balancer UI, navigate to .
Click .
Enter a Name for the certificate.
Import File or paste the details in the Upload or Paste Certificate File field.
Select Enable OCSP stapling check box to enable the option.
Enter a value between 60-31536000 as the Frequency Interval.
Enter a value in seconds as the Response Timeout.
Enter a value between 60-86400 seconds as the Fail Job Interval.
Enter Max Tries to define the number of times the failed job gets scheduled (with Fail Job Interval). After the maximum number of tries is exhausted, the job gets scheduled with regular OCSP job (Frequency Interval).
Under OCSP Responder URL List, enter the responder URL to do a failover/ override the AIA extension contained in the OCSP responder’s SSL/ TLS certificate.
Choose Failover or Override for Responder URL Action, to either failover or override the AIA extension contained in the SSL/ TLS certificate of the OCSP responder.
Click Add under OCSP Responder URL List.
Select a Responder URL Action. The Add Certificate screen with OCSP Stapling is configured.
Click Validate.
Handling Revoked Certificates
Events or alerts are raised whenever the SSL certificate status changes to Revoked or Issuer Revoked.
If a certificate is revoked, the status of the certificate is marked as Revoked in the NSX Advanced Load Balancer UI.
If a root/ intermediate certificate is revoked, all certificates issued by the revoked root/ intermediate certificate are marked as Issuer Revoked. The Controller stops requesting OCSP certificate status for these certificates.
SSL score of all the certificates with status as Revoked or Issuer Revoked are marked 0.
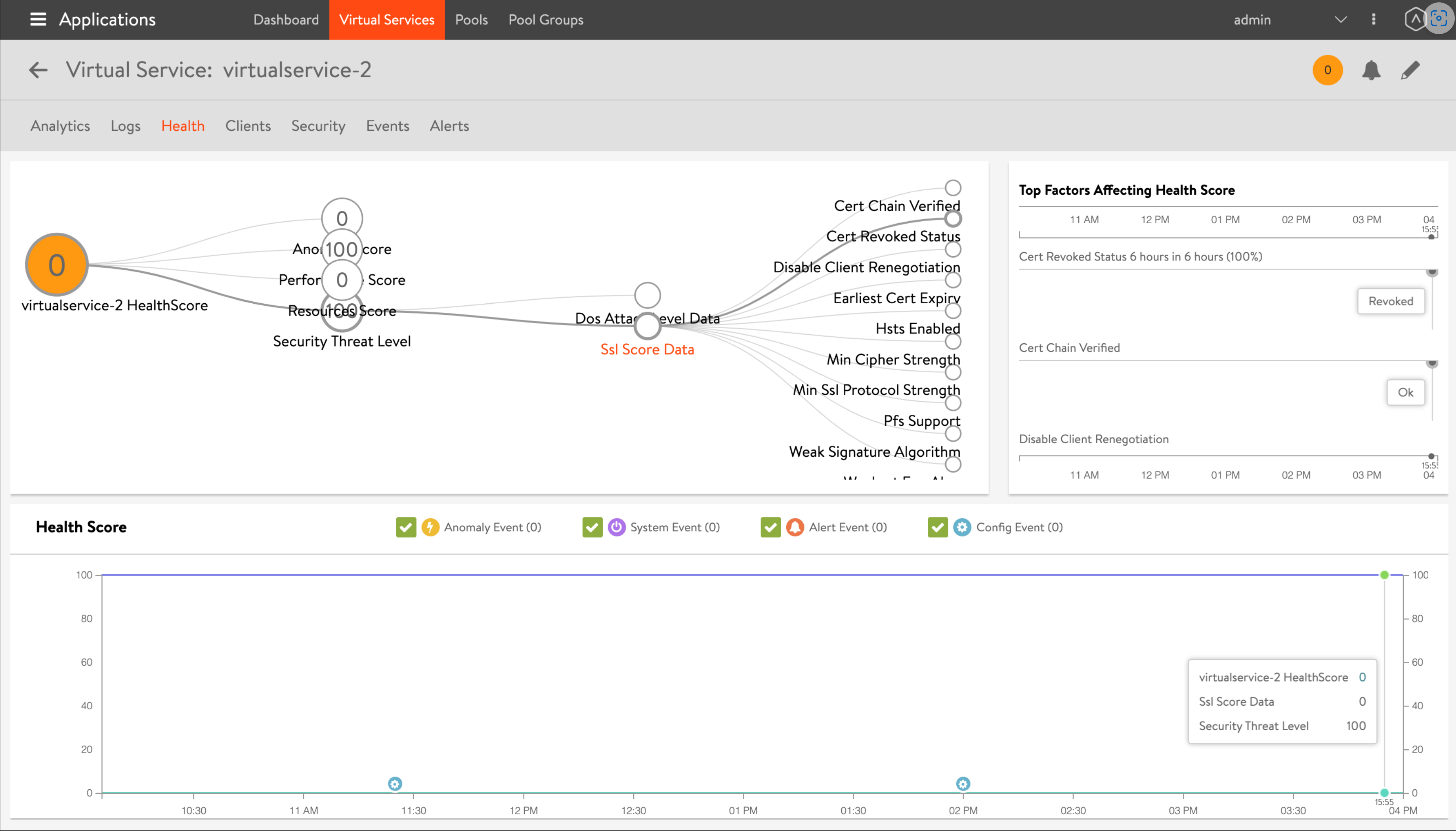
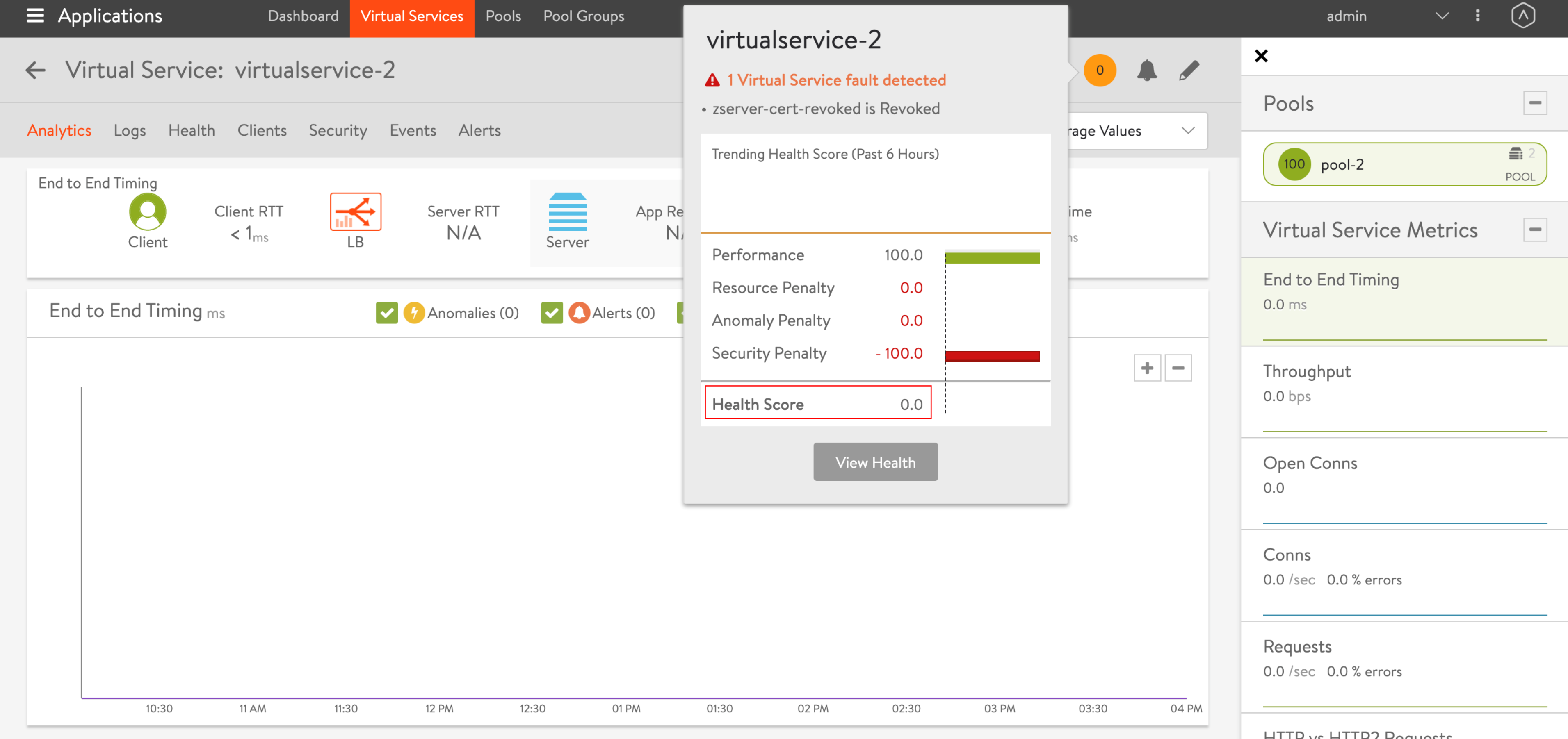
Virtual service faults are added to alert the users when the certificate is either Revoked or Issuer Revoked.
