The Edge Firewall primarily uses rules from the assigned Profile. Overriding Profile Firewall rules at the Edge level is an optional step.
Configure Edge Firewall
The Edge Firewall primarily uses rules from the assigned Profile. Overriding Profile Firewall rules at the Edge is an optional step.
Outbound Firewall Rules
At the Edge, Firewall Rules from the assigned Profile can be overridden using the Edge Firewall dialog shown below. Any Firewall override match value that is the same as any Profile Firewall rule, will override that Profile rule. You can create override rules in the same way as you create Profile rules (see Configure Profile Firewall).
Firewall Profiles are Segment aware. All Segments available for configuration are listed in the Configure Segment drop-down menu. When you choose a Segment to configure from the Configure Segments drop-down menu, the settings and options associated with that Segment appear in the Configure Segments area. Global Segment [Regular] is the default Segment.
For more information about Segmentation, see Configure Segments and Configure Edge Device.

Inbound Firewall Rules
Inbound firewall rules gives Internet clients access to servers connected to an Edge LAN interface. Access can be made available through either Port Forwarding Rules or 1:1 NAT (Network Address Translation) rules.
Port Forwarding Rules
Port forwarding rules enable you to configure rules to redirect traffic from a specific WAN port to a device (LAN IP/ LAN Port) within the local subnet. Optionally, you can also restrict the inbound traffic by an IP or a subnet. For the 3.3.2 release, the Inbound port forwarding rule can be configured with the Outside IP (which is on the same subnet of the WAN IP). See the example below.
Example
- If the source IP is 88.88.88.88 (from Internet), and it tries to reach 169.254.6.46 port 8888, it will port forward to 192.168.10.10 / port 80.
- If source IP is 99.99.99.99, and it tries to reach 169.254.6.46 port 8888 (same as above), it will port forward to 192.168.20.10 / port 80.
Procedure:
- Enter a name (optional) in the Name text field.
- Enter the protocol to be forwarded, TCP or UDP.
- Select the Interface for the Inbound traffic.
- Enter the Outside IP address in the appropriate text box. For more information, see the 'Port Forwarding Rules' section above.
- Enter the WAN port number. (To configure a range of ports, separate the first port and last port with a dash, e.g. "20-25").
- Enter the LAN IP and the Port where the request will be forwarded.
- From the Segment drop-down menu, select a segment the LAN IP will belong to.
- In the appropriate text field, enter the Inbound Traffic (Remote IP Address/subnet) that will be allowed to be forwarded to an internal server. Leave the Remote IP Address/subnet text field blank to allow "any" traffic.
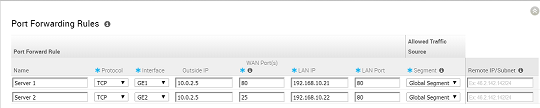
The following figure shows an illustration overview of the port forwarding configuration.

1:1 NAT Settings
These are used to map an Outside IP address supported by the VeloCloud Edge to a server connected to an Edge LAN interface (for example, a web server or a mail server). It can also translate outside IP addresses in different subnets than the WAN interface address if the ISP routes traffic for the subnet towards the VeloCloud Edge. Each mapping is between one IP address outside the firewall for a specific WAN interface and one LAN IP address inside the firewall. Within each mapping, you can specify which ports will be forwarded to the inside IP address. The '+' icon on the right can be used to add additional 1:1 NAT settings.
To configure the mapping:
- Optionally, enter a name for the mapping.
- Enter the Outside IP (LAN) address.
- Select the WAN interface where the Outside IP address will be bound.
- Enter the Inside (LAN) IP address.
- From the Segment drop-down menu, select a segment the LAN IP will belong to.
- Select if Outbound traffic should also be allowed to pass over the firewall connection by checking the Outbound Traffic checkbox.
- Enter the Allowed Traffic Source (Protocol, Ports, Remote IP/Subnet) for the mapping.
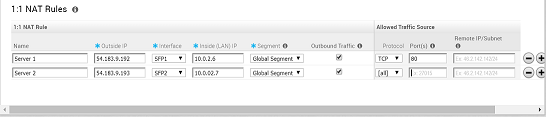
The following figure shows an overview view of the 1:1 NAT configuration.

Configure Edge Access Override
Overrides of Profile settings for Edge Access is an optional step. The override can be specified by selecting the Enable Edge Override option for the Edge Access block. Details about each of these options can be found at Configure Profile Firewall.