LAN-Side NAT Rules allow you to NAT IP addresses in an unadvertised subnet to IP addresses in an advertised subnet. For both the Profile and Edge levels, within the Device Settings configuration, LAN-side NAT Rules has been introduced for the 3.3.2 release.
Before you begin:
- LAN-side NAT Rules can be configured at the Profile level or the Edge level. To configure at the Edge level, make sure the Enable Edge Override checkbox is checked.
- LAN-side NAT supports traffic over VCMP tunnel. It does not support underlay traffic.
Use Case #1:
In this scenario, a third-party has assigned multiple non-overlapping subnets to a customer's site. The server in the customer's data center recognizes traffic from this third-party by a single IP address at any given site.
- VLAN1 = 192.168.1.0/24 - Do not advertise
- Static route 192.168.5.0/24 - Do not advertise
- Static route 192.168.7.0/24 - Do not advertise
- Static route 57.24.12.0/24 - Do not advertise
- Static route 172.16.24.0/24 - Advertise
- New rule: LAN-side NAT 192.168.1.0/24 -> 172.16.24.4/32
Use Case #2:
In this scenario, the LAN subnet is 192.168.1.0/24. However, this is an overlapping subnet with other sites. A unique subnet of equal size, 172.16.24.0/24 has been assigned to use for VPN communication at this site. Traffic from the PC must be NAT'd on the Edge prior to doing the route lookup, otherwise the source route will match 192.168.1.0/24 which is not advertised from this Edge and traffic will drop.
- VLAN1 = 192.168.1.0/24 - Do not advertise
- Static route 172.16.24.0/24 - Advertise
- New rule: LAN-side NAT 192.168.1.0/24 -> 172.16.24.0/24
- From the VCO navigational panel, go to Configure > Edges.
- In the Device Settings tab screen, scroll down to the LAN-Side NAT Rules area.
- In the LAN-Side NAT Rules area, complete the following: (See the table below and the Use Cases described above for more information about the fields in the LAN-Side NAT Rules area).
- Enter an address for the Inside Address textbox.
- Enter an address for the Outside Address textbox.
- Choose either Source or Destination from the Type drop-down menu.
- Type a description for the rule in the Description textbox (optional).
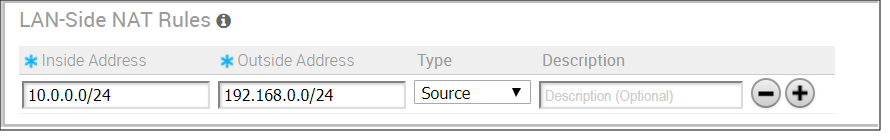
LAN-side NAT Rules (Filed Name) Type Description Inside Address text box IPv4 address/prefix, Prefix must be 1-32 The "inside" or "before NAT" IP address (if prefix is 32) or subnet (if prefix is less than 32). Outside Address text box IPv4 address/prefix, Prefix must be 1-32 The "outside" or "after NAT" IP address (if prefix is 32) or subnet (if prefix is less than 32). Type drop-down menu Select either Source or Destination. Determine whether this NAT rule should be applied on the source or destination IP address of user traffic. Description text box Text Custom text box to describe the NAT rule.