You can configure Firewall rules at the Profile and Edge levels to allow, drop, reject, or skip inbound and outbound traffic. If stateful firewall feature is activated, the firewall rule will be validated to filter both inbound and outbound traffic. With stateless firewall, you can control to filter only outbound traffic. The firewall rule matches parameters such as IP addresses, ports, VLAN IDs, Interfaces, MAC addresses, domain names, protocols, object groups, applications, and DSCP tags. When a data packet matches the match conditions, the associated action or actions are taken. If a packet matches no parameters, then a default action is taken on the packet.
To configure a firewall rule at the Profile level, perform the following steps.
Procedure
- In the SD-WAN service of the Enterprise portal, go to Configure > Profiles. The Profiles page displays the existing Profiles.
- Select a Profile to configure a firewall rule, and click the Firewall tab.
From the Profiles page, you can navigate to the Firewall page directly by clicking the View link in the Firewall column of the Profile.
- Go to the Configure Firewall section and under Firewall Rules area, click + NEW RULE. The Configure Rule dialog box appears.
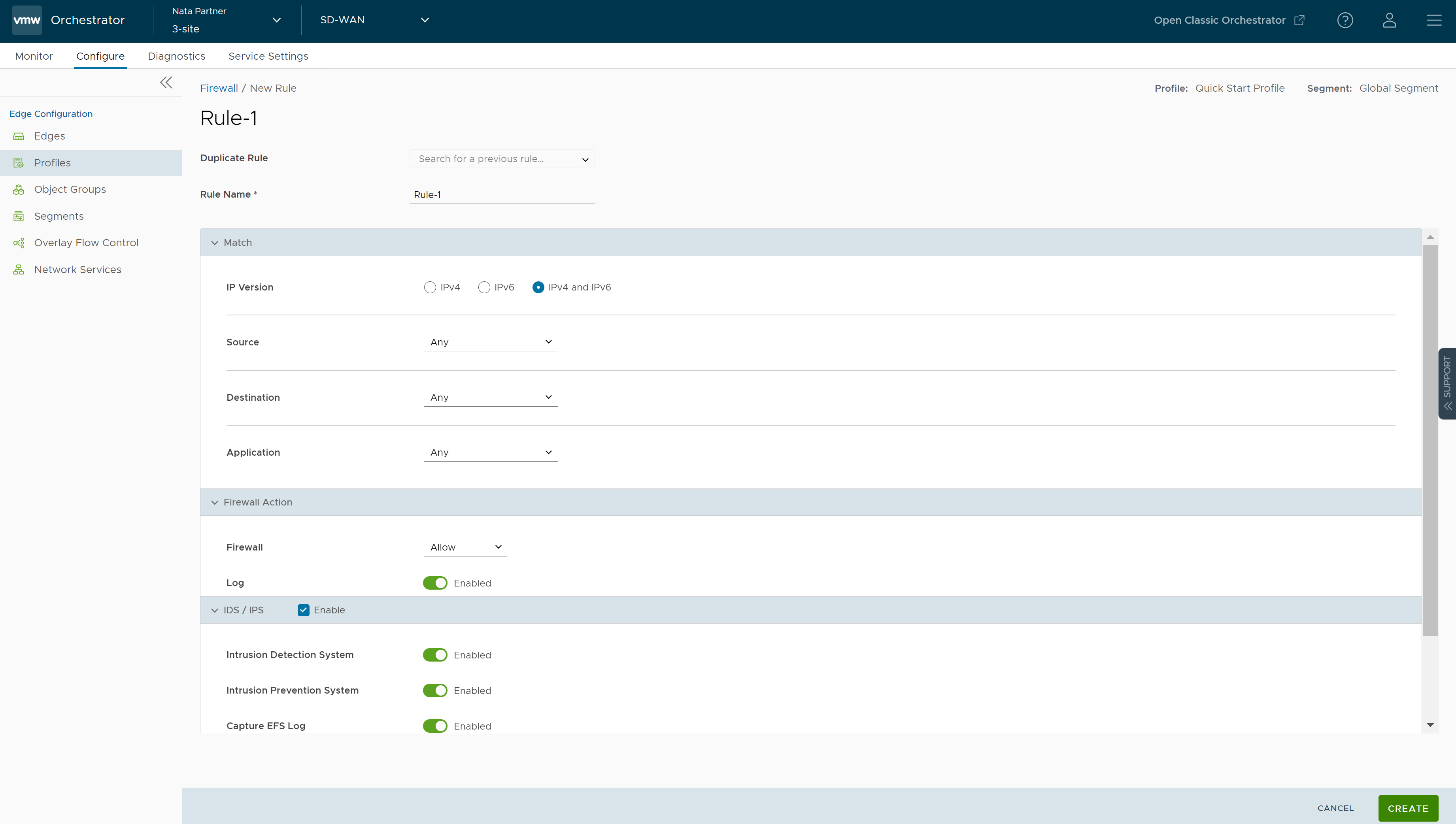
- In the Rule Name text box, enter a unique name for the Rule. To create a firewall rule from an existing rule, select the rule to be duplicated from the Duplicate Rule drop-down menu.