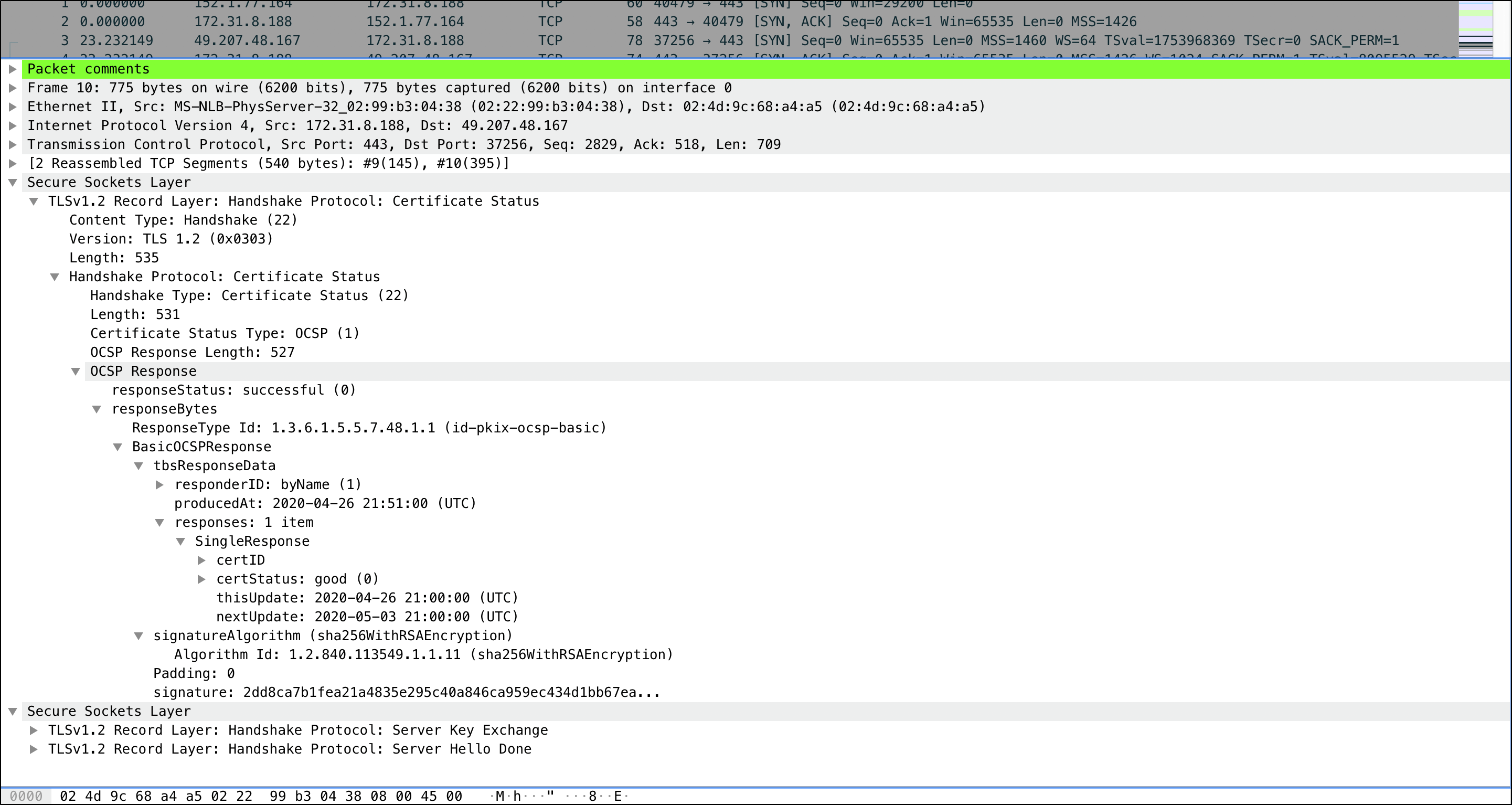
OCSP Stapling during SSL Handshake
When the OCSP response is sent to client, the exchange of stapling information in the SSL handshake is as shown below:
Enabling OCSP Stapling through CLI
OCSP stapling can be configured through the CLI using the enable_ocsp_stapling flag within the certificate object and configured as shown in the following example.
