Rules are imposed on networks to restrict access to specific services. Rules should be specific to ensure that only minimal access is granted.
Rules combine protocol (TCP, UDP, ICMP) and target port. You can list multiple predefined network and custom services in a single rule. Finally, only one rule can be applied per network, so creating and tailoring rules for network access is recommended. Try to balance reuse and prescriptiveness when creating rules.
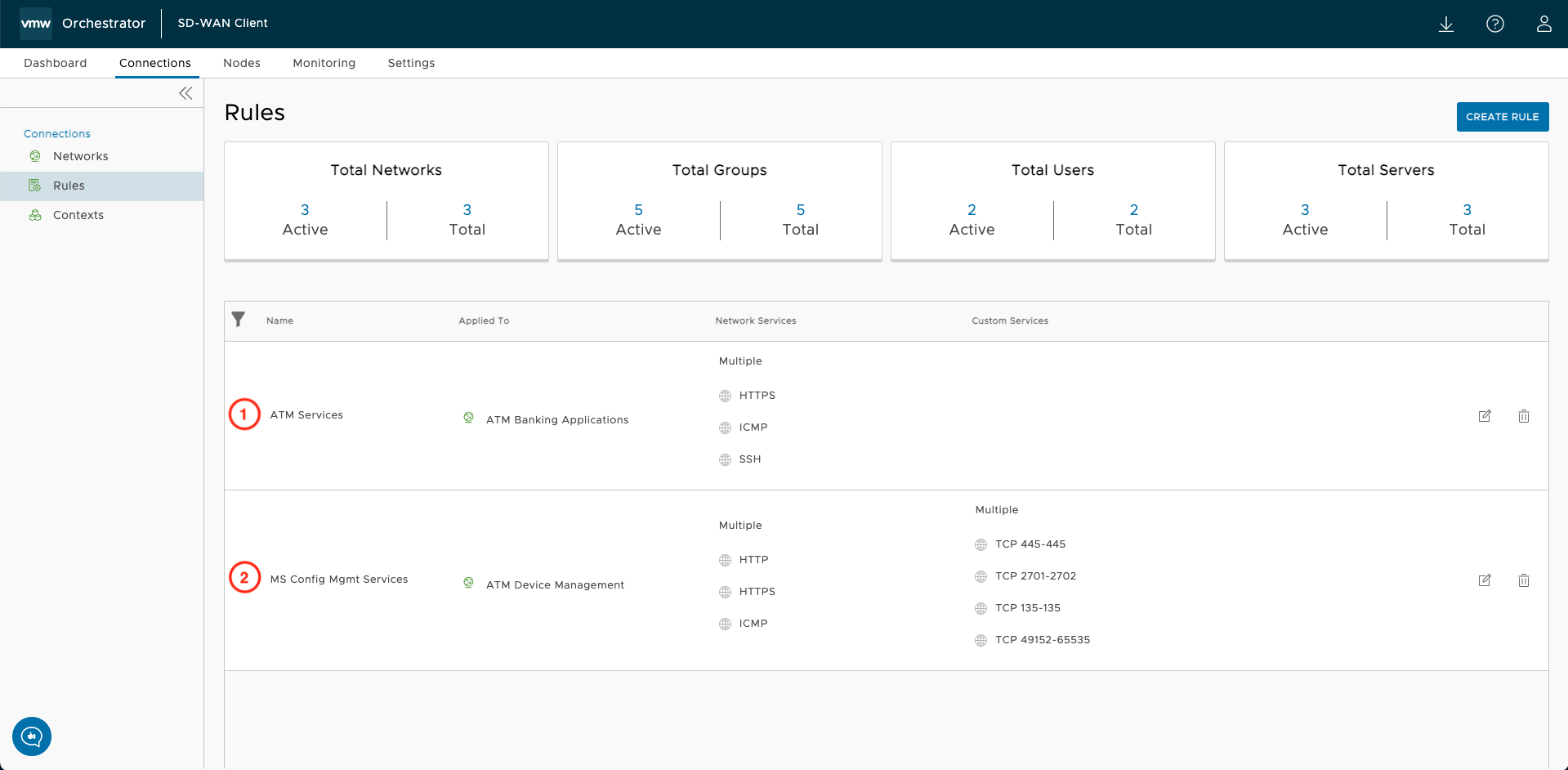
- The first rule, "ATM Services," uses only pre-defined network services HTTPS, ICMP, and SSH. This rule is representative of the services an ATM application might need access to, but it should be updated to reflect what your organization's actual ATM application relies on. To see which ports and protocols are associated with pre-defined network services, consult the configuration guide.
- The second rule is for "MS Config Mgmt Services." This rule combines pre-defined network services and custom services. When your application's service ports are not in the system, you can manually configure them using custom services. You can also include a range of ports, which eases the configuration burden when a service relies on a swath of ports.