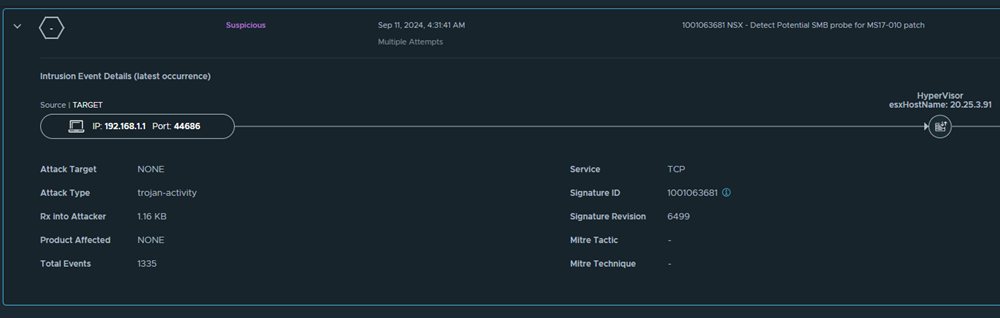
In this example scenario, consider that you want to create a custom signature that detects SMB traffic indicative of probing attempts targeting vulnerabilities in systems unpatched against MS17-010—potentially exploited by malware such as WannaCry.
Prerequisites
Ensure that the uploaded custom signatures use only the supported Suricata keywords. Using any unsupported keywords will render the signature invalid, as it will be unable to parse keywords that fall outside the approved list.
Procedure
- You can upload a custom signature in one of the following ways:
If you have a custom signature bundle already uploaded, first export the bundle in .zip format to your local system. Then, add the new custom signature to the bundle and re-upload it.
You can manually add a custom signature by adding the IDS signature.
Clone system signatures and customize the signature.
- Let’s manually add the custom signature. In the NSX Manager UI, go to (under Policy Management section), select .
- Click +Add and Manually Add.
- In the Manually Add Custom Signatures window, click Add Signature, type or paste in the custom signature, then click ADD. You can add more signatures, by clicking Add Signature. After adding all signatures you want to be part of the bundle, click Save. For example,
alert tcp $HOME_NET any -> $EXTERNAL_NET 445 (msg:"NSX - Detect Potential SMB probe for MS17-010 patch"; flow:established,to_server; target:src_ip; content:"|00|"; depth:1; content:"|FF|SMB"; within:7; content:"|23 00 00 00 07 00 5C|PIPE|5C 00|"; within:110; threshold: type limit, track by_src, seconds 10, count 10; metadata:ll_expected_verifier default, flip_endpoints False, server_side False, threat_class_name Suspicious Network Interaction, threat_name Potential SMB probe for MS17-010 patch, ids_mode INFO, blacklist_mode DISABLED, exploited None, confidence 50, severity 20, detector_id 63681, signature_severity Informational; reference:url,www.lastline.com; classtype:trojan-activity; sid:1063681; rev:6499; priority:5; flowbits:set,CS.LL.verifier_tcp_successful; flowbits:set,CS.LL.verifier_tcp_failed; flowbits:set,CS.LL.verifier_tcp_blocked;)
- NSX IDS/IPS automatically starts the validation process for the newly added signatures. The signature validator will assess the validity of the rule and classify it as Valid, Invalid, or Warning. By default, Warning signatures are excluded from the validation process. You must explicitly select them for inclusion if you want them to be pushed to transport nodes. Invalid signatures are published but are only stored on NSX Manager and are not pushed to transport nodes. However, you must resolve any issues with Invalid signatures and re-validate them before they can be published.
- Click Publish.
- Verify that you can view the published signatures on Transport Nodes.
- On the IDS/IPS & Malware Prevention page, select Profiles. You can either add a new custom profile or edit an existing one to include custom signatures. When adding or editing a profile, ensure that you assign severities to the custom signatures.
- Verify that rules are applied with the custom signature profile.
- When malicious traffic attempts to probe for vulnerabilities in systems that are unpatched against MS17-010, the IDS will generate an alert for suspicious activity.
- The Where Detected field lists VMs where probing attempts were made to exploit unpatched systems.
- Patch these VMs to avoid vulnerabilities in systems not patched against MS17-010.