[admin:user-ctrl]: > configure sslkeyandcertificate test-cert [admin:user-ctrl]: sslkeyandcertificate> enable_ocsp_stapling Overwriting the previously entered value for enable_ocsp_stapling [admin:user-ctrl]: sslkeyandcertificate> ocsp_config [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> ocsp_req_interval 21600 Overwriting the previously entered value for ocsp_req_interval [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> ocsp_resp_timeout 60 [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> url_action ocsp_responder_url_ ocsp_responder_url_failover Used as a Failover URL to the AIA extension contained in the certificate. ocsp_responder_url_override URL configured is used instead of the URL contained in the AIA extension of the certificate. [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> url_action ocsp_responder_url_failover [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> responder_url_lists [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> responder_url_lists http://ocsp2.example.com:8080/ [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> failed_ocsp_jobs_retry_interval 30 Overwriting the previously entered value for failed_ocsp_jobs_retry_interval [admin:user-ctrl]: sslkeyandcertificate:ocsp_config> save [admin:user-ctrl]: sslkeyandcertificate> save
The following are the configuration details.
+-------------------------------------------+--------------------------------------------------------------------------------------------------+ | Field | Value | +-------------------------------------------+--------------------------------------------------------------------------------------------------+ | uuid | sslkeyandcertificate-380d9e69-4f04-4519-8151-c89ff2d7bb6f | | name | test-cert | | type | SSL_CERTIFICATE_TYPE_VIRTUALSERVICE | | certificate | | | version | 2 | | serial_number | 15597070261980010830 | | self_signed | True | | issuer | | | common_name | test.example.com | | email_address | [email protected] | | organization_unit | L7 | | organization | abc | | locality | Bangalore | | state | Karnataka | | country | IN | | distinguished_name | C=IN, ST=Karnataka, L=Bangalore, O=VMware, OU=L7, CN=test.example.com, [email protected] | | | | | enable_ocsp_stapling | True | | ocsp_config | | | ocsp_req_interval | 21600 sec | | ocsp_resp_timeout | 60 sec | | responder_url_lists[1]. | http://ocsp.example.com/ | | url_action | OCSP_RESPONDER_URL_FAILOVER | | failed_ocsp_jobs_retry_interval | 30 sec | | tenant_ref | admin | +-------------------------------------------+--------------------------------------------------------------------------------------------------+
If a successful OCSP response is received, the next_update value and the ocsp_req_interval value are compared and the lesser value of the two is used to schedule the next OCSP Request.
Verifying the Certificate Status
If OCSP stapling is enabled for a certificate, the Controller looks for the OCSP URL under the Authority Information Access (AIA) extension, in the certificate, and sends a request to the identified URL. Both GET and POST HTTP methods are supported. The OCSP requests are first sent using the POST method. If there is no response or occurrence of error, the GET method is used.
On receiving the OCSP requests, the CA servers or responders respond with the certificate status. The OCSP responses cannot be forged, as they are directly signed by the CA. The NSX Advanced Load Balancer Controller verifies the signature of the OCSP response. If the response verification fails, the response is dropped and failover mechanisms are triggered to send further requests.
The CA responds with one of the following certificate statuses:
- Good:
-
A positive response is received to the status inquiry. So the certificate with the requested certificate serial number is not revoked within the validity interval.
- Revoked:
-
The certificate has been revoked, either temporarily or permanently.
- Unknown:
-
The responder does not recognize the certificate being requested. This can be because the request indicates an unrecognized issuer, that is not served by this responder.
Navigate to to view the status of SSL/ TLS certificates.
Application Logs
App logs are generated with the following significance.
