NSX Service Insertion framework allows insertion of security services as add-ons to NSX. NSX provides interfaces to define, register and deploy add on security services. Service Insertion allows addition of network and endpoint security services to NSX.
NSX Network Introspection, previously known as NetX, uses Service Insertion for installation, configuration of third party network security services. Refer to the Network Introspection section.
NSX Endpoint Protection, NSX Distributed Malware Prevention use a combination of Service Insertion and Guest Introspection framework to provide endpoint security.
Service Insertion
- Define the nature of security service they can provide, for example, Networking, Endpoint, Malware Prevention.
- Allow classification of security levels provided by the security service. E.g. Basic, Normal, Comprehensive or Silver, Gold, Platinum etc. This is defined by the provider.
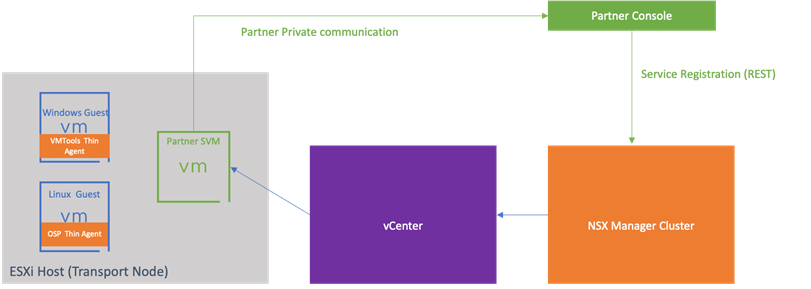
- Allows defining an OVF specification that includes multiple form factors for the Partner SVM depiceted in the diagram.
Service Insertion framework uses vCenter’s ESXi Agent Manager (EAM) API to deploy provider given security service OVF. OVF gets deployed to the vSphere compute cluster specified as deployment target. One instance of the OVF gets deployed on each host in the target cluster. This is called Service Instance. The VM that is deployed on the host is Service VM.
Service VM characteristics
- Service VM is started before starting any workload VM.
- Cannot be shut down.
- Restarts if shut down.
- Pinned to the host so cannot be migrated to any other host.
Security service providers that use Service Insertion framework to plug in their service need to define their network requirements in the provided OVF. If the solution requires external network connectivity then OVF is required to specify additional networks and administrators are required to configure this network during service deployment.
Service Insertion framework relies on NSX Manager and vCenter to help deploy security services. NSX Service Insertion API is public and partners developing their security solutions are required to adhere to this API.
Key Concepts of Service Insertion
Service Definition: Partners define services with these attributes: name, description, supported form factors, deployment attributes that include network interfaces, and appliance OVF package location to be used by the SVM.
Service Profiles and Vendor Templates: Partners register vendor templates which expose protection levels for policies. For example, protection levels can be Gold, Silver, or Platinum. Service Profiles can be created from Vendor Templates, which allow the NSX administrators to name the Vendor Templates according to their preference. For services other than those of Guest Introspection, the Service Profiles allow further customization using attributes. The Service Profiles can then be used in the Endpoint Protection policy rules to configure protection for virtual machine groups defined in NSX. As an administrator, you can create groups based on VM name, tags, or identifiers. Multiple Service Profiles can optionally be created from a single Vendor Template.
Guest Introspection
Security services that are endpoint centric or require intelligence from endpoint file, network, process et.al. activities should use Guest Introspection framework in addition to Service Insertion.
Guest Introspection framework provides necessary interfaces that a security solution (Deployed using service insertion) can consume to gather security context from within the endpoint. Guest Introspection provides a rich context API that provides various types of events based on IO activities on the guest VM. These include but are not limited to file, network, process, registry, system events. API allows gathering additional relevant information in the context of the event. API also allows methods to gather information on demand. There are interfaces provided to take remediation actions on the endpoint such as deny access to a file or delete a file found to be malicious.
Guest Introspection framework relies on use of Guest Introspection thin agents deployed on the Guest VMs. Guest Introspection thin agents are available for Windows and Linux operating systems. On Windows they are packaged and delivered with VMTools. The Linux thin agent is available as part of the operating system specific packages (OSPs). The packages are hosted on VMware packages portal.
The Guest Introspection API is made available to security service providers under an NDA. Security service providers are required to adhere to the API requirements and are required to certify their services with VMware. VMware certified security solutions provided by security providers can then be used as add-on security services with NSX.
- The component that relays events and information gathered by the guest thin agents to the security solutions that consume Guest Introspection library is called Context MUX.
- This component also relays security profile based on a policy rule for a protected VM to its protecting security solution. E.g. If a customer selects a basic protection profile and applies to a VM. Context MUX propagates this VM id and corresponding profile information to the security solution.
- Another component that is part of the Guest Introspection framework runs as part of OpsAgent on each host. This component is used to consume NSX defined security configuration consisting of policy based on profiles, rules and groups. It consumes the security configuration and provides to Context MUX. Context MUX uses this information to decide what guest VMs should be mapped to what security services for protection.
Key concepts for Guest Introspection
File Introspection driver: Is installed on the guest VM, intercepts file and process activity on the guest VM.
Network Introspection driver: Is installed on the guest VM, intercepts the network traffic and user activity on the guest VM.