As an admin, you can configure a physical server for NSX-T networking through the NSX Manager GUI.
Alternatively, you can run the Ansible script to achieve the same goal. See Secure Workloads on Windows Server 2016/2019 Bare Metal Servers for configuring Windows physical servers using Ansible. However, it is recommended to use the NSX Manager UI to prepare physical servers for NSX-T networking.
Physical servers supports an overlay and VLAN transport zone. You can use the management interface to manage the physical server server. The application interface allows you to access the applications on the physical server. These NIC configurations are supported on a physical server:
- Single physical NIC cards provide an IP address for both the management and the application IP interfaces.
- Dual physical NIC cards provide a physical NIC and a unique IP address for the management interface. Dual physical NIC cards also provide a physical NIC, and a unique IP address for the application interface.
- Windows servers: Dual physical NIC cards in a bonded configuration provide a unique IP address for both the management interface and the application interface. Such physical NIC bonds are supported through bonds created in the OS. Bond must be configured in the Switch Independent mode. Traffic running on management network is not supported on a bonded teaming interface.
- Linux servers: Bond interface only supports underlay mode (VLAN 0). Supported flavors are CentOS 7.9, CentOS 8.3, RHEL 7.9 and RHEL 8.3. Physical NIC bonds are supported in Active/Active and Active/Standby mode through OVS switch.
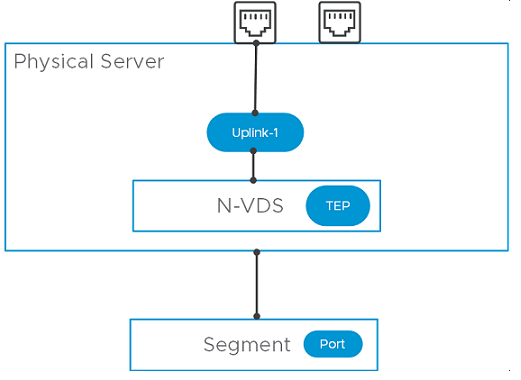
- Create a segment port on an NSX-T segment.
- Attach application interface of the physical server to the segment port.
Prerequisites
- A transport zone must be configured.
- An uplink profile must be configured, or you can use the default uplink profile.
- An IP pool must be configured, or DHCP must be available in the network deployment.
- At least one physical NIC must be available on the host node.
- Hostname
- Management IP address
- User name
- Password
- A segment (VLAN or Overlay), depending upon your requirement, must be available to attach to the application interface of the physical server.
- Verify that the required third-party packages are installed. Third party packages must be installed on the physical server so that its physical NICs are available during transport node configuration. See Install Third-Party Packages on a Physical Server.
- On Windows physical servers, log in as an administrator to install NSX.
- Starting with NSX Data Center 3.2.1, on Linux physical servers, you can update the sudoers file to add custom users with minimal privileges. The custom users allows you to install NSX without root permissions.
After configuring visudo, run the following command to access the /etc/sudoers file.
$ sudo visudo
RHEL/CentOS/OEL/SLES:
tester ALL=(ALL) /usr/bin/rpm, /usr/bin/nsxcli, /usr/bin/systemctl restart openvswitch
Ubuntu:tester ALL=(ALL) /bin/ls, /usr/bin/sudo, /usr/bin/dpkg, /bin/nsxcli
Procedure
Results
The physical server is configured for NSX-T networking.