- In the Match section, configure the match conditions for the rule:
Field Description IP Version By default, IPv4 and IPv6 address type is selected. You can configure the Source and Destination IP addresses according to the selected Address Type, as follows: - IPv4 – Allows to configure only IPv4 addresses as Source and Destination.
- IPv6 – Allows to configure only IPv6 addresses as Source and Destination.
- IPv4 and IPv6 – Allows to configure both IPv4 and IPv6 addresses in the matching criteria. If you choose this mode, you cannot configure Source or Destination IP address.
Note: When you upgrade, the firewall rules from previous versions are moved to IPv4 mode.Source Allows to specify the source for packets. Select any of the following options:- Any - Allows all source addresses by default.
- Object Group - Allows you to select a combination of address group and service group. For more information, see Object Groups and Configure Firewall Rule with Object Group.
Note: If the selected address group contains any domain names, then they would be ignored when matching for the source.
- Define - Allows you to define the source traffic to a specific VLAN, Interface, IPv4 or IPv6 Address, MAC Address, or Transport Port. Select one of the following options:
- VLAN - Matches traffic from the specified VLAN, selected from the drop-down menu.
Note: When using a VLAN to match source or destination traffic in a firewall policy, it takes into account both local and remote VLANs.
- Interface and IP Address - Matches traffic from the specified interface and IPv4 or IPv6 address, selected from the drop-down menu.
Note: If an interface cannot be selected, then the interface is either not activated or not assigned to this segment.Note: If you select IPv4 and IPv6 (Mixed mode) as the Address Type, then the traffic is matched based on only the specified interface.Along with the IP address, you can specify one of the following address types to match the source traffic:
- CIDR prefix - Choose this option if you want the network defined as a CIDR value (for example:
172.10.0.0 /16). - Subnet mask - Choose this option if you want the network defined based on a Subnet mask (for example,
172.10.0.0 255.255.0.0). - Wildcard mask - Choose this option if you want the ability to narrow the enforcement of a policy to a set of devices across different IP subnets that share a matching host IP address value. The Wildcard mask matches an IP, or a set of IP addresses based on the inverted Subnet mask. A '0' within the binary value of the mask means the value is fixed and a '1' within the binary value of the mask means the value is wild (can be 1 or 0). For example, a Wildcard mask of 0.0.0.255 (binary equivalent = 00000000.00000000.00000000.11111111) with an IP Address of 172.0.0, the first three octets are fixed values, and the last octet is a variable value. This option is available only for IPv4 address.
- CIDR prefix - Choose this option if you want the network defined as a CIDR value (for example:
- Mac Address - Matches traffic based on the specified MAC address.
- Transport Port - Matches traffic from the specified source port or port range.
- VLAN - Matches traffic from the specified VLAN, selected from the drop-down menu.
Destination Allows to specify the destination for packets. Select any of the following options: - Any - Allows all destination addresses by default.
- Object Group - Allows you to select a combination of address group and service group. For more information, see Object Groups and Configure Firewall Rule with Object Group.
- Define - Allows you to define the destination traffic to a specific VLAN, Interface, IPv4 or IPv6 Address, Domain Name, Protocol, or Port. Select one of the following options:
- VLAN - Matches traffic from the specified VLAN, selected from the drop-down menu.
Note: When using a VLAN to match source or destination traffic in a firewall policy, it takes into account both local and remote VLANs.
- Interface - Matches traffic from the specified interface, selected from the drop-down menu.
Note: If an interface cannot be selected, then the interface is either not activated or not assigned to this segment.
- IP Address - Matches traffic for the specified IPv4 or IPv6 address and Domain name.
Note: If you select IPv4 and IPv6 (Mixed mode) as the Address Type, then you cannot specify IP address as the destination.
