This scenario uses an HTTPS end-to-end application profile type with SSL client and server authentication.
Client Authentication
Clients access the Web application through HTTPS. HTTPS session is closed on the Edge VIP and the session requests for a client certificate.
- Add a Web server certificate that is signed by a root CA. For more information, see Scenario: Import SSL Certificate.
- Create an HTTPS application profile.
Version Procedure NSX 6.4.5 and later - In the Application Profile Type drop-down menu, select HTTPS End-to-End.
- Click .
- Select the web server certificate that you added in step 1.
- In the Client Authentication drop-down menu, select Required.
NSX 6.4.4 and earlier - In the Type drop-down menu, select HTTPS.
- Click . CA verifies the client certificate.
- Select the web server certificate that you added in step 1.
- In the Client Authentication drop-down menu, select Required.
- Create a virtual server. For information about specifying virtual server parameters, see Scenario: Import SSL Certificate.
Note: In NSX 6.4.4 and earlier, when the Enable Pool Side SSL option is disabled in the application profile, the pool selected is composed of HTTP servers. When the Enable Pool Side SSL option is enabled in the application profile, the pool selected is composed of HTTPS servers.
- Add a client certificate that is signed by the root CA in the browser.
-
- Go to the website https://www.sslshopper.com/ssl-converter.html.
- Convert certificate and private key to the pfx file. For complete examples of certificate and private key, see Example: Certificate and Private Key topic.
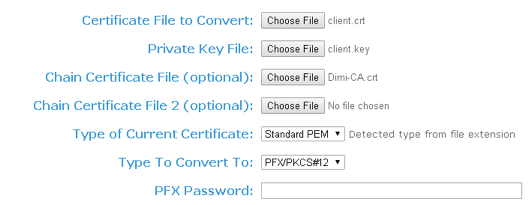
- Import the pfx file in the browser.
Server Authentication
Clients access the Web application through HTTPS. HTTPS session is closed on the Edge VIP. Edge establishes new HTTPS connections to the servers, and it requests and verifies the server certificate.
NSX Edge accepts specific ciphers.
- Add the Web server certificate that is chained with the root CA certificate for server certificate authentication. For more information, see Scenario: Import SSL Certificate.
- Create an HTTPS application profile.
Version Procedure NSX 6.4.5 and later - In the Application Profile Type drop-down menu, select HTTPS End-to-End.
- Click .
- Next to Cypher, click the Edit (
 ) icon, and select the ciphers.
) icon, and select the ciphers. - Enable the Server Authentication option.
- Select the CA certificate that you added in step 1.
NSX 6.4.4 and earlier - In the Type drop-down menu, select HTTPS.
- Select the Enable Pool Side SSL check box.
- Click . CA verifies the client certificate from the back-end HTTPS server.
- Select the Server Authentication check box.
- Select the CA certificate that you added in step 1.
- From the Cipher list, select the required ciphers.
Note:
If your preferred cipher is not in the approved ciphers list, it resets to Default.
After upgrading from an old NSX version, if the cipher is null or empty, or if the cypher is not in the approved ciphers list of the old version, it resets to Default.
- In the Client Authentication drop-down menu, select Required.
- Create a virtual server. For information about specifying virtual server parameters, see Scenario: Import SSL Certificate.
Note: In NSX 6.4.4 and earlier, when the Enable Pool Side SSL option is disabled in the application profile, the pool selected is composed of HTTP servers. When the Enable Pool Side SSL option is enabled in the application profile, the pool selected is composed of HTTPS servers.