On the campaign's Timeline tab in the Campaign Details page, the threats detected by NSX Network Detection and Response are represented by threat cards.
Sort the threat cards with the Sort by drop-down menu. Select from Most recent (the default), Earliest, Highest impact, and Lowest impact.
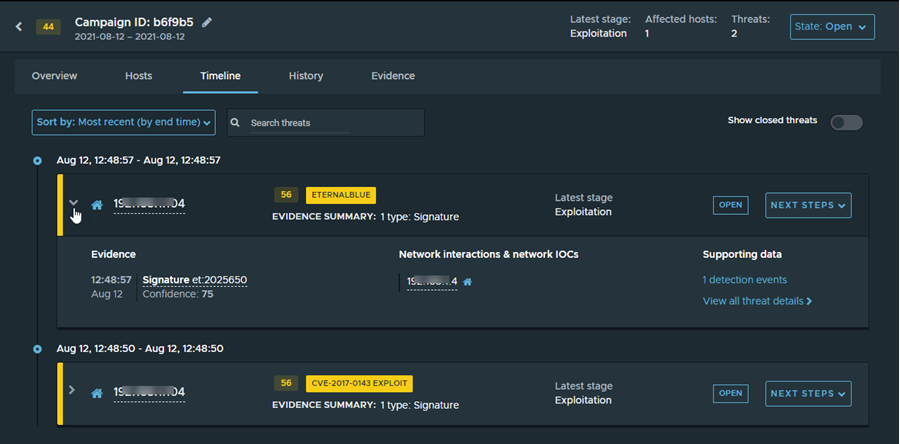
The Search threats text box above the list provides fast, as-you-enter search. It filters the rows in the list, displaying only those rows that have text, in any field, that matches the query string. Your query is matched against values across the following categories: impact, IP address, threat/malware, latest campaign phase, first seen, evidence, and other hosts, and, for mail messages, message information.
To filter the displayed threat cards by threat status, toggle the Show closed threats button. The default is to show all threats.
Threat Cards
The threat cards show all the threats associated with the selected campaign and their corresponding threat levels.
Each card displays the calculated threat impact, the threat name, the threat class, and if available, the detection outcome. It also shows the status of the threat: OPEN or CLOSED.
You can click Next Steps and select an action from the drop-down menu. Select Close to close the threat, Open to reopen a closed threat, or Manage Alert to create an alert management rule from the threat.
The Evidence Summary section contains an overview of the evidence and other data detected for the threat. Click the ![]() icon (or almost anywhere else in the card) to expand the Evidence details section.
icon (or almost anywhere else in the card) to expand the Evidence details section.
Evidence Details
The Evidence column displays the file downloads, signatures, and other categories along with a timestamp of when the evidence was seen.
The Network interactions & network IOCs column displays the IP address or domain name of external hosts. Click the IP address link to expand the Network Interaction sidebar.
The Supporting data column provides a link to the detected events, a link to the captured data, and a link to the threat details.