Certificate Status is Revoked
Certificate status is Issuer Revoked
Certificate Status is Unavailable
OCSP response is stale
To control the significant logs for the above scenarios, configure analytics profile as shown in the following example.
[admin:controller-vmdc2]: > configure analyticsprofile System-Analytics-Profile [admin:controller-vmdc2]: > configure analyticsprofile System-Analytics-Profile Updating an existing object. Currently, the object is: +-------------------------------------------------+-------------------------------------------------------+ | Field | Value | +-------------------------------------------------+-------------------------------------------------------+ | uuid | analyticsprofile-1775513e-bbf5-47ce-a067-42237c91315d | | name | System-Analytics-Profile | | tenant_ref | admin | | exclude_revoked_ocsp_responses_as_error | True | | exclude_stale_ocsp_responses_as_error | True | | exclude_issuer_revoked_ocsp_responses_as_error | True | | exclude_unavailable_ocsp_responses_as_error | True | | hs_security_ocsp_revoked_score | 0.0 | | enable_adaptive_config | True | +-------------------------------------------------+-------------------------------------------------------+ +-------------------------------------------------+-------------------------------------------------------+ [admin:controller-vmdc2]: analyticsprofile> no exclude_revoked_ocsp_responses_as_error | +-------------------------------------------------+-------------------------------------------------------+ | Field | Value | +-------------------------------------------------+-------------------------------------------------------+ | uuid | analyticsprofile-1775513e-bbf5-47ce-a067-42237c91315d | | name | System-Analytics-Profile | | tenant_ref | admin | | exclude_revoked_ocsp_responses_as_error | False | | exclude_stale_ocsp_responses_as_error | True | | exclude_issuer_revoked_ocsp_responses_as_error | True | | exclude_unavailable_ocsp_responses_as_error | True | | hs_security_ocsp_revoked_score | 0.0 | | enable_adaptive_config | True | +-------------------------------------------------+-------------------------------------------------------+ +-------------------------------------------------+-------------------------------------------------------+ [admin:controller-vmdc2]: analyticsprofile> hs_security_ocsp_revoked_score 3.0 | +-------------------------------------------------+-------------------------------------------------------+ | Field | Value | +-------------------------------------------------+-------------------------------------------------------+ | uuid | analyticsprofile-1775513e-bbf5-47ce-a067-42237c91315d | | name | System-Analytics-Profile | | tenant_ref | admin | | exclude_revoked_ocsp_responses_as_error | False | | exclude_stale_ocsp_responses_as_error | True | | exclude_issuer_revoked_ocsp_responses_as_error | True | | exclude_unavailable_ocsp_responses_as_error | True | | hs_security_ocsp_revoked_score | 3.0 | | enable_adaptive_config | True | +-------------------------------------------------+-------------------------------------------------------+
The following fields are configurable.
exclude_revoked_ocsp_responses_as_error
exclude_stale_ocsp_responses_as_error
exclude_issuer_revoked_ocsp_responses_as_error
exclude_unavailable_ocsp_responses_as_error
These fields are enabled by default. When set to True, the corresponding logs are excluded from significant logs. To include the logs in significant logs, set the fields to False.
Also, hs_security_ocsp_revoked_score can be configured. By default, the score is set to 0.0 when the certificate or issuer certificate is revoked.
Risk and Risk Mitigation
OCSP stapling is effective because it offloads OCSP requests from browser to the server. It is optional. Browsers do not know whether a response is expected or not, and so they use a soft-fail behavior. This can lead to a security compromise. To avoid this possibility, the certificate extension called OCSP Must-Staple is used. With this label, the server communicates to the browser that the certificate has to be served with a valid OCSP response, n the absence of which, the certificate is not accepted.
In the event of a security compromise, even if the attacker has the key, they must supply an OCSP staple when using the certificate. If not, the browser rejects the certificate. If an OCSP staple is included, the response would identify the certificate as revoked, and the browser will reject the certificate. This mitigates the security issues of OCSP stapling.
Caveat
OCSP Stapling v2 described in RFC6961 defines a new extension status_request_v2 that enables the client to request the status of all certificates in the chain. Currently, in NSX Advanced Load Balancer, multiple certificate status requests are not supported. When a client sends the client hello with status_request_v2 extension, the NSX Advanced Load Balancer return the certificate status of only the application certificate directly attached to the virtual service.