Describes how to configure a Non SD-WAN Destination of type Generic Firewall (Policy Based VPN) in SD-WAN Orchestrator.
Procedure
- From the navigation panel in the SD-WAN Orchestrator, go to Configure > Network Services.
The Services screen appears.
- In the Non SD-WAN Destinations via Gateway area, click the New button.
The New Non SD-WAN Destinations via Gateway dialog box appears.
- In the Name text box, enter the name for the Non SD-WAN Destination.
- From the Type drop-down menu, select Generic Firewall (Policy Based VPN).
- Enter the IP address for the Primary VPN Gateway, and click Next.
A Non SD-WAN Destination of type Generic Firewall (Policy Based VPN) is created and a dialog box for your Non SD-WAN Destination appears.
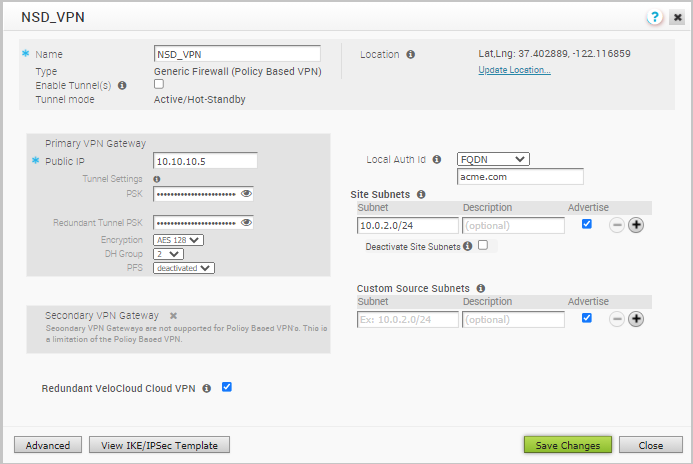
- To configure tunnel settings for the Non SD-WAN Destination’s Primary VPN Gateway, click the Advanced button.
- In the Primary VPN Gateway area, you can configure the following tunnel settings:
Field Description PSK The Pre-Shared Key (PSK), which is the security key for authentication across the tunnel. The Orchestrator generates a PSK by default. If you want to use your own PSK or password then you can enter it in the textbox. Note: Starting from the 4.5 release, the use of the special character "<" in the password is no longer supported. In cases where users have already used "<" in their passwords in previous releases, they must remove it to save any changes on the page.Encryption Select either AES 128 or AES 256 as the AES algorithms key size to encrypt data. The default value is AES 128. DH Group Select the Diffie-Hellman (DH) Group algorithm to be used when exchanging a pre-shared key. The DH Group sets the strength of the algorithm in bits. The supported DH Groups are 2, 5, and 14. It is recommended to use DH Group 14. PFS Select the Perfect Forward Secrecy (PFS) level for additional security. The supported PFS levels are 2 and 5. The default value is deactivated. Note: The Secondary VPN Gateway are not supported for the Generic Firewall (Policy Based VPN) network service type. - Select the Redundant VeloCloud Cloud VPN checkbox to add redundant tunnels for each VPN Gateway.
Any changes made to Encryption, DH Group, or PFS of Primary VPN Gateway will also be applied to the redundant VPN tunnels, if configured. After modifying the tunnel settings of the Primary VPN Gateway, save the changes and then click View IKE/IPSec Template to view the updated tunnel configuration.Note: Currently, the supported IKE version is IKEv1.
- Click the Update location link to set the location for the configured Non SD-WAN Destination. The latitude and longitude details are used to determine the best Edge or Gateway to connect to in the network.
- Local authentication ID defines the format and identification of the local gateway. From the Local Auth Id drop-down menu, choose from the following types and enter a value that you determine:
- FQDN - The Fully Qualified Domain Name or hostname. For example, google.com.
- User FQDN - The User Fully Qualified Domain Name in the form of email address. For example, [email protected].
- IPv4 - The IP address used to communicate with the local gateway.
Note:For Generic Firewall (Policy based VPN), if the user does not specify a value, Default is used as the local authentication ID. The default local authentication ID value will be the SD-WAN Gateway Interface Local IP.
- Under Site Subnets, you can add subnets for the Non SD-WAN Destination by clicking the + button. If you do not need subnets for the site, select the Deactivate Site Subnets checkbox.
- Use Custom Source Subnets to override the source subnets routed to this VPN device. Normally, source subnets are derived from the edge LAN subnets routed to this device.
- Check the Enable Tunnel(s) checkbox once you are ready to initiate the tunnel from the SD-WAN Gateway to the Generic Firewall (Policy Based VPN) VPN gateways.
- Click Save Changes.