Secure workloads that are running on Windows Server 2016 bare metal servers.
Prerequisites
- Configure WinRM for Windows bare metal servers.
- Install Linux packages needed for Linux bare metal servers.
You can provide connectivity and security to applications or workloads between:
- Physical workloads (bare metal server) and virtual workloads
- Virtual workloads and physical workloads (bare metal server)
- Physical workloads (bare metal server) and physical workloads (bare metal server)
Before securing bare metal hosts, do the following:
- Ensure the NSX Agent is installed on the bare metal host.
- Establish network connectivity between the application IP address of the Windows bare metal server, NSX Agent and NSX Manager.
- Apply DFW rules to secure ingress and egress traffic flowing through the L2 and L3 networks between workloads on a Windows Server 2016 bare metal server and virtual or physical workloads.
A couple of use cases where ingress and egress trafffic is filtered at the Windows bare metal server.
Traffic between Virtual and Physical Bare Metal Workloads

Traffic between Physical Bare Metal Workloads
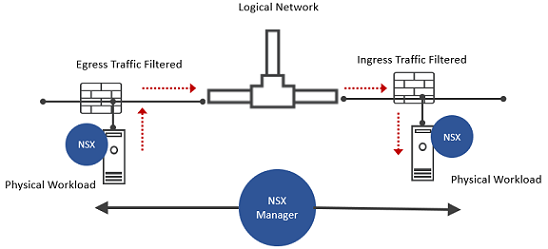
Before you apply DFW rules to the Windows bare metal workloads, integrate NSX on the Windows Server using Ansible scripts. To install and integrate NSX on a Windows bare metal server, refer to the Secure Workloads on Windows Server 2016 Bare Metal Server topic in the NSX Installation Guide.