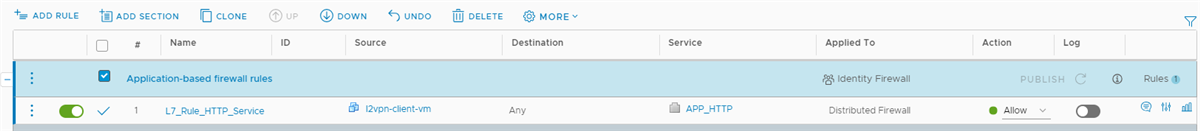
You can configure a context-aware or an application-based firewall rule by defining layer 7 service objects. A layer 7 context-aware firewall rule can intelligently inspect the content of the packets.
This example explains the process of creating a layer 7 firewall rule with APP_HTTP service object. This firewall rule allows HTTP requests from a virtual machine to any destination. After creating the firewall rule, you initiate some HTTP sessions on the source VM that passes this firewall rule, and turn on flow monitoring on a specific vNIC of the source VM. The firewall rule detects an HTTP application context and enforces the rule on the source VM.
Prerequisites
- Security administrator
- NSX administrator
- Security engineer
- Enterprise administrator
Procedure
What to do next
To know about other scenarios where you can use context-aware firewall rules, see Context-Aware Firewall Scenarios.
 ) icon.
) icon.