After configuring NSX, complete the configuration procedure on Arista CloudVision eXchange (CVX) to enable CVX to interact with NSX.
Prerequisites
NSX has registered the CVX as an enforcement point.
Procedure
- Log in to NSX Manager as a root user and run the following command to create a thumbprint for CVX to communicate with NSX Manager:
openssl s_client -connect <IP address of nsx-manager>:443 | openssl x509 -pubkey -noout | openssl rsa -pubin -outform der | openssl dgst -sha256 -binary | openssl base64
Sample output:depth=0 C = US, ST = CA, L = Palo Alto, O = VMware Inc., OU = NSX, CN = nsx-mgr verify error:num=18:self signed certificate verify return:1 depth=0 C = US, ST = CA, L = Palo Alto, O = VMware Inc., OU = NSX, CN = nsx-mgr verify return:1 writing RSA key S+zwADluzeNf+dnffDpYvgs4YrS6QBgyeDry40bPgms=
- Run the following commands from the CVX CLI:
cvx no shutdown service pcs no shutdown controller <IP address of nsx-manager> username <NSX administrator user name> password <NSX administrator password> enforcement-point cvx-default-ep pinned-public-key <thumbprint for CVX to communicate with NSX Manager> notification-id <notification ID created while registering CVX with NSX> end - Run the following command from the CVX CLI to check the configuration:
show running-config
Sample ouput:cvx no shutdown source-interface Management1 ! service hsc no shutdown ! service pcs no shutdown controller 192.168.2.80 username admin password 7 046D26110E33491F482F2800131909556B enforcement-point cvx-default-ep pinned-public-key sha256//S+zwADluzeNf+dnffDpYvgs4YrS6QBgyeDry40bPgms= notification-id a0286cb6-de4d-41de-99a0-294465345b80 - Configure tag on the ethernet interface of the physical switch that connects to the physical server. Run the following commands on the physical switch managed by CVX.
configure terminal interface ethernet 4 tag phy_app_server end copy running-config startup-config Copy completed successfully.
- Run the following command to verify tag configuration for the switch:
show running-config section tag
Sample output:interface Ethernet4 description connected-to-7150s-3 switchport trunk allowed vlan 1-4093 switchport mode trunk tag sx4_app_server
IP addresses that are learnt on the tagged interfaces, using ARP, are shared with NSX.
- Log in to NSX Manager to create and publish firewall rules for the physical workloads managed by CVX. See Security for more information on creating rules. For example:
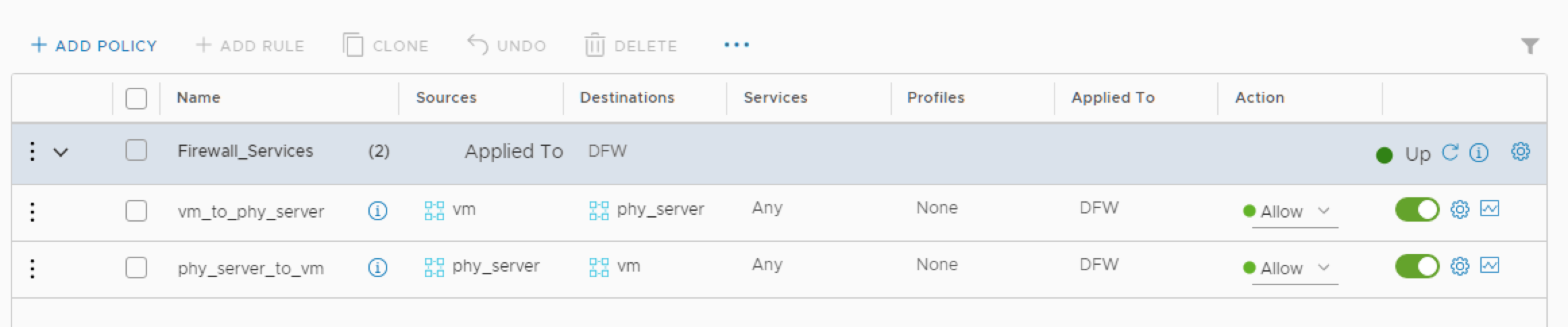 NSX policies and rules published in NSX appear as dynamic ACLs on the physical switch managed by CVX.
NSX policies and rules published in NSX appear as dynamic ACLs on the physical switch managed by CVX.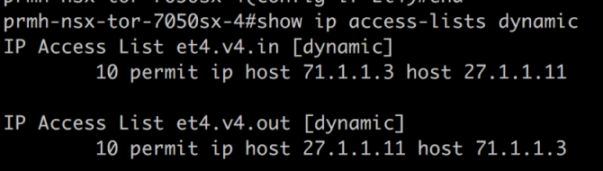
For more information, see CVX HA set up, CVX HA Virtual IP setup, and Physical Switch Mlag Setup