Networks combine nodes, groups, rules, and contexts to create an access policy rule that determines if a connection between two endpoints should be established.
It would be best to consider networks in the SD-WAN Client solution as more than IP connectivity. These are policy-driven constructs more akin to an access control list entry or a sequence in a route map. For highly restrictive networks, like the ones that support ATMs, it is ideal to be as specific as possible in authorizing access to the fabric. Only devices meeting the specified criteria will be allowed to establish a connection. Any device not meeting the criteria will not have a connection established, thus blocking it from the network entirely.
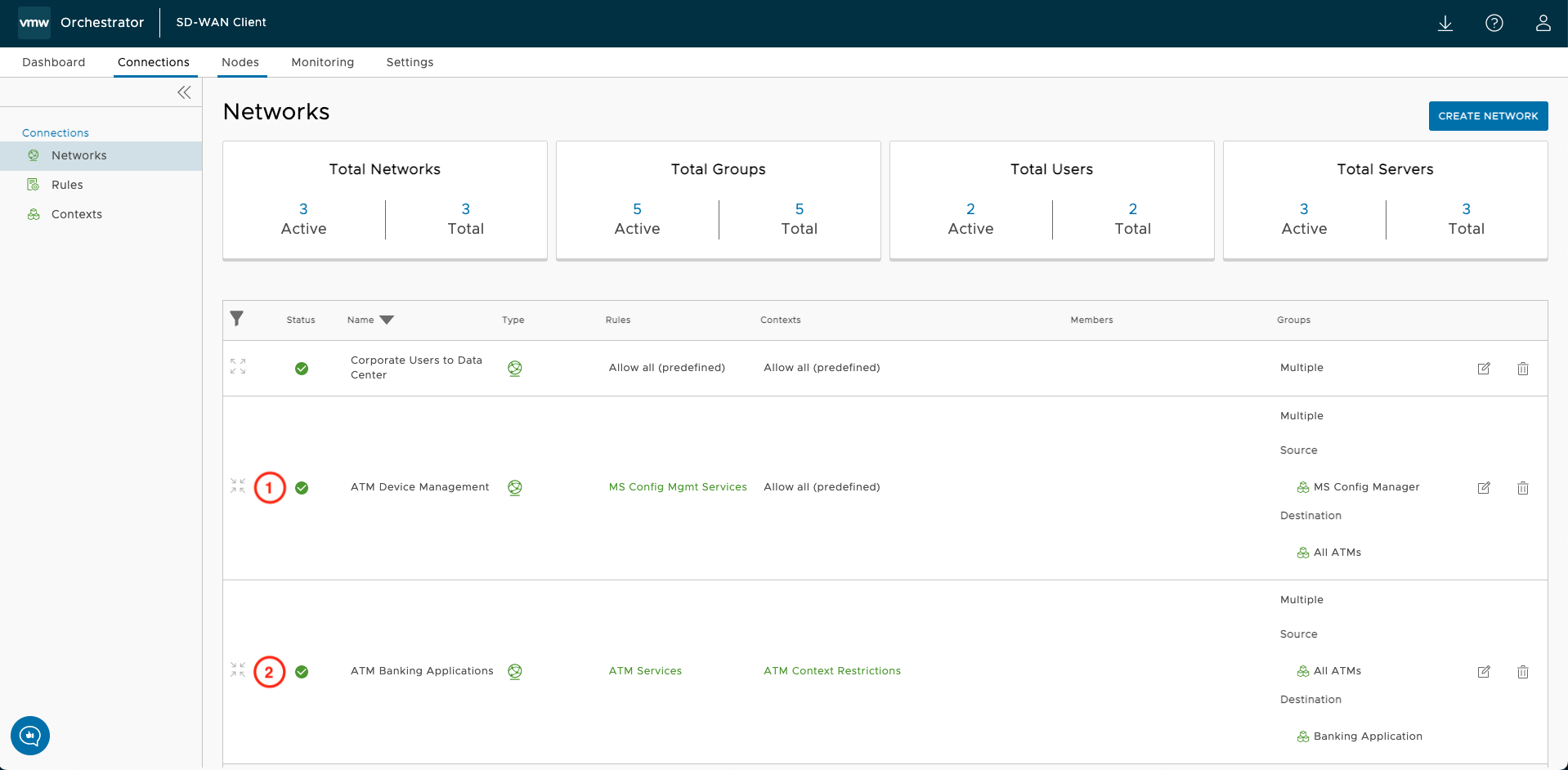
-
- The type is set to hub and spoke. The selection of this network type is based on the required data flow. Because traffic will originate from the Microsoft Configuration Manager server(s) to the ATM(s), but ATM(s) will not be initiating similar configuration management connections to the servers. Hub and spoke is ideal for this type of communication. The flow is unidirectional that allows for return traffic from the destination.
- The rule applied to this network includes only the necessary services for MS Configuration Management Services to work. The rule ensures only the minimum access to manage the endpoint is provided, nothing more.
- The applied context checks to see if the host meets the criteria before admitting it to the network. In this case, none is selected, and no additional checks will be made for admission. The decision to omit a context for a network is up to your desired security posture. Most likely, the configuration servers are behind several layers of defense and are tightly controlled resources. Location, time of day, OS, and endpoint posture validation may not offer much, if any, increase in security posture.
- Members only apply when a node is selected individually. Since we use groups to identify sources and destinations, not individual nodes, this column will be blank.
- The two groups used in this network are the MS Config Manager and All ATMs. The correct nodes have been assigned to their respective group, so it is easy to reference these two objects versus the potential tens of thousands of ATMs and a handful of Microsoft Configuration Manager servers. As depicted, the MS Config Manager is the source, and All ATMs are the destination.
- The second network is ATM Banking Applications.
- This network is also a hub and spoke type. The network type aligns with the communication flow. The ATM will initiate communication to the banking application, and not the other way around. If the banking application needs to initiate communication with the ATM, a third network should be created to allow this flow.
- The rule here includes only the necessary services the ATM needs access to. The referenced rule, ATM Services, ensures that no other access is granted to the host with the banking application installed. Granular access control ensures you are not unnecessarily exposing your network to risk.
- The applied context checks to see if the host meets the criteria before admitting it to the network. The checks included in ATM Context Restrictions include geography of origin, OS type, and presence of AV and a screensaver password on the ATMs. The ATM cannot connect to the banking application if any of those checks fail.
- It is recommended to periodically review your configuration for any “shadow networks” that might permit access when it should otherwise be denied. Networks are processed in a top-down order until a match is found. If you happen to configure a Network after this one that is less restrictive but still permits the same source/destinations to communicate, then traffic will be permitted when it should have been denied.
- Members only apply when a node is selected individually. Since we use groups to identify sources and destinations, not individual nodes, this column will be blank.
- The two groups used in this network are the Banking Applications and All ATMs. The correct nodes have been assigned to their respective group, so it is easy to reference these two objects versus the potential tens of thousands of ATMs and a handful of Banking Applications servers. As depicted, All ATMs are the source, and Banking Applications are the destination.