When an operator creates a new DLR, the following wizard is used to collect the necessary information.
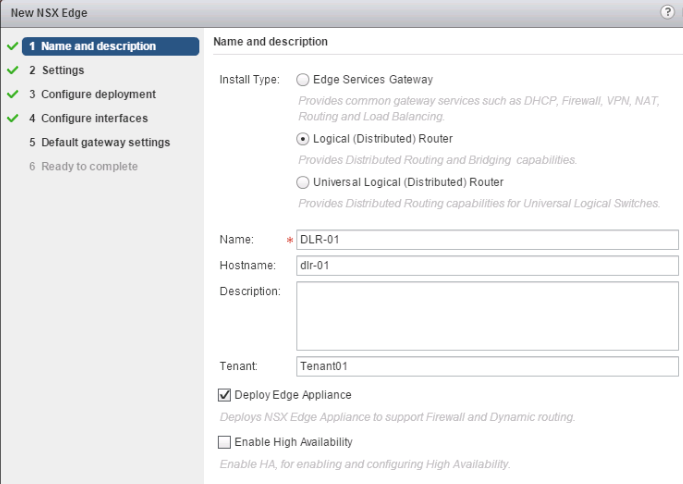
On the “Name and Description” screen, the following information is collected:
- “Name” will appear in the “NSX Edges” UI.
- “Hostname” will be used to set the DNS name of the ESG or DLR Control VM, visible on SSH/Console session, in syslog messages, and in the vCenter “Summary” page for the ESG/DLR VM under “DNS Name.”
- “Description” is in the UI showing the list of NSX Edges.
- “Tenant” will be used to form the DLR Instance Name, used by the NSX CLI. It can be also be used by external cloud management platform.
On the “Settings” screen:
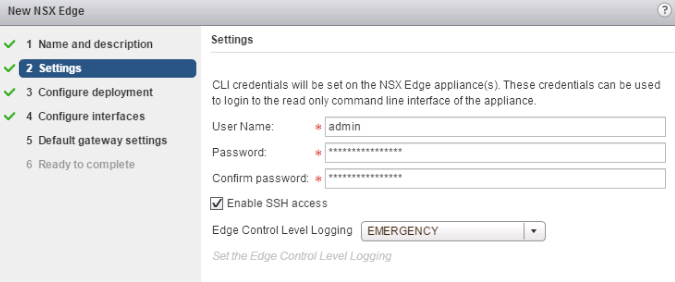
- “User Name” and “Password” set the CLI/VM console credentials to access the DLR Control VM. NSX does not support AAA on ESG or DLR Control VMs. This account has full rights to ESG/DLR Control VMs; however, the ESG/DLR configuration cannot be changed via the CLI/VMconsole.
- “Enable SSH access” enables the SSH daemon on the DLR Control VM to start.
- The control VM Firewall rules need to be adjusted to allow SSH network access.
- The operator can connect to the DLR Control VM from either a host on the subnet of the Control VM’s management Interface, or without such restriction on the OSPF/BGP “Protocol Address," if a protocol address is configured.
Note: It is not possible to have network connectivity between the DLR Control VM and any IP address that falls into any subnet configured on any of that DLR’s “Internal” interfaces. This is because the egress interface for these subnets on DLR Control VM points to the pseudo-interface “VDR," which is not connected to the data plane.
- “Enable HA” deploys Control VM as an Active/Standby HA pair.
- “Edge Control Level Logging” sets the syslog level on the Edge appliance.
On the “Configure deployment” screen:
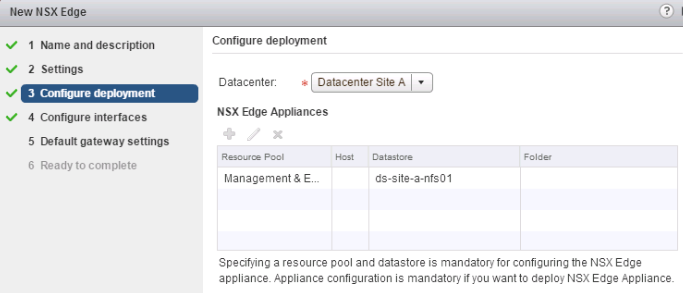
- “Datacenter” selects the vCenter datacenter in which to deploy the Control VM.
- “NSX Edge Appliances” refers to the DLR Control VM and allows definition of exactly one (as shown).
- If “HA” is enabled, the Standby Edge will be deployed on the same cluster, host, and datastore. A DRS “Separate Virtual Machines” rule will be created for the Active and Standby DLR Control VMs.
On the “Configure Interfaces” screen:
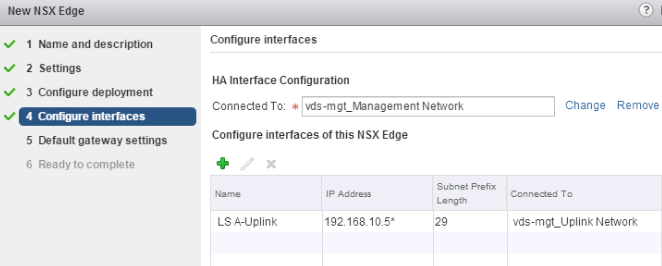
- “HA Interface”
- Is not created as a DLR logical interface capable of routing. It is only a vNIC on the Control VM.
- This interface does not require an IP address, because NSX manages the DLR configuration via VMCI.
- This interface is used for HA heartbeat if the DLR "Enable High Availability” is checked on the "Name and description" screen.
- “Interfaces of this NSX Edge” refer to DLR Logical Interfaces (LIFs)
- The DLR provides L3 gateway services to VMs on the “Connected To” dvPortgroup or logical switch with IP addresses from corresponding subnets.
- “Uplink” type LIFs are created as vNICs on the Control VM, so, up to eight are supported; the last two available vNICs are allocated to the HA interface and one reserved vNIC.
- An “Uplink” type LIF is required for dynamic routing to work on the DLR.
- And “Internal” type LIFs are created as pseudo-vNICs on the Control VM, and it is possible to have up to 991 of them.
On the “Default gateway settings” screen:
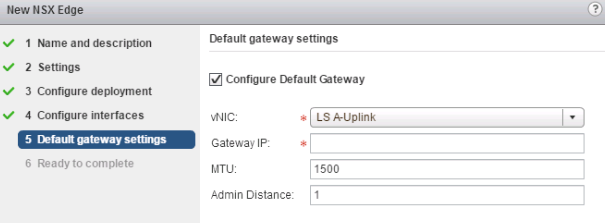
- Configure Default Gateway, if selected, will create a static default route on the DLR. This option is available if an “Uplink” type LIF is created in the previous screen.
- If ECMP is used on the uplink, the recommendation is to leave this option disabled, to prevent dataplane outage in case of next-hop failure.
Note: The double right-arrow in the top right corner allows for “suspending” the wizard in progress so that it can be resumed at a later time.