You can view the details for a specific campaign by clicking the hyperlinked campaign name on the Campaigns page.
This page provides the detailed information for the campaign.
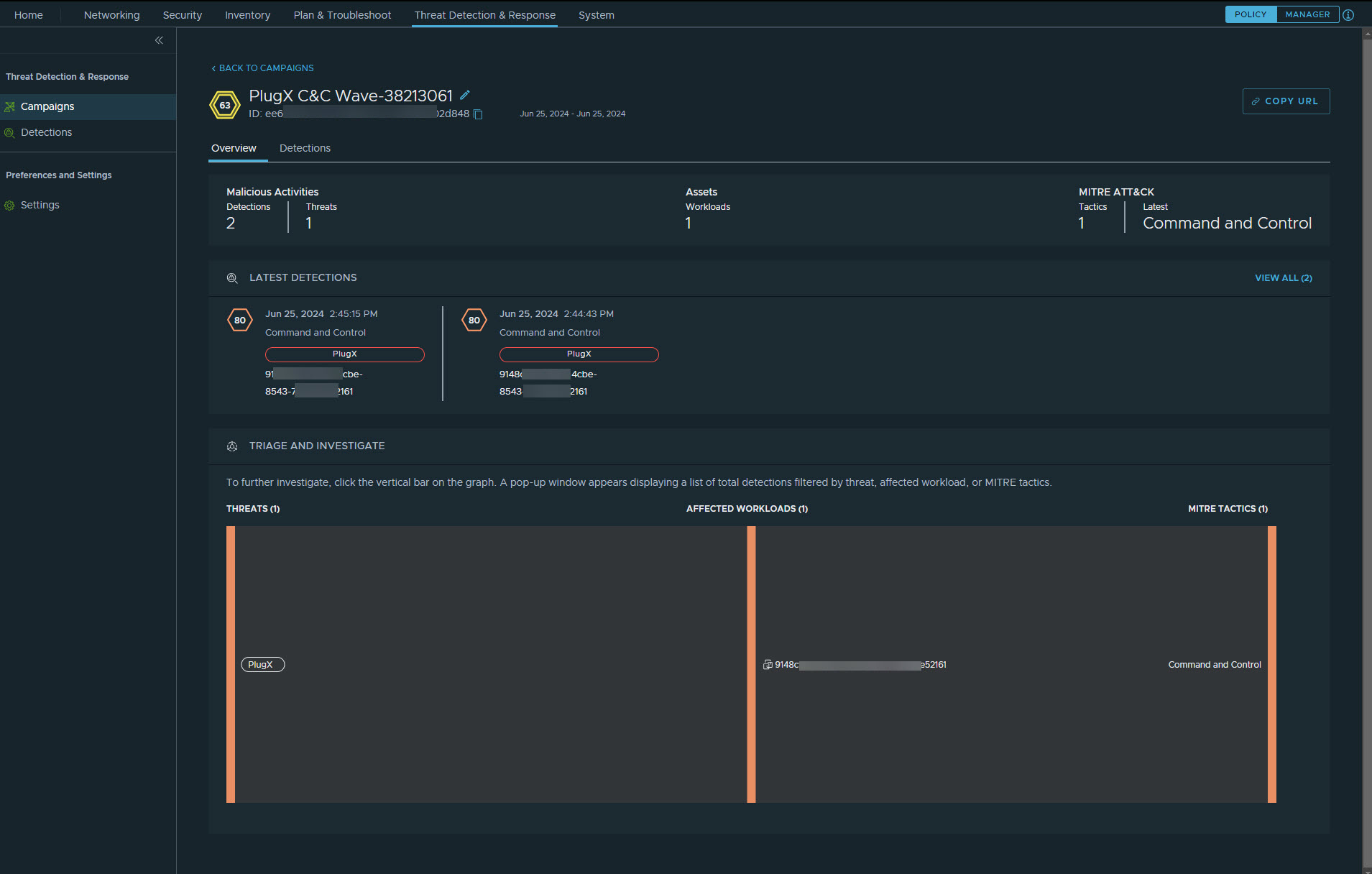
At the top of the page are the impact score, campaign name, campaign UUID, and campaign timeline.
-
To edit the campaign name, click the pencil icon
 at the end of the campaign name.
at the end of the campaign name.When a campaign is created, its name is automatically generated by using a heuristic based on the malicious activity that is initially correlated. You can rename the campaign name to make it more meaningful and recognizable.
- Click Copy URL to copy the link address for the campaign.
Triage and Investigate : If you want to investigate further, click the vertical bar on the graph. A pop-up window appears displaying a list of total detections filtered by threat, affected workload, or MITRE tactics. After you are done, close the pop-up window.
Overview
By default, the Overview tab is displayed. This tab provides the following information:
- Malicious Activities: Displays the total count of detections and threats.
- Assets: Displays the total count of the affected workloads and sites.
- MITRE ATT&CK: Provides the overview details of the MITRE ATT&CK tactics and stages identified in the campaign:
- Tactics: Displays the total number of MITRE tactics identified in the campaign.
- Latest: This refers to the latest stage of the MITRE framework that was detected in the campaign and not the latest stage in the campaign timeline.
- Latest Detections: Provides a list of the latest detections.
Detections
Click the Detections tab to see the full list of detections in the campaign.