SSL profiles configure application-independent SSL properties such as, cipher lists and reuse these lists across multiple applications. SSL properties are different when the load balancer is acting as a client and as a server, as a result separate SSL profiles for client-side and server-side are supported.
Client-side SSL profile refers to the load balancer acting as an SSL server and stopping the client SSL connection. Server-side SSL profile refers to the load balancer acting as a client and establishing a connection to the server.
- default-balanced-client-ssl-profile
- default-balanced-server-ssl-profile
- default-high-compatibility-client-ssl-profile
- default-high-compatibility-server-ssl-profile
- default-high-security-client-ssl-profile,
- default-high-security-server-ssl-profile.
For NSX 4.1.x versions, the NSX Manager could communicate with an NSX LB virtual server if the virtual server was configured with the default-balanced-client-ssl-profile and ECDSA certificates. The NSX Manager was not able to communicate with an NSX LB virtual server if the virtual server was configured with the default-balanced-client-ssl-profile and RSA certificates, because the balanced cipher group did not support the required cipher TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384. As a result, the communication between the NSX Manager and vIDM LB VIP with such a configuration had been broken since NSX 4.1.x. Starting with NSX 4.2, the cipher TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 is also added to the balanced and high compatibility client/server profiles to support the communication between the NSX Manager and a load balancer virtual server for vIDM. With this new addition, you no longer need to create a custom profile and add the cipher TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 as a workaround for supporting the communication between the NSX Manager and a vIDM LB VIP.
SSL session caching allows the SSL client and server to reuse previously negotiated security parameters avoiding the expensive public key operation during the SSL handshake. SSL session caching is disabled by default on both the client-side and server-side.
SSL session tickets are an alternate mechanism that allows the SSL client and server to reuse previously negotiated session parameters. In SSL session tickets, the client and server negotiate whether they support SSL session tickets during the handshake exchange. If supported by both, server can send an SSL ticket, which includes encrypted SSL session parameters to the client. The client can use that ticket in subsequent connections to reuse the session. SSL session tickets are enabled on the client-side and disabled on the server-side.
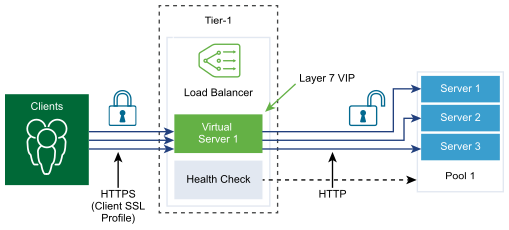
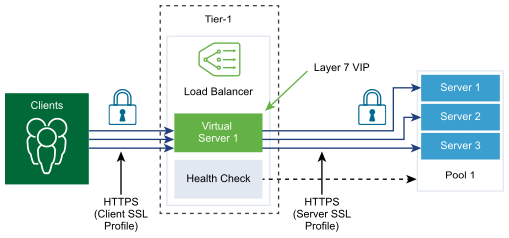
Procedure
- With admin privileges, log in to NSX Manager.
- Select .
- Select a Client SSL Profile and enter the profile details.
Option Description Name and Description Enter a name and a description for the Client SSL profile. SSL Suite Select the SSL Cipher group from the drop-down menu and available SSL Ciphers and SSL protocols to be included in the Client SSL profile are populated. Balanced SSL Cipher group is the default.
Session Caching Toggle the button to allow the SSL client and server to reuse previously negotiated security parameters avoiding the expensive public key operation during an SSL handshake. Tags Enter tags to make searching easier. You can specify a tag to set a scope of the tag.
Supported SSL Ciphers Depending on the SSL suite, you assigned the supported SSL Ciphers are populated here. Click View More to view the entire list. If you selected Custom, you must select the SSL Ciphers from the drop-down menu.
Supported SSL Protocols Depending on the SSL suite, you assigned the supported SSL protocols are populated here. Click View More to view the entire list. If you selected Custom, you must select the SSL Ciphers from the drop-down menu.
Session Cache Entry Timeout Enter the cache timeout in seconds to specify how long the SSL session parameters must be kept and can be reused. Prefer Server Cipher Toggle the button so that the server can select the first supported cipher from the list it can support. During an SSL handshake, the client sends an ordered list of supported ciphers to the server.
- Select a Server SSL Profile and enter the profile details.
Option Description Name and Description Enter a name and a description for the Server SSL profile. SSL Suite Select the SSL Cipher group from the drop-down menu and available SSL Ciphers and SSL protocols to be included in the Server SSL profile are populated. Balanced SSL Cipher group is the default.
Session Caching Toggle the button to allow the SSL client and server to reuse previously negotiated security parameters avoiding the expensive public key operation during an SSL handshake. Tags Enter tags to make searching easier. You can specify a tag to set a scope of the tag.
Supported SSL Ciphers Depending on the SSL suite, you assigned the supported SSL Ciphers are populated here. Click View More to view the entire list. If you selected Custom, you must select the SSL Ciphers from the drop-down menu.
Supported SSL Protocols Depending on the SSL suite, you assigned the supported SSL protocols are populated here. Click View More to view the entire list. If you selected Custom, you must select the SSL Ciphers from the drop-down menu.
Session Cache Entry Timeout Enter the cache timeout in seconds to specify how long the SSL session parameters must be kept and can be reused. Prefer Server Cipher Toggle the button so that the server can select the first supported cipher from the list it can support. During an SSL handshake, the client sends an ordered list of supported ciphers to the server.