You can manage the rate at which NSX IDS/IPS events are generated for system signatures by configuring Thresholds and Rate Filters.
Without setting threshold parameters, each time malicious traffic matches a rule, the corresponding signature generates an IPS event based on the action defined for that rule. By configuring a Threshold for a signature, you control how frequently the signature generates an IPS event. Additionally, you can adjust the rule’s action dynamically, changing the response when specific conditions are met, which helps protect workloads from malicious traffic in real time.
Starting with NSX 4.2.1, you can configure Thresholds in system signatures that are running IDPS bundle version 2406 or later.
This feature is supported only on bundles version 2406 or higher that have been downloaded after the upgrade. Additionally, custom signatures do not support Thresholds. The Default signature bundle does support Thresholds if you have newly installed NSX 4.2.1. The Default signature bundle does not support Thresholds if you upgrading to NSX 4.2.1.
Before configuring thresholds and rate filters for a signature, ensure you understand the parameters involved in setting up a threshold for a signature.
Threshold: Define a minimum threshold for a rule before an alert is triggered. For example, setting a threshold count of 10 means the IDS/IPS will generate an alert only after the rule matches 10 times. For example, if the threshold is set to 10, the system will only generate an alert if it receives 10 or more inbound emails from the same server within a one-minute time period.
alert tcp !$HOME_NET any -> $HOME_NET 25 (msg:"ET POLICY Inbound Frequent Emails - Possible Spambot Inbound"; \ flow:established; content:"mail from|3a|"; nocase; \ threshold: type threshold, track by_src, count 10, seconds 60; \ reference:url,doc.emergingthreats.net/2002087; classtype:misc-activity; sid:2002087; rev:10;)
Limit: Use this option to prevent alert flooding. When set to a limit of N, the system will generate no more than N alerts within the specified time frame. For example, if the limit is set to 1, the system will generate at most one alert per host within a three-minute period when MSIE 6.0 is detected.
alert http $HOME_NET any -> any $HTTP_PORTS (msg:"ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk"; \ flow:to_server,established; content:"|0d 0a|User-Agent|3a| Mozilla/4.0 (compatible|3b| MSIE 6.0|3b|"; \ threshold: type limit, track by_src, seconds 180, count 1; \ reference:url,doc.emergingthreats.net/2010706; classtype:policy-violation; sid:2010706; rev:7;)
Both: This type is a combination of the “threshold” and “limit” types. It applies both thresholding and limiting. For example, a maximum of one alert will be generated if the signature is triggered five times within 360 seconds.
alert tcp $HOME_NET 5060 -> $EXTERNAL_NET any (msg:"ET VOIP Multiple Unauthorized SIP Responses TCP"; \ flow:established,from_server; content:"SIP/2.0 401 Unauthorized"; depth:24; \ threshold: type both, track by_src, count 5, seconds 360; \ reference:url,doc.emergingthreats.net/2003194; classtype:attempted-dos; sid:2003194; rev:6;)
For example, in the following code, you want to limit incoming connections to your SSH server. Rule 888 generates an alert for SYN packets directed to the SSH port. If an IP address triggers this rule 10 times or more within 60 seconds, the rate filter will switch the action to drop for future matching traffic. The rate filter expires after 5 minutes.
rate_filter gen_id 1, sig_id 888, track by_src, count 10, seconds 60, \ new_action drop, timeout 300
Prerequisites
IDPS bundle version selected must be v2406 or later
Procedure
- From the NSX Manager go to the > (under Policy Management section).
- On the IDS/IPS & Malware Prevention page, go to Signature Management tab and select System Signature.
- Select a rule, click the three dots and select Edit Action Threshold.
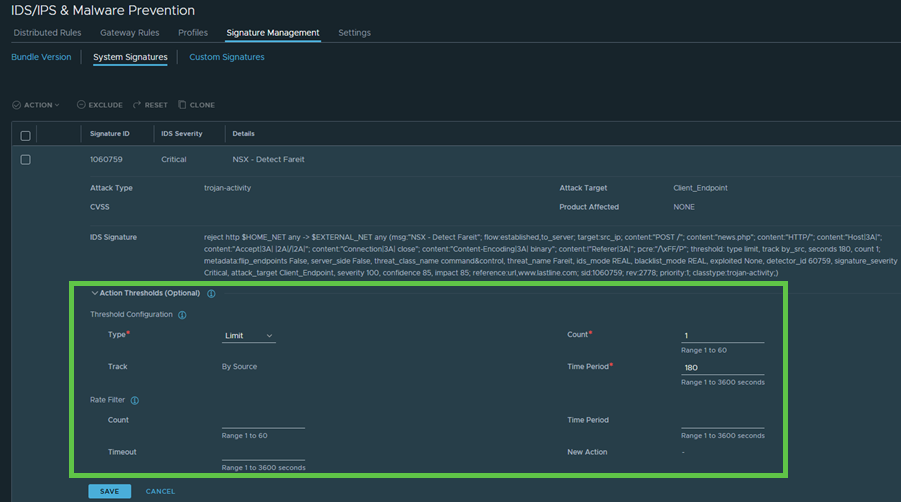
- Expand the Action Thresholds section.
- In the Threshold Configuration, set the following fields:
- Type: You can choose between Limit, Threshold, or a combination of both. By default, the Limit option is set as the threshold type for every signature.
- Count: Configure the number of rule matches required for the threshold to trigger an event in the IDPS. The available range is from 1 to 60.
- Track: By default, the IPS monitors and tracks IP addresses originating from the source.
- Time Period: Specifies the time period within which the rule must reach the defined count. The available range is from 1 to 3600 seconds.
- In the Rate Filter section, set the following fields:
- Count: Configure the number of rule matches required to trigger the rate filter, after which the new action is applied to the traffic. The available range is from 1 to 60.
- Time Period: This parameter defines the duration in which the count must be reached. The available range is from 1 to 3600 seconds.
- Timeout: This parameter defines the duration in which the rate filter stays active. The range is from 1 to 3600 seconds.
- New Action: By default, the new action is configured to Drop.
- Click Save.
- Click Publish.
- View the signature metadata to see the new threshold configuration.