In this example, your objective is to create security policies with Gateway Firewall rules that detect malicious files on the north-south traffic, which is passing through the NSX Edges in your NSX.
For this example, consider that your network topology is as shown in the following figure. You will add Gateway Malware Prevention rules to detect malware on tier-1 gateways: T1-GW1 and T1-GW2. Both tier-1 gateways have an overlay segment attached to it. Workload VMs are attached to the overlay segments. Both tier-1 gateways are connected to a single tier-0 gateway, which in turn is connected to the physical top-of-rack switch to enable connectivity with the outside public network.
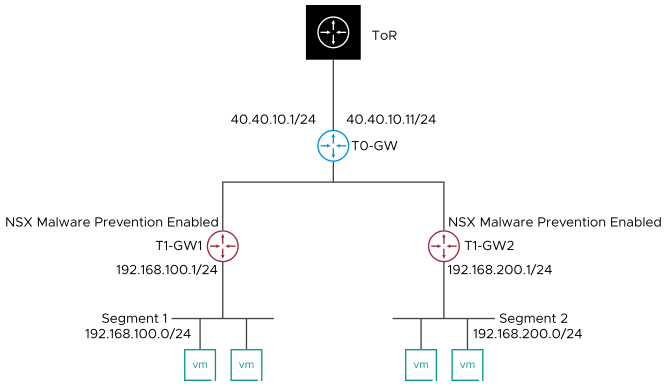
Assumptions:
Procedure
- From your browser, log in to an NSX Manager at https://nsx-manager-ip-address.
- Navigate to .
- On the Gateway Specific Rules page, in the Gateway drop-down menu, select T1-GW1.
- Click Add Policy to create a section, and enter a name for the policy.
For example, enter
Policy_T1-GW1.
- Click Add Rule and configure two rules with the following configurations.
| Name |
ID |
Sources |
Destinations |
Services |
Security Profiles |
Applied To |
Mode |
| N_to_S |
1011 |
North |
South |
HTTP |
Profile_T1-GW |
T1-GW1 |
Detect Only |
| S_to_N |
1010 |
South |
North |
HTTP |
Profile_T1-GW |
T1-GW1 |
Detect Only |
The rule IDs in this table are only for reference. They might vary in your NSX environment.
Let us understand the meaning of these rules:
- Rule 1011: This rule is enforced on T1-GW1 when HTTP connections are initiated by the machines in the public IP range (12.1.1.10-12.1.1.100) and these connections are accepted by the workload VMs that are attached to Segment1. If a file is detected in the HTTP connection, a file event is generated, and the file is analyzed for malicious behavior.
- Rule 1010: This rule is enforced on T1-GW1 when HTTP connections are initiated by the workload VMs on Segment1 and these connections are accepted by the machines in the public IP range (12.1.1.10-12.1.1.100). If a file is detected in the HTTP traffic, a file event is generated, and the file is analyzed for malicious behavior.
- Publish the rules.
- On the Gateway Specific Rules page, in the Gateway drop-down menu, select T1-GW2.
- Click Add Policy to create a section, and enter a name for the policy.
For example, enter
Policy_T1-GW2.
- Click Add Rule and configure an Any-Any rule as follows.
| Name |
ID |
Sources |
Destinations |
Services |
Security Profiles |
Applied To |
Mode |
| Any_Traffic |
1006 |
Any |
Any |
Any |
Profile_T1-GW |
T1-GW2 |
Detect Only |
This rule is enforced on T1-GW2 when any type of traffic is initiated from any source and accepted by any destination. If a file is detected in the traffic, a file event is generated, and the file is analyzed for malicious behavior.
- Publish the rules.
Example
Scenario: In the same topology as shown earlier, assume that a VM on Segment1 wants to transmit a file to a VM on Segment2. In this case, the file traverses through both tier-1 gateways: T1-GW1 and T1-GW2. As Malware Prevention profile is configured on both tier-1 gateways, the file is inspected twice and two file events are generated. This behavior is expected.
