In this example, your objective is to create a security policy with Distributed Malware Prevention firewall rules that detects and prevents malicious Portable Executable files on Windows workload VMs that are running database servers and Web servers in your organization.
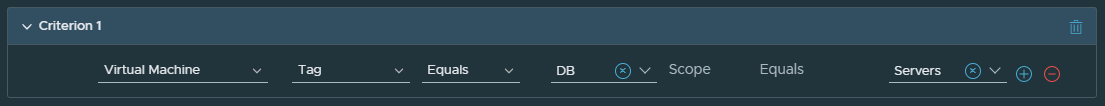
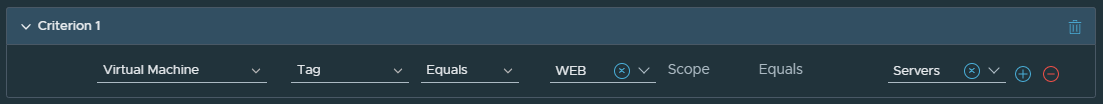
You can use the NSX Distributed Malware Prevention service in NSX-T Data Center to meet this objective. For this example, you will group workload VMs of database servers and Web servers by using a dynamic membership criterion based on tags.
Assumptions:
- Tags required for grouping of workload VMs are added already in the NSX-T inventory, as follows:
- Tag Name: DB, Scope: Servers
- Tag Name: WEB, Scope: Servers
- DB Tag is assigned to three database workloads (Windows VMs): VM1, VM2, and VM3.
- WEB Tag is assigned to three application workloads (Windows VMs): VM4, VM5, and VM6
- Cloud File Analysis option is selected in the Malware Prevention profile.
Prerequisites
NSX Malware Prevention service virtual machine is deployed on vSphere host clusters where the workload VMs are running. For detailed instructions, see Deploy the NSX Distributed Malware Prevention Service.
Procedure
Results
The rule is pushed to the host.
When Windows Portable Executable (PE) files are detected on the workload VMs, file events are generated and shown in the Malware Prevention dashboard. If the file is benign, the file is downloaded on the workload VM. If the file is a known malware (file matches known malware file signatures in NSX-T), and Detect and Prevent mode is specified in the rule, then the malicious file is blocked on the workload VM.
If the file is an unknown malware (Day-zero threat) and detected for the first time in the data center, it is downloaded on the workload VM. After NSX-T has determined the file verdict as malicious either by using local file analysis or cloud file analysis, the verdict is distributed to the other ESXi hosts and NSX Edges in the data center, which are activated for NSX Malware Prevention. When the file with the same hash is detected again on any of the workload VMs that are protected by NSX Malware Prevention, the security policy is applied, and the malicious file is blocked on the workload VMs.