The data center is integral to an organization's operations.
Because of its prominent role in the business, it is a tightly controlled resource governed by multiple groups within the organization. Cross-functional team collaboration will be necessary to ensure the data center is ready for the SD-WAN Client. While the following steps do not need to be followed in order, they must all be accomplished before proceeding to the next deployment phase.
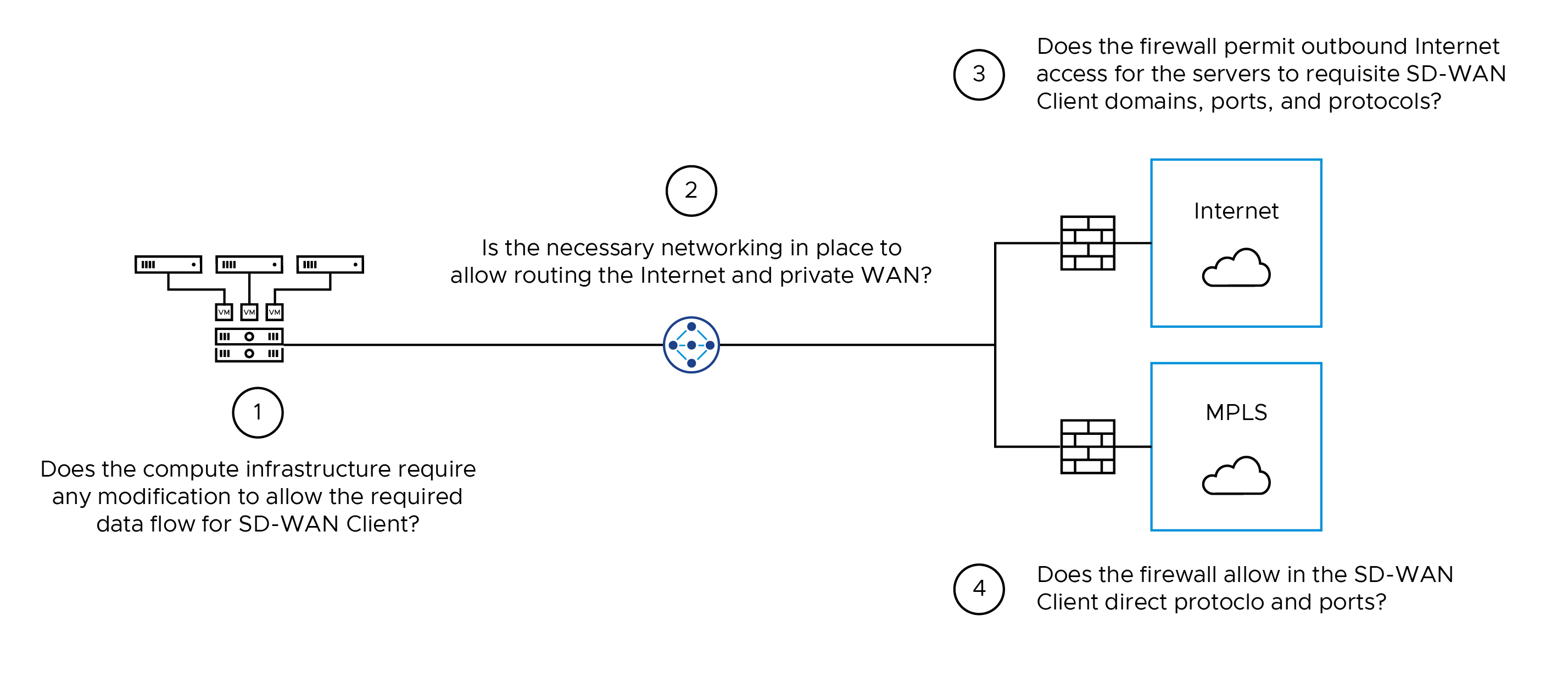
- Examine the compute infrastructure. Because the servers hosting the banking applications are already online and operational, minimal changes should be needed here. However, advanced security capabilities like NSX Gateway Firewall might be in the environment. If NSX Gateway Firewall exists, security rules will be required for the external firewall(s) in the data center.
- Again, the routing and switching infrastructure is most likely in place. And the routing protocols should forward traffic to the correct destination, be it Internet or private WAN. However, not all organizations use straightforward routing designs for numerous reasons. This check ensures you have the required IP reachability to establish management, control plane, and data plane connections.
- The Internet firewall performs two critical functions: NAT and security policy enforcement. Because the SD-WAN Client is designed to operate over NAT, you can simply rely on port address translation (PAT). All SD-WAN Client Servers can be overloaded to a single IP address without issue. The second piece is security. Only outbound firewall rules are needed here. You can specify the domains, ports, and protocols required by the SD-WAN Client solution to work. Do not use SSL Inspection on the data plane connections, as it is not possible to intercept these connections.
- The private WAN (MPLS) might sit behind a firewall zone in the data center. If that is the case, allowing data plane traffic between SD-WAN Client Servers and ATMs will be necessary. The direct, encrypted communication between Servers and ATMs will occur over UDP 10,000-60,000. The firewall will require a rule to allow this traffic bidirectionally. Otherwise, it will hairpin through an Optimization Relay on the Internet, creating a suboptimal traffic flow.