Configure east-west and north-south firewall policies under predefined categories for your environment.
Distributed Firewall (east-west) and Gateway Firewall (north-south) offer multiple sets of configurable rules divided by categories. You can configure an exclusion list that contains logical switches, logical ports, or groups, to be excluded from firewall enforcement.
NSX Firewall simplifies policy definition by having pre-defined categories, which help in organizing rules.
- Gateway firewall policy categories: emergency, system, pre-rules, local gateway, auto service, default. For more information see Gateway Firewall
- Distributed firewall policy categories: ethernet, emergency, infrastructure, environment, application, default. For more information see Distributed Firewall.
The categories are ordered from left to right, and the rules are ordered from top to bottom. Packets are matched against the rules with top-to-bottom ordering within each category. Each packet is checked against the top rule starting with the left-most category's rule table before moving down the subsequent rules in that table. If no match is found, then the same check is performed against the rules in the next category. The first rule that matches the traffic parameters is enforced. If the rule action is Allow, Drop, or Reject, no subsequent rules can be enforced as the search is then terminated for that packet. The rules in the Environment category have a additional "Jump to Application" action; any packet that matches such a rule will also be matched against the rule table and be policed by the matching rule of the Application category with top-to-bottom ordering. Because of this behavior, it is always recommended to put the most granular policies at the top of the rule table. This ensures that they will be enforced before more generic rules.
The default NSX firewall rule that matches any packet not policied by a finer grain rule is configured with a permissive action. We recommend you configure more specific allowlist rules to permit traffic flows required by applications, and subsequently change the default rule to drop or reject in order to create a more secure security posture. Whether an east-west or north-south firewall fails close or fails open upon failure depends on the last rule in the firewall.
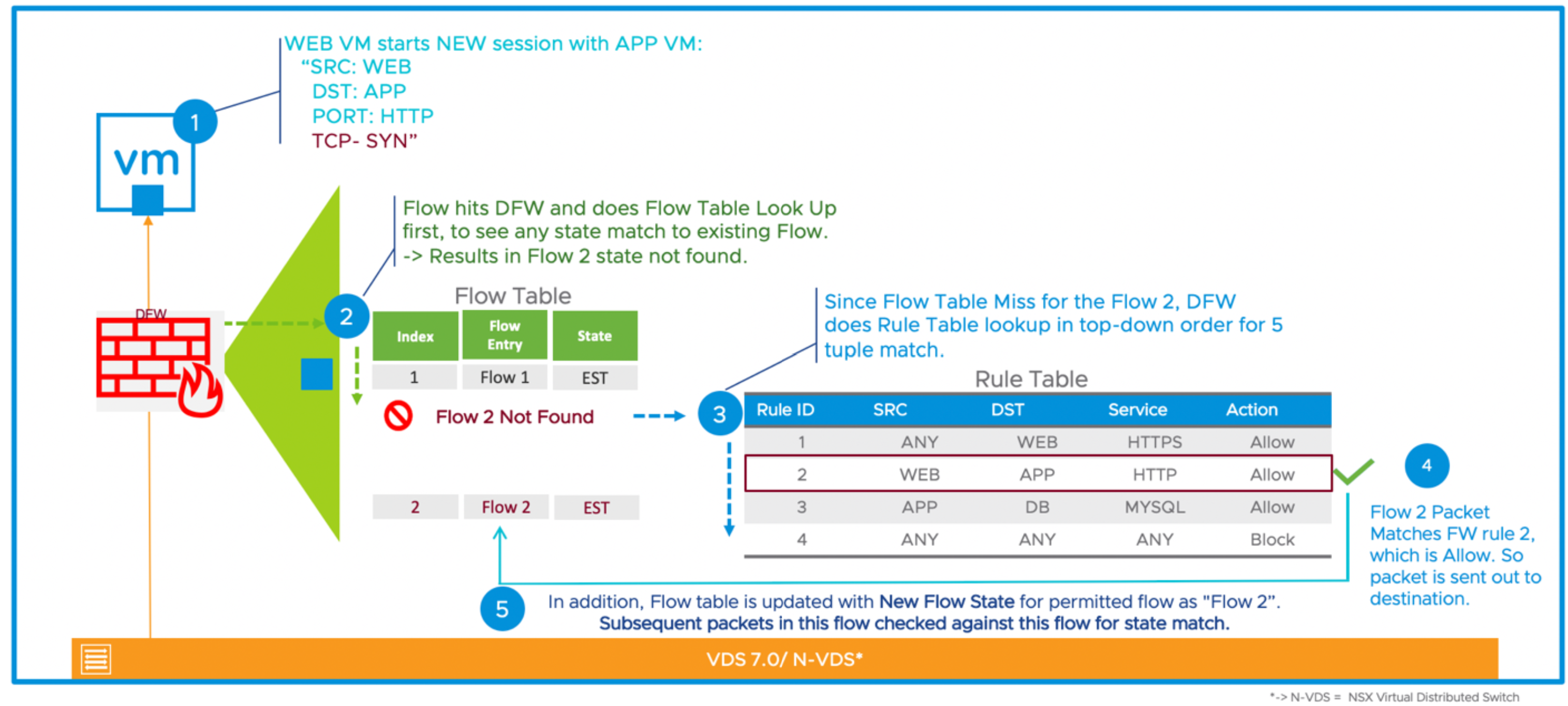
- A lookup is performed in the connection tracker table to determine if an entry for the flow already exists.
- As flow 2 is not present in the connection tracker table, a lookup is performed in the rule table to identify which rule is applicable to flow 2. The first rule that matches the flow will be enforced.
- Rule 2 matches for flow 2. The action is set to ‘Allow’.
- Because the action is set to ‘Allow’ for flow 2, a new entry will be created inside the connection tracker table. The packet is then transmitted out of DFW.