After you have an NSX version 3.2 or later installed and all the deployment prerequisites are met, you can proceed to manually deploy the NSX Application Platform.
Prerequisites
You must meet all of the deployment prerequisites, including the Kubernetes cluster resources and form factor system requirements. See the Deployment Requirements for NSX Application Platform and Manual Deployment Requirements topics for details.
If you migrated your Security Intelligence 1.2.x traffic flow data, do not deploy the NSX Application Platform using the Evaluation form factor. Using the Evaluation form factor forces the system to deploy the NSX Application Platform without migrating your traffic flow data from the previous Security Intelligence 1.2.x installation and causes the loss of information about that previous installation.
Step 1: Prepare to Deploy
To deploy the NSX Application Platform, provide the Helm repository and Docker registry information.
When you do not have internet connectivity, you can configure the NSX Manager and Kubernetes guest cluster with an HTTP/HTTPS Proxy to retrieve the Helm repository and Docker registry information. The NSX proxy details are also shared with NSX Malware Prevention to connect to the cloud for sandbox analysis.
Private Harbor can be used to retrieve the Helm repository and Docker registry information. If private Harbor registry is used without internet, NSX Malware Prevention cannot be activated.
Prerequisites
Proxy Prerequisites
- If you do not have internet connectivity, configure the NSX proxy to route internet traffic. Make sure that the proxy is activated and port number is accurate. For HTTPS proxy, you must have a proxy server self-signed certificate available.
See the Configure Proxy Settings topic in the Operations and Management section of the NSX Administration Guide, which is delivered with the VMware NSX Documentation set.
- Add Proxy server certificate in NSX for HTTPS proxy. See Import a CA certificate topic under Importing and Replacing Certificates in the Certificates section of the NSX Administration Guide, which is delivered with the VMware NSX Documentation set.
- Verify that the proxy details are configured on the TKG Guest Clusters running in the vSphere Client so that worker nodes can access Docker images. See Configure HTTP Proxy Setting on the Supervisor by Using the vSphere Client.
- If you are using proxy, verify that the NSX Manager version is updated to 4.2.
This option is available only in the NSX Application Platform 4.2 release.
- If self-signed or Private CA certificate is used for the proxy server, the certificate should include Subject Alternative Name (SAN).
Private Harbor Prerequisites
- Add private Harbor private CA or self signed certificate in NSX. See Import a CA certificate topic under Importing and Replacing Certificates in the Certificates section of the NSX Administration Guide, which is delivered with the VMware NSX Documentation set.
- If self-signed or Private CA certificate is used for the private Harbor registry, the certificate should include Subject Alternative Name (SAN).
Procedure
Step 2: Provide Configuration Details
To deploy the NSX Application Platform, you must provide the configuration information about the TKG Cluster on Supervisor or Upstream Kubernetes cluster resources that your infrastructure administrator created for you.
You must have the kubeconfig file that you obtained from your infrastructure administrator. This file contains configuration information for your TKG Cluster on Supervisor or Upstream Kubernetes environment and provides access information.
Procedure
Step 3: Precheck the Platform
The system needs to check the configuration information that have been obtained before proceeding with the NSX Application Platform deployment.
Procedure
Step 4: Review & Deploy
The NSX Application Platform deployment wizard gives you the chance to review and edit any of the configuration details that the system has obtained.
Procedure
Results
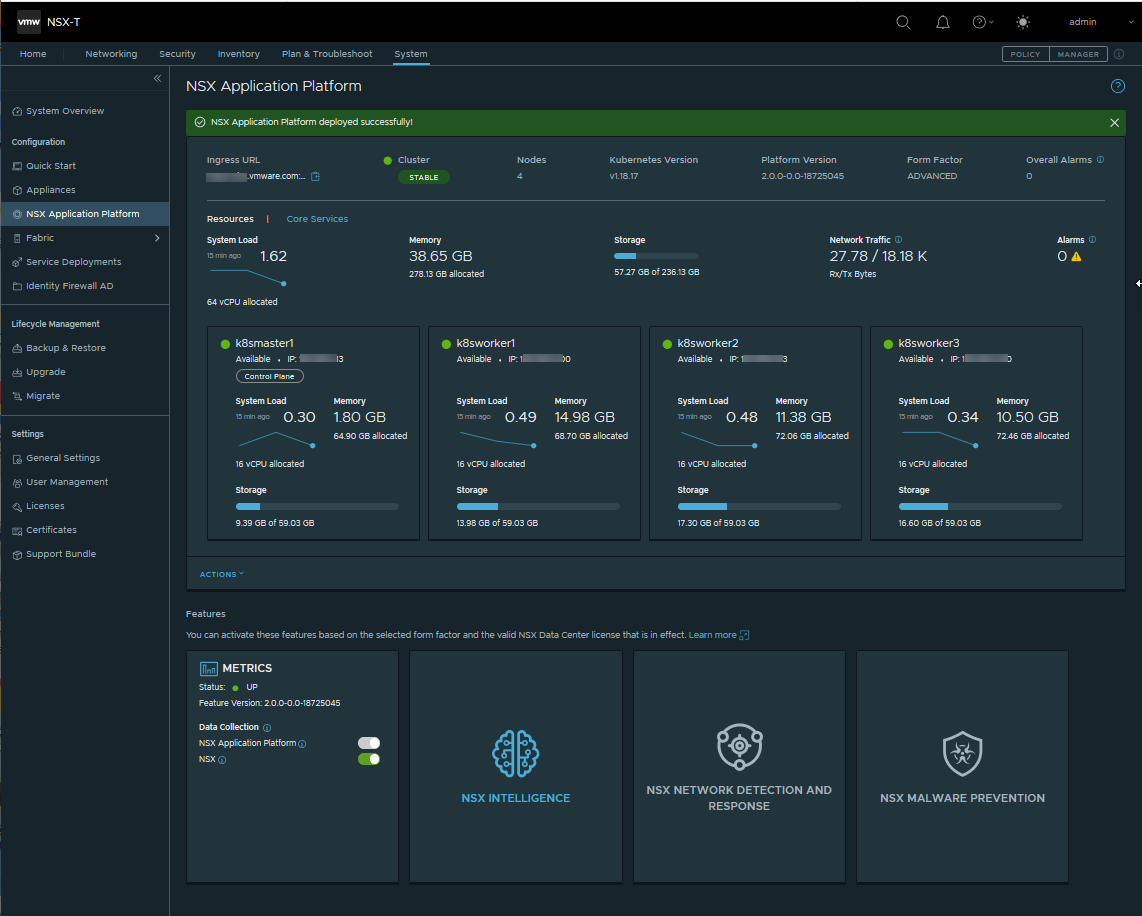
What to do next
You can now activate any of the available NSX features that can be hosted on the NSX Application Platform and is available for the form factor and NSX license that you are currently using. See #GUID-94C2F705-5745-4D6F-B1CA-8CDC1C7DEC7F for more information.