This is an optional service that allows you to create VPN tunnel configurations to access one or more Non-VeloCloud Sites. The VeloCloud provides the configuration required to create the tunnel(s) – including creating IKE IPSec configuration and generating a pre-shared key.
Overview
The following figure shows an overview of the VPN tunnels that can be created between the VeloCloud and a Non-VeloCloud Site.
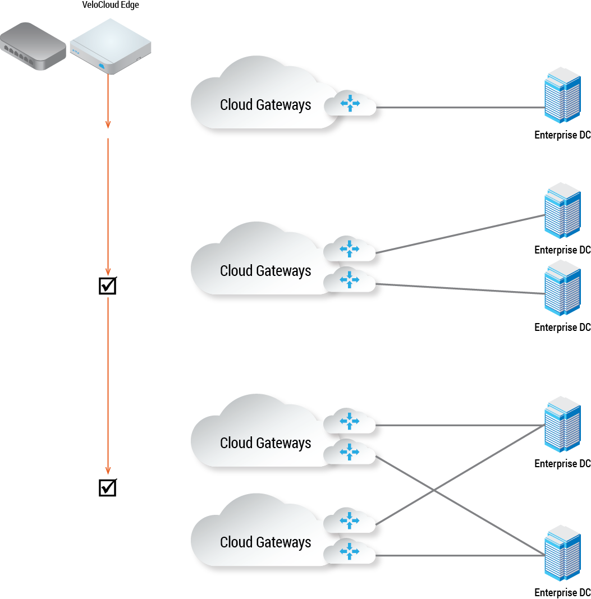
Optionally, an IP address can be specified for a Secondary VPN Gateway to form a Secondary VPN Tunnel between a VeloCloud Gateway and the Secondary VPN Gateway. Using Advanced Settings, Redundant VPN Tunnels can be specified for any VPN tunnels you create.
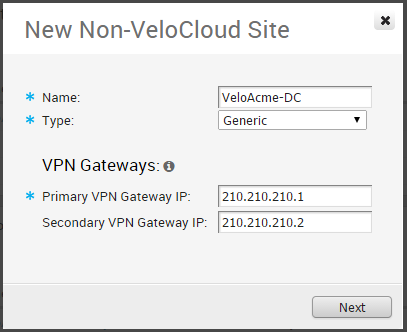
Add Non-VeloCloud Site VPN Gateway
Enter a Name and chose a gateway Type (Cisco ASA, Cisco ISR, Palo Alto, SonicWall, or Generic). Specify the IP address for the Primary VPN Gateway and, optionally, specify an IP address for a Secondary VPN Gateway.
Configure Non-VeloCloud Site Subnets
Once you have created a Non-VeloCloud Site configuration, you can add subnets using the following dialog box.
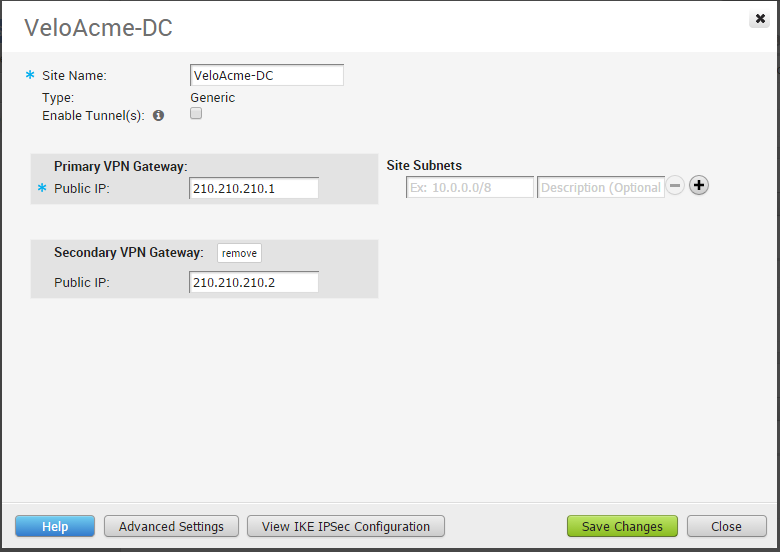
Click the Advanced Settings button to enter additional subnet parameters, VPN Gateway parameters, and to add Redundant VPN tunnel(s).
