This section explains the advanced configuration options relevant to the creation of an NSX Advanced Load Balancer OpenStack cloud.
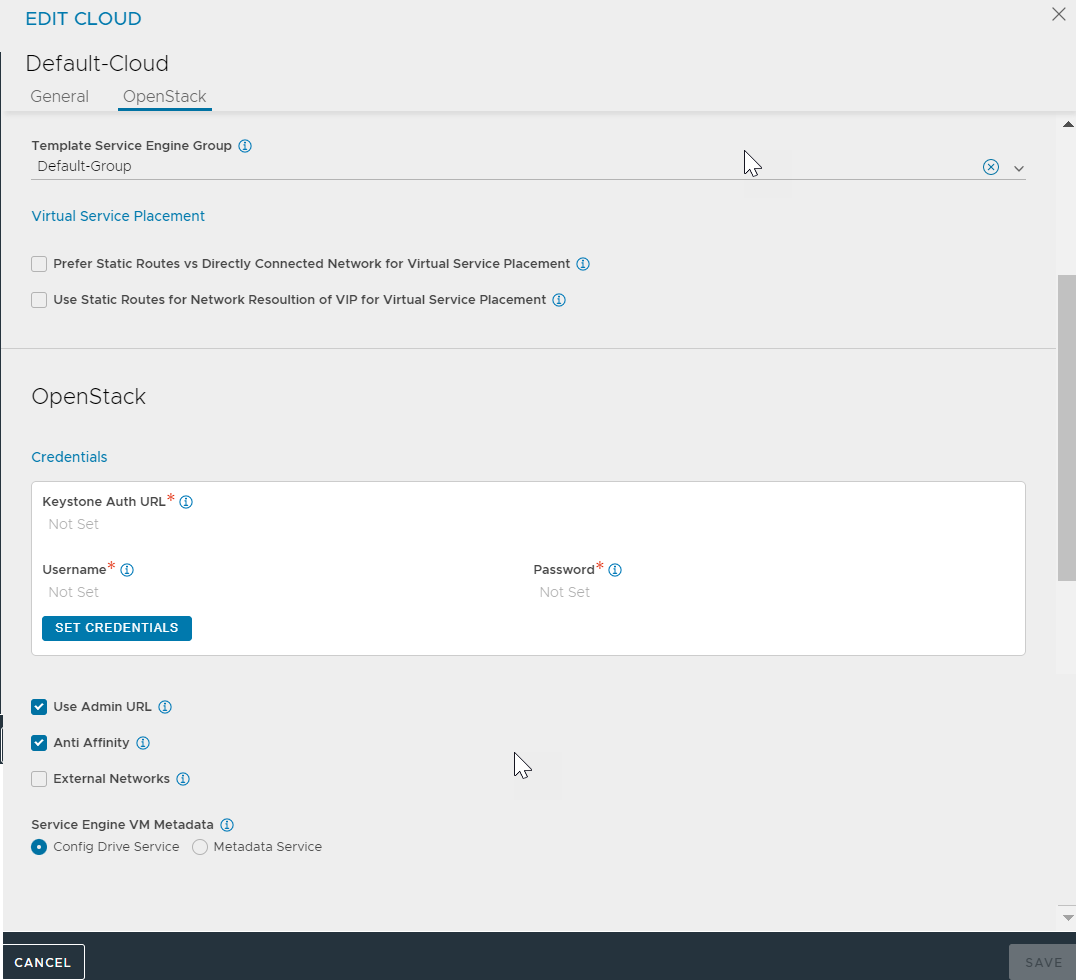
The advanced configuration options can be accessed from OpenStack tab of the NSX Advanced Load Balancer cloud editor wizard as shown in the image:
Security-Groups
The default value is
True.
The security-groups Neutron extension supports specifying the allowed rules for both ingress and egress. NSX Advanced Load Balancer uses this extension to create one service group per NSX Advanced Load Balancer Service Engine (SE). This service group is created with all egress and Secure Shell (SSH) and Internet Control Message Protocol (ICMP) ingress. As virtual services (VS) are created and placed on this SE, the corresponding service ports are added to the service group. Similarly, when the virtual services are unplaced from the SE, the corresponding service ports are removed from the service group (if no longer used by any other VS on the same SE). When set to True, the security-group extension will be used. If the underlying network plugin does not support this feature, then Virtual IP (VIP) traffic will not work unless there are other means to achieve the same effect. This option can be turned off if the underlying network supports turning off security filter rules on ports.
This example shows the security group of an SE with a virtual service with the service port ‘80’ placed on it.
[root@sivacos ~(keystone_admin)]# neutron security-group-list | 5544b75d-2a57-4f56-b1d0-ef68242293ba | avi-se-30af06c4-09c6-4c94-92be-f39d4dfddf91 | egress, IPv4 | | | | egress, IPv6 | | | | ingress, IPv4,22/tcp, remote_ip_prefix: 0.0.0.0/0 | | | | ingress, IPv4,80/tcp, remote_ip_prefix: 0.0.0.0/0 | | | | ingress, IPv4,icmp, remote_ip_prefix: 0.0.0.0/0 |
Anti-Affinity
The default value is
True.
