VMware NSX builds security into the network virtualization infrastructure. There are many built-in services that are part of NSX that enhance security. Security teams can protect the data center traffic across virtual, physical, containerized, and cloud workloads. The security capabilities are always present in the infrastructure and are quickly configurable. Further, no one can tamper with the security controls because they reside in the hypervisor, effectively decoupling the controls from your workloads.
Workloads come in various form factors like virtual machines, containers, and physical servers. In addition, workloads are hosted in different environments like on-premises, native cloud, or managed cloud. The heterogeneity of the workload form factor and deployment type further challenges the organizations regarding security coverage, policy consistency, number of platforms to be managed, and overall operational simplicity. The requirement of an organization is to have an operationally simple platform that provides consistent policy across virtual machines, containers, physical servers, and native cloud workloads without compromising the application and data security.
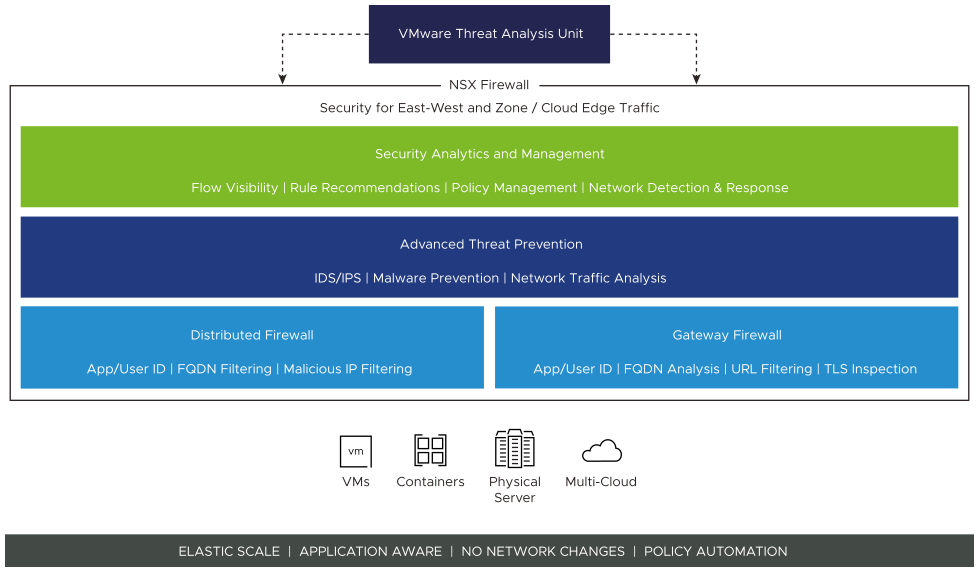
NSX has a distributed architecture. Security enforcement controls are located at the virtual network interface of each workload and provide a granular mechanism to police traffic flows. There is no centralized appliance that limits security capacity, and you do not need to artificially hairpin the network traffic to a network security stack. As NSX is integrated into the virtualization infrastructure, it has visibility into all applications and workloads. NSX uses this visibility to derive rich application context, closely track the life cycle of workloads and automate security policy management.
NSX Distributed Firewall (DFW) is a distributed, scale-out internal firewall that protects all East-West traffic across all workloads without network changes, thereby radically simplifying the security deployment model. It includes a stateful L4-L7 firewall, an intrusion detection/prevention system (IDS/IPS), network sandbox, and behavior-based network traffic analysis. With the NSX Firewall, you can protect the data center traffic across virtual, physical, containerized, and cloud workloads from internal threats and avoid damage from threats that make it past the network perimeter.
NSX Gateway Firewall is instantiated per gateway and is supported at both Tier-0 and Tier-1. The Gateway Firewall provides firewalling services and other services that cannot be distributed such as NAT, DHCP, VPN, and load balancing, and needs the services router component of the gateway. Gateway firewall works independently of NSX DFW from a policy configuration and enforcement perspective, although you can share objects from the DFW.
NSX Intelligence, a security analytics and policy management solution, automatically determines the communication patterns across all types of workloads, makes security policy recommendations based on those patterns, and checks that traffic flows conform to the deployed policies.