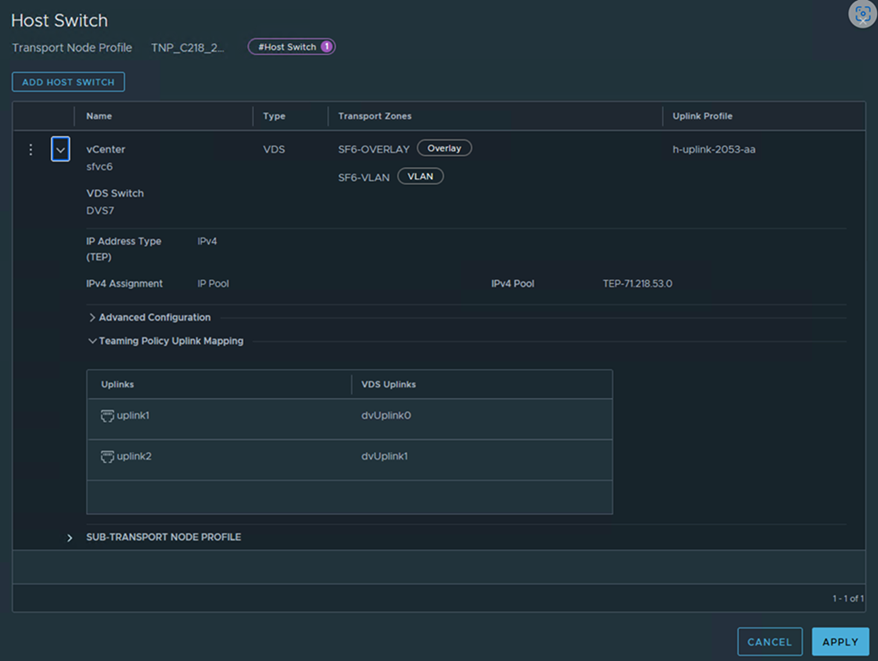
You can configure NSX on indivdual ESXi hosts
Prerequisites
- Verify that the individual host you want to prepare is powered on.
- Verify that the system requirements are met. See System Requirements.
- The reverse proxy service on all nodes of the NSX Manager cluster must be Up and running.
To verify, run get service http. If the service is down, restart the service by running restart service http on each NSX Manager node. If the service is still down, contact VMware support.
- If you deployed VMware vCenter on a custom port or a non-default port, apply these rules to NSX Manager:
- IPv4 rules must be applied on NSX Manager manually before starting the host preparation.
iptables -A INPUT -p tcp -m tcp --dport <CUSTOM_PORT> --tcp-flags FIN,SYN,RST,ACK SYN -j ACCEPTiptables -A OUTPUT -p tcp -m tcp --dport <CUSTOM_PORT> --tcp-flags FIN,SYN,RST,ACK SYN -j ACCEPT
- IPv6 table rules must be applied on NSX Manager manually before starting the host preparation.
ip6tables -A OUTPUT -o eth0 -p tcp -m tcp --dport <CUSTOM_PORT> --tcp-flags FIN,SYN,RST,ACK SYN -j ACCEPTip6tables -A INPUT -p tcp -m tcp --dport <CUSTOM_PORT> --tcp-flags FIN,SYN,RST,ACK SYN -j ACCEPT
- IPv4 rules must be applied on NSX Manager manually before starting the host preparation.
- (Host in lockdown mode) If your exception list for vSphere lockdown mode includes expired user accounts such as lldpvim-user, NSX installation on vSphere fails. This user automatically gets created on ESXi to talk to hostd to get the LLDP neighbor information and then gets deleted. Ensure that you delete all expired user accounts before you begin installation. For more information on accounts with access privileges in lockdown mode, see Specifying Accounts with Access Privileges in Lockdown Mode in the vSphere Security Guide.
Procedure
What to do next
Create a logical switch and assign logical ports. See the Advanced Switching section in the NSX Administration Guide.