This topic helps describes the key concepts and architecture of service insertion and NSX Guest Introspection Platform components (guest introspection).
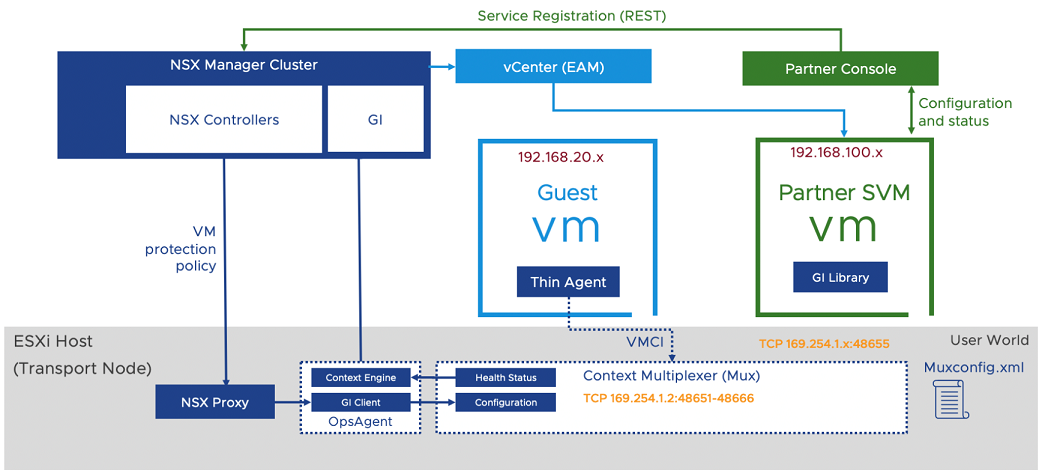
- NSX Manager: It is the management plane appliance for NSX that provides API and graphical user interface to customers and partners for configuration of Network and Security policies. For guest introspection, the NSX Manager also provides API and GUI to deploy and manage partner appliances.
- Guest Introspection SDK: VMware provided library consumed by the security vendor.
-
Service VM: It is the security vendor provided VM that consumes the guest introspection SDK provided by VMware. It contains the logic to scan file, process, network and system events to detect virus or malware on the guest. After scanning a request, it sends back a verdict or notification about the action taken by the guest VM on the request.
- Guest Introspection host agent (Context Multiplexer): It processes configuration of endpoint protection policies. It also multiplexes and forwards messages from protected VMs to the Service VM and back from Service VM to protected VMs. It reports the health status of the guest introspection platform and maintains records of the Service VM configuration in the
muxconfig.xmlfile. - Ops agent (Context engine and Guest Introspection client): It forwards the guest introspection configuration to the guest introspection host agent (Context Multiplexer). It also relays the health status of the solution to NSX Manager.
- EAM: NSX Manager uses the ESXi agent manager to deploy a partner Service VM on every host on the cluster configured for protection.
-
Thin agent: It is the file and/or network introspection agent running inside the guest VMs. It intercepts file and network activities or events that are forwarded to the Service VM through the host agent. On Windows, this agent is part of VMware Tools. On Linux, this agent exists outside of VMware Tools. It provides in-guest context to NSX and can also be used to replace the traditional agent provided by antivirus or antimalware security vendors. It is a generic and lightweight agent that facilitates offloading files and processes for scanning to the Service VM provided by the vendor.
- Reduced consumption of compute resources: Guest introspection offloads signatures and security scanning logic from each endpoint on a host to a third-party partner Service VM on the host. As scanning happens only on the Service VM, there is no need to spend compute resources on guest VMs to run scans.
-
Better management: As scans are offloaded to a Service VM, signatures need to be updated to only one object per host. Such a mechanism works better than agent-based solution where same signatures need updates on all guest VMs.
- Continuous antivirus and antimalware protection: As the Service VM runs continuously, a guest VM is not mandated to run the latest signatures. For example, a snapshot VM might run some older version of the signature making it vulnerable in the traditional way of protecting endpoints. With the guest introspection platform, the Service VM is continuously running the latest and malware signatures thereby ensuring that any newly added VM is also protected with the latest signatures.
- Offloaded signatures to a Service VM: database lifecycle is outside of guest VM lifecycle and so the Service VM is not affected by guest VM outages.