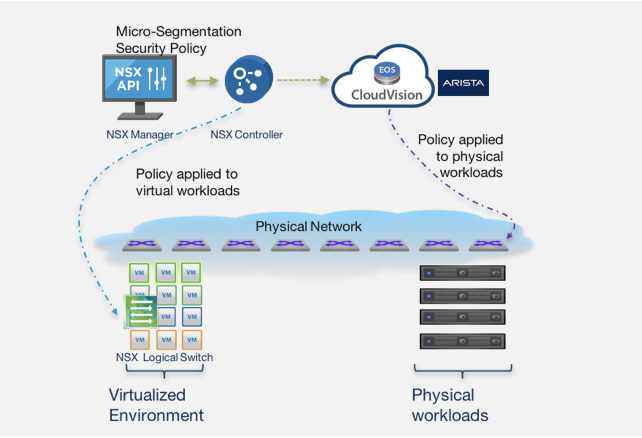
NSX can act as a single point of administration for both virtual and physical workloads.
NSX supports integration with Arista CloudVision eXchange (CVX). This integration facilitates consistent networking and security services across virtual and physical workloads, independent of your application frameworks or physical network infrastructure. NSX does not directly program the physical network switch or router but integrates at the physical SDN controller level, therefore preserving the autonomy of security administrators and physical network administrators.
NSX supports integration with Arista EOS 4.22.1FX-PCS and later.
Limitations
- Arista switches require ARP traffic to exist before firewall rules are applied to an end host that is connected to an Arista switch. Packets can therefore pass through the switch before firewall rules are configured to block traffic.
- Allowed traffic does not resume when a switch crashes or is reloaded. The ARP tables need to be populated again, after the switch comes up, for the firewall rules to be enforced on the switch.
- Firewall rules cannot be applied on the Arista Physical Switch, for FTP passive clients that connect to FTP Server connected to the Arista Physical Switch.
- In CVX HA setup that uses Virtual IP for the CVX cluster, the CVX VM’s dvpg’s Promiscuous mode, and Forged transmits must be set to Accept. In case they are set to default (Reject), the CVX HA Virtual IP will not be reachable from NSX Manager.