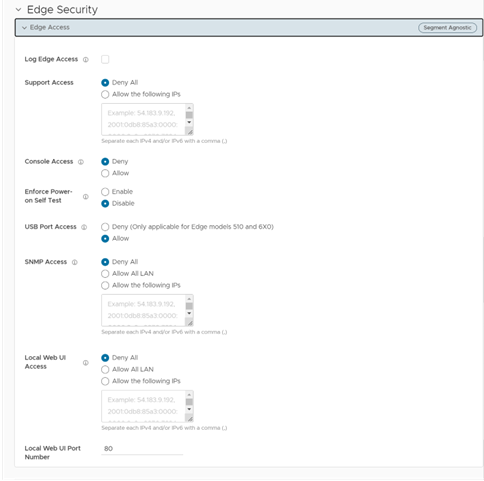
When configuring a profile for Edge access, you must make sure to select the appropriate option for Support access, Console access, USB port access, SNMP access, and Local Web UI access under Firewall settings to make the Edge more secure. This will prevent any malicious user from accessing the Edge.
Power-on Self-Test
In the 5.1.0 release, a power-on self-test is performed after the SD-WAN Orchestrator is powered on or rebooted to verify the software author and to guarantee that critical files and code have not been alerted or corrupted. Use cases for this feature include Common Criteria Requirements and Medium to high-risk deployments (Finance, Government, etc.).
Note: The Power-on Self-test feature is deactivated by default. (A warning message displays on the console, an event is generated, and the Power-on Self-test continues.
The Power on Self-test feature is comprised of the following checks when the SD-WAN Orchestrator is powered-on or rebooted:
- Software Integrity test: Critical system files are identified and signed at build time. The integrity of the signatures is verified. This process uses cryptographic signatures to validate authenticity and integrity.
- Known Answer test of Cryptographic modules: Cryptographic modules, such as Openssl, will run Known answer tests and verify they all pass.
- Test of Entropy source: The Random number generation capability of the entropy source is verified.
Note: The Power-on Self-test will indicate a Pass/Fail result. The system will continue to bring up the remaining applications only if the Power-on Self-test has passed. If the Power-on Self-test fails, error messages will display indicating where the test failed, and the system boot-up sequence will stop.
The following files are signed and verified during the power-on and reboot process:
- Edges (All files under):
- /opt/vc/bin
- /opt/vc/sbin
- /opt/vc/lib
- /bin
- /sbin
- /lib
- /usr/bin
- /usr/sbin
- /usr/lib
- /vmlinuz
- /etc/init.d
- SD-WAN Orchestrator and SD-WAN Gateway
Note: For the following modules, the integrity check runs in ENFORCED mode and will cause a boot FAIL if they cannot be verified.
- SD-WAN Gateway - Package names are stored in: /opt/vc/etc/post/vcg_critical_packages.in
- Gateway Critical Modules
- gatewayd.*:all
- libssl1.0.0:.*:amd64
- libssl1.1:.*:amd64
- openssl:.*:all
- python-openssl:.*:all
- Gateway Critical Modules
- SD-WAN Orchestrator - Package names are stored in /opt/vc/etc/post/vco_critical_packages.in
- SD-WAN Orchestrator Critical Modules:
- libssl1.0.0:.*:amd64
- ibssl1.1:.*:amd64
- openssl:.*:all
- vco-backend:.*:all
- vco-cws-service:.*:all
- vco-dr:.*:all
- vco-new-ui:.*:all
- vco-nginx-apigw:.*:all
- vco-nginx-common:.*:all
- vco-nginx-i18n:.*:all
- vco-nginx-portal:.*:all
- vco-nginx-reporting:.*:all
- vco-nginx-sdwan-api:.*:all
- vco-nginx-upload:.*:all
- vco-node-common:.*:all
- vco-portal:.*:all
- vco-sdwan-api:.*:all
- vco-tools:.*:all
- vco-ui:.*:all
- vco-ztnad-service:.*:all
- nodejs:.*:all
- vc-fips-common:.*:all
- vc-fips-complaint:.*:all
- vc-fips-strict:.*:all
- openssh-client:.*:all
- openssh-server:.*:all
- linux-base:.*:all
- linux-firmware:.*:all
- linux-tools-common:.*:all
- libselinux1:.*:amd64
- linux-base:.*:all
- linux-firmware:.*:all
- linux-libc-dev:.*:amd64
- util-linux:.*:amd64
- linux-tools-common:.*:all
- linux-(aws|azure|generic)-headers-.*:.*:all
- linux-(aws|azure|generic)-tools-.*:.*:amd64
- linux-headers-.*-(aws|azure|generic):.*:amd64
- linux-headers-(aws|azure|generic)-lts-.*:.*:amd64
- linux-image-unsigned-.*-(aws|azure|generic):.*:amd64
- linux-image-unsigned-(aws|azure|generic)-lts-.*:.*:amd64
- linux-modules-.*-(aws|azure|generic):.*:amd64
- linux-tools-.*-(aws|azure|generic):.*:amd64
- linux-tools-(aws|azure|generic)-lts-.*:amd64
- SD-WAN Orchestrator Critical Modules:
- SD-WAN Gateway - Package names are stored in: /opt/vc/etc/post/vcg_critical_packages.in
Procedure
To configure Edge access for profiles, perform the following steps: