By default, all the Edges inherit the Firewall rules, Enhanced Firewall Services (EFS) settings, Stateful Firewall settings, Network and Flood Protection settings, Firewall Logging, Syslog Forwarding, and Edge access configurations from the associated Profile.
- In the SD-WAN service of the Enterprise portal, go to .
- Select an Edge for which you want to override the inherited Firewall settings and click on the Firewall tab.
- Select the Override checkbox against the various Firewall settings if you want to modify the inherited Firewall rules and settings for the selected Edge.
Note: The Edge override rules will take priority over the inherited Profile rules for the Edge. Any Firewall override match value that is the same as any Profile Firewall rule will override that Profile rule.

- At the Edge level, you can configure Port Forwarding and 1:1 NAT IPv4 or IPv6 rules individually by navigating to Additional Settings > Inbound ACLs. For detailed information, see Port Forwarding Rules and 1:1 NAT Settings.
Note: By default, all inbound traffic will be blocked unless the Port Forwarding and 1:1 NAT Firewall Rules are configured. The outside IP will always be that of WAN IP or IP address from WAN IP subnet.Note: When configuring IPv6 Port Forwarding and 1:1 NAT rules, you can enter only Global or Unicast IP address and cannot enter Link Local Address.
Port Forwarding and 1:1 NAT Firewall Rules
Port Forwarding and 1:1 NAT firewall rules gives Internet clients access to servers connected to an Edge LAN interface. Access can be made available through either Port Forwarding Rules or 1:1 NAT (Network Address Translation) rules.
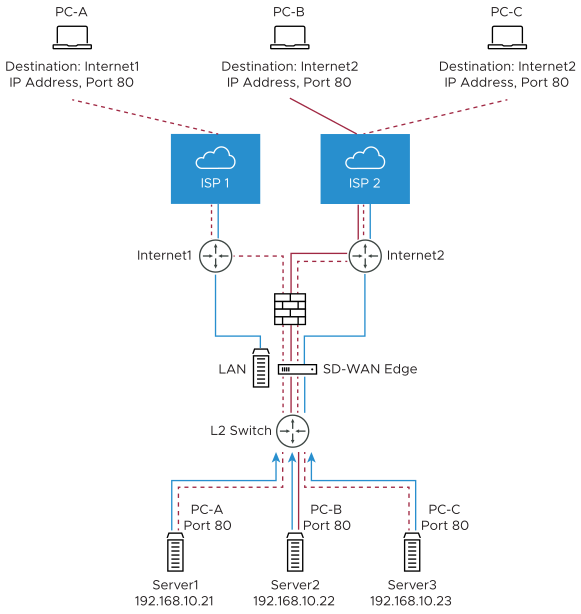
Port Forwarding Rules
Port forwarding rules allows you to configure rules to redirect traffic from a specific WAN port to a device (LAN IP/ LAN Port) within the local subnet. Optionally, you can also restrict the inbound traffic by an IP or a subnet. Port forwarding rules can be configured with the Outside IP which is on the same subnet of the WAN IP. It can also translate outside IP addresses in different subnets than the WAN interface address if the ISP routes traffic for the subnet towards the SD-WAN Edge.
The following figure illustrates the port forwarding configuration.
In the Port Forwarding Rules section, you can configure port forwarding rules with IPv4 or IPv6 address by clicking the +Add button and then entering the following details.
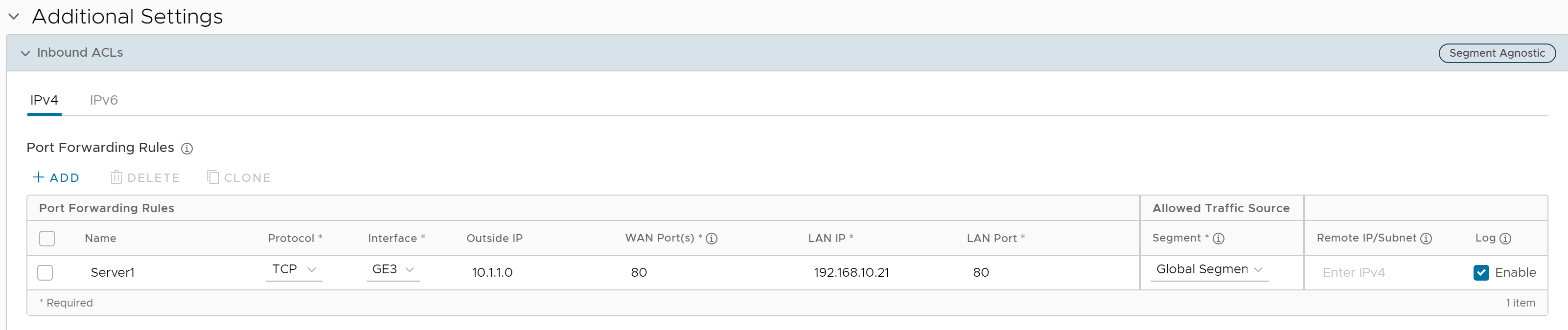
- In the Name text box, enter a name (optional) for the rule.
- From the Protocol drop-down menu, select either TCP or UDP as the protocol for port forwarding.
- From the Interface drop-down menu, select the interface for the inbound traffic.
- In the Outside IP text box, enter the IPv4 or IPv6 address using which the host (application) can be accessed from the outside network.
- In the WAN Ports text box, enter a WAN port or a range of ports separated with a dash (-), for example 20-25.
- In the LAN IP and LAN Port text boxes, enter the IPv4 or IPv6 address and port number of the LAN, where the request will be forwarded.
- From the Segment drop-down menu, select a segment the LAN IP will belong to.
- In the Remote IP/subnet text box, specify an IP address of an inbound traffic that you want to be forwarded to an internal server. If you do not specify any IP address, then it will allow any traffic.
- Select the Log check box to activate logging for this rule.
- Click Save Changes.
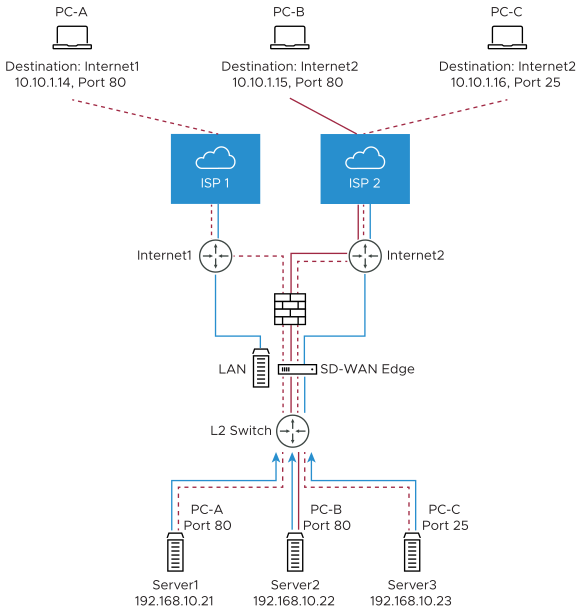
1:1 NAT Settings
These are used to map an Outside IP address supported by the SD-WAN Edge to a server connected to an Edge LAN interface (for example, a web server or a mail server). It can also translate outside IP addresses in different subnets than the WAN interface address if the ISP routes traffic for the subnet towards the SD-WAN Edge. Each mapping is between one IP address outside the firewall for a specific WAN interface and one LAN IP address inside the firewall. Within each mapping, you can specify which ports will be forwarded to the inside IP address. The '+' icon on the right can be used to add additional 1:1 NAT settings.
The following figure illustrates the 1:1 NAT configuration.
In the 1:1 NAT Rules section, you can configure 1:1 NAT rules with IPv4 address or IPv6 address by clicking the +Add button and then entering the following details.
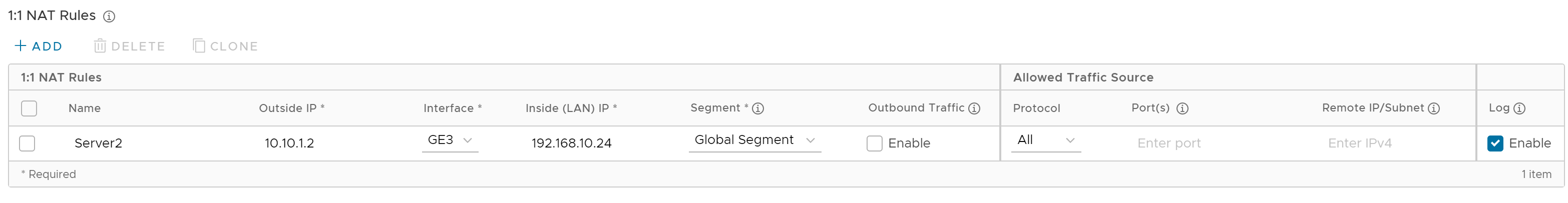
- In the Name text box, enter a name for the rule.
- In the Outside IP text box, enter the IPv4 or IPv6 address with which the host can be accessed from an outside network.
- From the Interface drop-down menu, select the WAN interface where the Outside IP address will be bound.
- In the Inside (LAN) IP text box, enter the actual IPv4 or IPv6 (LAN) address of the host.
- From the Segment drop-down menu, select a segment the LAN IP will belong to.
- Select the Outbound Traffic check box, if you want to allow traffic from LAN Client to Internet being NATed to Outside IP address.
- Enter the Allowed Traffic Source (Protocol, Ports, Remote IP/Subnet) details for mapping in the respective fields.
- Select the Log check box to activate logging for this rule.
- Click Save Changes.