You create a security group at the NSX Manager level.
Universal security groups are used in two types of deployments: active cross-vCenter NSX environments, and active standby cross-vCenter NSX environments, where one site is live at a given time and the rest are on standby.
- Universal security groups in an active environment can contain the following included objects only: security groups, IP sets, MAC sets. You cannot configure dynamic membership or excluded objects.
- Universal security groups in an active standby environment can contain the following included objects: security groups, IP sets, MAC sets, universal security tags. You can also configure dynamic membership using VM Name only. You cannot configure excluded objects.
Note:
Powered off VM's that are based on dynamic criteria such as Computer OS Name and Computer Name will not be included in Security Groups. Dynamic criteria is received by NSX only once when the VM is powered on. After being powered on, the guest details are synced to NSX Manager and remain with the NSX Manager even if the VM is later powered off.
Note: Universal security groups created prior to 6.3 cannot be edited for use in active standby deployments.
Prerequisites
If you are creating a security group based on Active Directory group objects, ensure that one or more domains have been registered with NSX Manager. NSX Manager gets group and user information as well as the relationship between them from each domain that it is registered with. See Register a Windows Domain with NSX Manager.
Procedure
- In the vSphere Web Client, click .
- Navigate to Security Group:
- In NSX 6.4.1 and later, ensure that you are in the Security Groups tab.
- In NSX 6.4.0, ensure that you are in the tab.
- If multiple IP addresses are available in the NSX Manager drop-down menu, select an IP address, or keep the default selection.
- To manage universal security groups, the primary NSX Manager must be selected.
- Click Add or the Add New Security Group icon.
- Type a name and optionally a description for the security group.
- (Optional) If you are creating a universal security group, select Universal Synchronization or Mark this object for universal synchronization.
- (Optional) If you are creating a universal security group for use in an active standby deployment, select both Universal Synchronization / Mark this object for universal synchronization and Use for active standby deployments. Dynamic membership for universal security groups with active standby deployment is based on virtual machine name
- Click Next.
- On the Dynamic Membership page, define the criteria that an object must meet for it to be added to the security group you are creating. This gives you the ability to include virtual machines by defining a filter criteria with a number of parameters supported to match the search criteria.
Note: If you are creating a universal security group, the
Define dynamic membership step is not available in active active deployments. It is available in active standby deployments, based on virtual machine name only.
For example, you may include a criterion to add all virtual machines tagged with the specified security tag (such as AntiVirus.virusFound) to the security group. Security tags are case sensitive.
Or you can add all virtual machines containing the name W2008 and virtual machines that are in the logical switch global_wire to the security group.
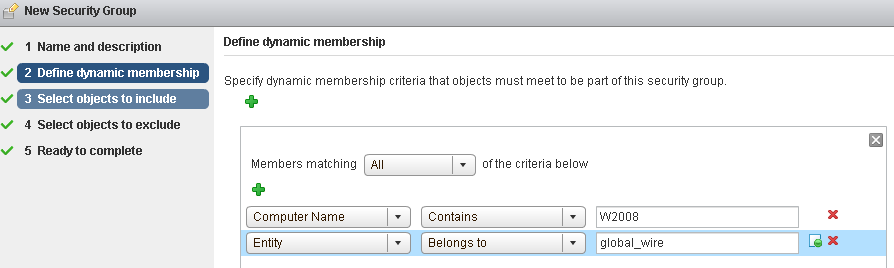
- Click Next.
- On the Select objects to include page, select the tab for the resource you want to add and select one or more resources to add to the security group. You can include the following objects in a security group.
Table 1.
Objects that can be included in security groups and universal security groups.
| Security Group |
Universal Security Group |
- Other security groups to nest within the security group you are creating.
- Cluster
- Logical Switch
- Network
- Virtual App
- Datacenter
- IP sets
- Directory Groups
Note: The Active Directory configuration for NSX security groups is different from the AD configuration for vSphere SSO. NSX AD group configuration is for end users accessing guest virtual machines, while vSphere SSO is for administrators using vSphere and NSX. In order to consume these directory groups you must sync with Active Directory. See
Identity Firewall Overview.
- MAC Sets
- Security tag
- vNIC
- Virtual Machine
- Resource Pool
- Distributed Virtual Port Group
|
- Other universal security groups to nest within the universal security group you are creating.
- Universal IP sets
- Universal MAC sets
- Universal Security Tag (active standby deployments only)
|
The objects selected here are always included in the security group regardless of whether or not they match the criteria that you defined earlier on the Dynamic Membership page.
When you add a resource to a security group, all associated resources are automatically added. For example, when you select a virtual machine, the associated vNIC is automatically added to the security group.
- Click Next and select the objects that you want to exclude from the security group.
Note: If you are creating a universal security group, the
Select objects to exclude step is not available.
The objects selected here are always excluded from the security group regardless of whether or not they match the dynamic criteria.
- Click Next.
The
Ready to Complete window appears with a summary of the security group.
- Click Finish.
Example
Membership of a security group is determined as follows:
{Expression result (derived from Define dynamic membership) + Inclusions (specified in Select objects to include} - Exclusion (specified in Select objects to exclude)
This means that inclusion items are first added to the expression result. Exclusion items are then subtracted from the combined result.