Compute uses the nova-scheduler service to determine the host upon which to launch a virtual machine (VM) based on various criteria and filters. One such filter, ServerGroupAntiAffinityFilter, ensures that each instance in an anti-affinity group is on a different host of the group. NSX Advanced Load Balancer uses one anti-affinity group per SE group, thereby allowing each SE in the SE group to be placed on a different host. This provides better isolation of SEs in the event of host failures. If this option is set to False, anti-affinity filters will not be used. This option can be turned off if nova-compute has only one compute node.
This example shows an anti-affinity group, serviceenginegroup-37dac996-7c88-4761-a920-6dc9d265c786, in a tenant with two SE VMs.
root@node-17:~# nova server-group-list
+--------------------------------------+-------------------------+
| ID | Name
| Project ID | User ID
| Policies | Members
| Metadata |
+--------------------------------------+-------------------------+
| c605a898-86fa-457f-80c8-f1db21dfb68a | avi-aasg-serviceenginegroup-37dac996-7c88-4761-a920-6dc9d265c786
| fefb594ef03e4670beaffe3305440e24 | aba3667db25e44afb5aff73f3f363027
| [u'anti-affinity'] | [u'd7509390-6afe-4865-ade2-231e9a664421', u'1867c24e-8495-4cbf-80d0-06a2328656c6'] | {} |
+--------------------------------------+-------------------------+
root@node-17:~# nova list | egrep "d7509390|1867c24e"| d7509390-6afe-4865-ade2-231e9a664421 | cc_os-se-ozmkj
| ACTIVE | - | Running | avimgmt=10.10.44.231 |
| 1867c24e-8495-4cbf-80d0-06a2328656c6 | cc_os-se-xmrzn
| ACTIVE | - | Running | network-80.21=10.80.21.13;avimgmt=10.10.44.230
External-Networks
The default value is
False.
When set to True, this option enables selection of OpenStack networks marked ‘external’ for NSX Advanced Load Balancer management, VIP or data networks.
Map-admin-to-cloudadmin
The default value is False.
By default, the NSX Advanced Load Balancer admin tenant maps to the OpenStack admin tenant. If set to True, the NSX Advanced Load Balancer admin tenant maps to the admin_tenant configured in the NSX Advanced Load Balancer cloud. This directly maps the load-balancer-related operations onto the corresponding tenant in OpenStack.
Neutron-rbac
The default value is True.
By default, NSX Advanced Load Balancer consults the Neutron role-based-access-control (RBAC) rules to retrieve the ‘usable’ list of networks for a tenant. This list would typically include the tenant’s networks, any non-tenant networks widely shared with ‘all,’ and any non-tenant networks explicitly shared with the tenant using RBAC. This flag is helpful in a provider-mode SE configuration, and if set to False, the RBAC shared networks are not included in the ‘usable’ list.
Configuring Multi-Queue in OpenStack
The following are steps to configure multiqueue property in NSX Advanced Load Balancer Cloud using CLI (Example cloud name is Default-Cloud):
In SE-Group parameter max_queues_per_vnic is a boot-up property. This flag is a Service Engine Group boot-up property and if it is activated or deactivated; it will require all the Service Engines under that respective Service Engine Group to be rebooted.
[admin:avi-controller]: > configure cloud Default-Cloud [admin:avi-controller]: cloud> openstack_configuration [admin:avi-controller]: cloud:openstack_configuration> custom_se_image_properties New object being created [admin:avi-controller]: cloud:openstack_configuration:custom_se_image_properties> name hw_vif_multiqueue_enabled [admin:avi-controller]: cloud:openstack_configuration:custom_se_image_properties> value true [admin:avi-controller]: cloud:openstack_configuration:custom_se_image_properties> save [admin:avi-controller]: cloud:openstack_configuration> save [admin:avi-controller]: cloud> save
The following are the steps to remove the configuration:
[admin:avi-controller]: > configure cloud Default-Cloud [admin:avi-controller]: cloud> openstack_configuration [admin:avi-controller]: cloud:openstack_configuration> no custom_se_image_properties name hw_vif_multiqueue_enabled Removed custom_se_image_properties with name=hw_vif_multiqueue_enabled +-------------------------+-------------------------------+ | Field | Value | +-------------------------+-------------------------------+ | username | admin | | password | | | admin_tenant | admin | | mgmt_network_name | public | | privilege | WRITE_ACCESS | | use_keystone_auth | True | | region | RegionOne | | hypervisor | KVM | | tenant_se | True | | import_keystone_tenants | True | | anti_affinity | True | | security_groups | True | | allowed_address_pairs | True | | free_floatingips | False | | img_format | OS_IMG_FMT_AUTO | | use_admin_url | True | | role_mapping[1] | | | os_role | * | | avi_role | Tenant-Admin | | use_internal_endpoints | False | | config_drive | True | | auth_url | http://10.79.170.82:5000/v2.0 | | insecure | False | | external_networks | True | | neutron_rbac | True | | map_admin_to_cloudadmin | False | | contrail_plugin | False | | contrail_endpoint | http://10.79.170.82:8082 | | name_owner | True | | contrail_disable_policy | False | +-------------------------+-------------------------------+ [admin:avi-controller]: cloud:openstack_configuration> save [admin:avi-controller]: cloud> save</code></pre>