This topic discusses common configuration issues related to L2 VPN.
In the following procedure:
- Steps 1, 2, and 3 are applicable only when the L2 VPN service is running on an SSL tunnel.
- Steps 4, 5, and 6 are applicable when the L2 VPN service is running on both SSL and IPSec tunnels.
Problem
Following configuration issues are specific to L2 VPN clients that use SSL VPN tunnels for routing traffic:
- L2 VPN client is configured, but Internet-facing firewall does not allow traffic to flow through the tunnel using destination port 443.
- L2 VPN client is configured to validate server certificate, but it is not configured with correct CA certificate or FQDN.
Following configuration issues are common to L2 VPN clients that use either SSL VPN tunnels or IPSec VPN tunnels for routing traffic:
- L2 VPN server is configured, but NAT or firewall rule is not created on the Internet-facing firewall.
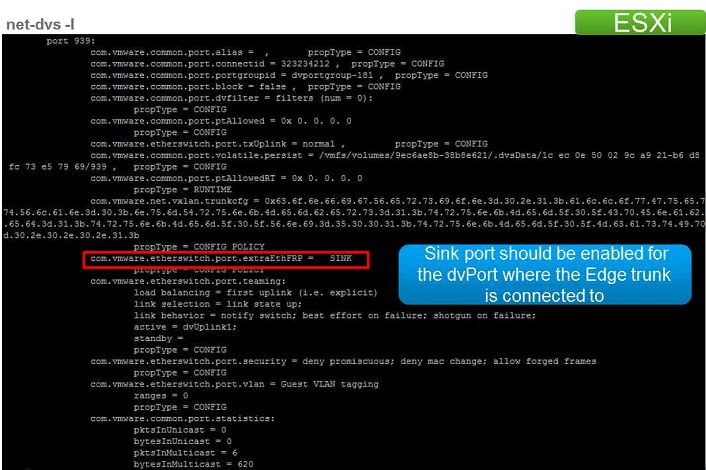
- Trunk interface is not backed by either a distributed port group or a standard port group.
Note: For L2 VPN running on SSL tunnels, remember that:
- L2 VPN server listens on port 443 by default. This port is configurable from L2 VPN server settings.
- L2 VPN client makes an outgoing connection to port 443 by default. This port is configurable from the L2 VPN client settings.