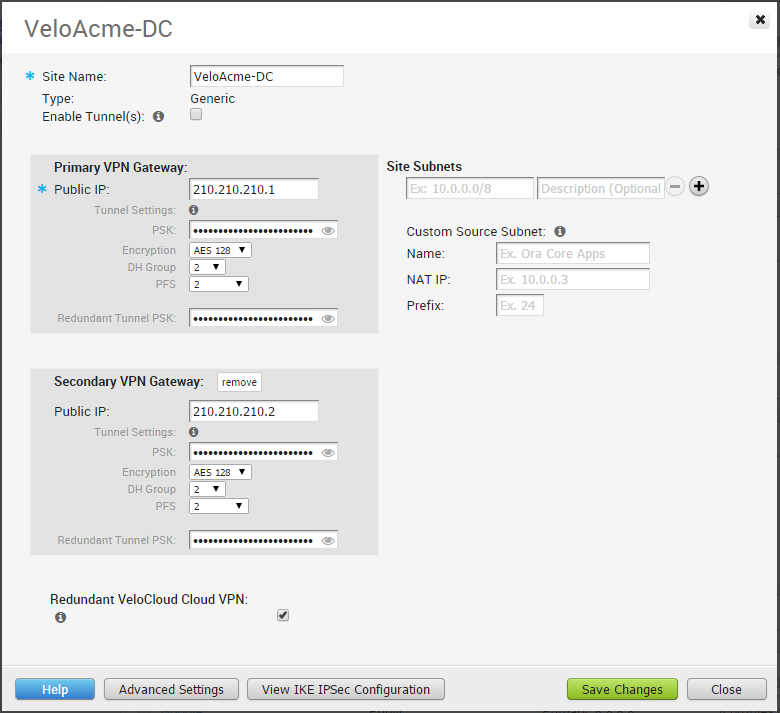
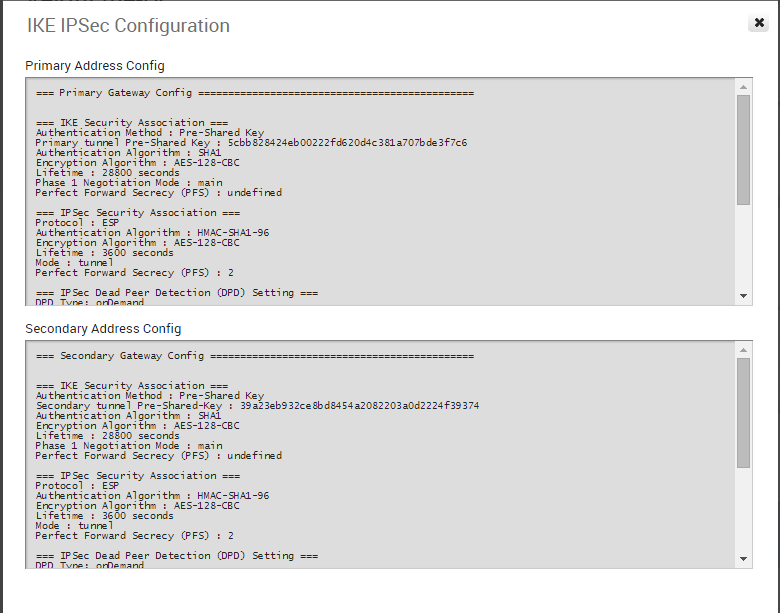
View IKE IPSec Configuration, Configure Non-VeloCloud Site Gateway
If you click the View IKE IPSec Configuration button, the information needed to configure the Non-VeloCloud Site Gateway appears. The Gateway administrator should use this information to configure the Gateway VPN tunnel(s).
Enable IPSec Tunnel
The Non-VeloCloud Site VPN tunnel is initially disabled. You must enable the tunnel(s) after the Non-VeloCloud Site Gateway has been configured and before first use of the Edge-to- Non-VeloCloud Site VPN.