Along with the IP address, you can specify one of the following address types to match the source traffic: CIDR prefix, Subnet mask, or Wildcard mask.
Use the Domain Name field to match the entire domain name or a portion of the domain name. For example, \"salesforce\" will match traffic to \"mixe\".
- Transport - Matches traffic from the specified source port or port range.
Protocol - Matches traffic for the specified protocol, selected from the drop-down menu. The supported protocols are GRE, ICMP, TCP, and UDP.Note: ICMP is not supported in Mixed mode (IPv4 and IPv6).
- VLAN - Matches traffic from the specified VLAN, selected from the drop-down menu.
Application Select any of the following options: - Any - Applies the firewall rule to any application by default.
- Define - Allows to select an application and Differentiated Services Code Point (DSCP) flag to apply a specific firewall rule.
Note: When creating firewall rules matching an application, the firewall depends on the DPI (Deep Packet Inspection) Engine to identify the application to which a particular flow belongs. Generally, the DPI will not be able to determine the application based on the first packet. The DPI Engine usually needs the first 5-10 packets in the flow to identify the application, but the firewall needs to classify and forward the flow from the very first packet. This may cause the first flow to match a more generalized rule in the firewall list. Once the application has been correctly identified, any future flows matching the same tuples will be reclassified automatically and hit the correct rule.For more information on specific usecase matching FTPv6 Firewall/Business policy rule, see Edge Firewall Support for FTPv6.
- In the Action section, configure the actions to be performed when the traffic matches the defined criteria.
Field Description Firewall Select any of the following action the firewall should perform on packets, when the conditions of the rule are met: - Allow - Allows the data packets by default.
- Drop - Drops the data packets silently without sending any notification to the source.
Log Select this checkbox if you want a log entry to be created when this rule is triggered. - Select the IDS/IPS checkbox and activate either IDS or IPS toggle to create the Firewall. When user activates only IPS, IDS will be automatically activated. EFS engine inspects traffic sent/received through the Edges and matches content against signatures configured in the EFS engine. IDS/IPS Signatures are updated on a continuous basis with a valid EFS license. For more information about EFS, see Enhanced Firewall Services Overview.
Note: EFS can be activated in the rule only if the Firewall action is Allow. If the Firewall action is anything other than Allow, EFS will be deactivated.
- Intrusion Detection System - When IDS is activated on Edges, the Edges detect if the traffic flow is malicious or not based on certain signatures configured in the engine. If attack is detected, the EFS engine generates an alert and sends the alert message to SASE Orchestrator/Syslog Server if Firewall logging is activated in Orchestrator, and will not drop any packets.
- Intrusion Prevention System - When IPS is activated on Edges, the Edges detect if the traffic flow is malicious or not based on certain signatures configured in the engine. If attack is detected, the EFS engine generates an alert and blocks the traffic flow to the client only if the signature rule has action as "Reject", matched by the malicious traffic. If the action in the signature rule is "Alert", the traffic will be allowed without dropping any packets even if you configure IPS.
Note: VMware recommends customer to not activate VNF when IDS/IPS is activated on Edges. - To send the EFS logs to Orchestrator, turn on the Capture EFS Log toggle button.
Note: For an Edge to send the Firewall logs to Orchestrator, ensure that the “Enable Firewall Logging to Orchestrator” customer capability is activated at the Customer level under “Global Settings” UI page. Customers must contact your Operator if you would want the Firewall Logging feature to be activated.
- While creating or updating a Firewall rule, you can add comments about the rule in the New Comment field in the Comment History tab. A maximum of 50 characters is allowed and you can add any number of comments for the same rule.
- After configuring all the required settings, click Create.
A firewall rule is created for the selected Profile, and it appears under the Firewall Rules area of the Profile Firewall page.Note: The rules created at the Profile level cannot be updated at the Edge level. To override the rule, user needs to create the same rule at the Edge level with new parameters to override the Profile level rule.In the Firewall Rules area of the Profile Firewall page, you can perform the following actions:
- DELETE - To delete existing Firewall rules, select the checkboxes prior to the rules and click DELETE.
- CLONE - To duplicate a Firewall rule, select the rule and click CLONE.
- COMMENT HISTORY - To view all comments added while creating or updating a rule, select the rule and click COMMENT HISTORY.
- Search for Rule - Allows to search the rule by Rule name, IP address, Port/Port range, and Address group and Service group names.