Follow the below steps to configure a Non SD-WAN Destination of type Generic IKEv2 Router (Route Based VPN) in the SASE Orchestrator.
Procedure
- Once you have created a Non SD-WAN Destination configuration of the type Generic IKEv2 Router (Route Based VPN), you are redirected to an additional configuration options page:
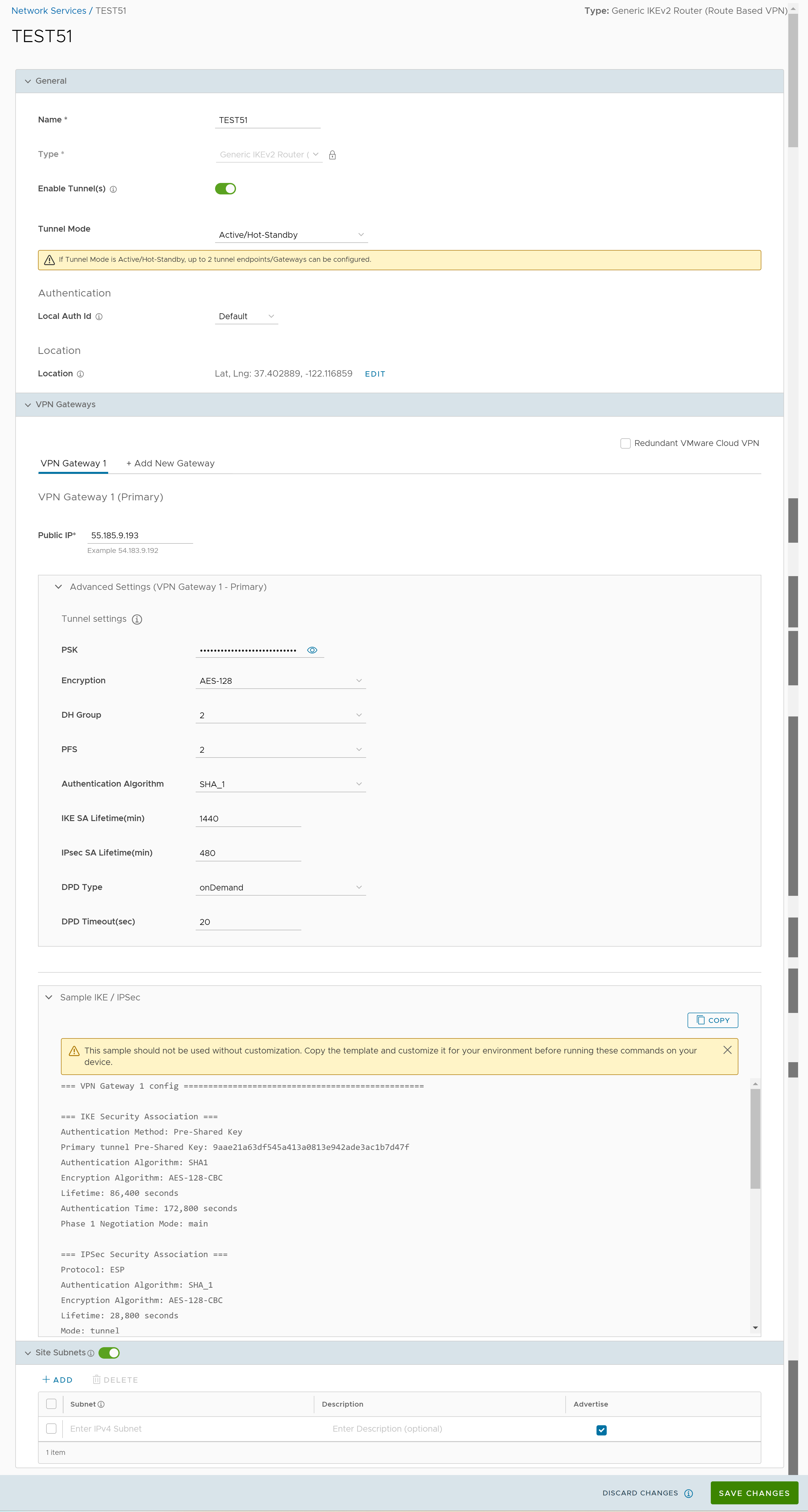
- You can configure the following tunnel settings:
Option Description General Name You can edit the previously entered name for the Non SD-WAN Destination. Type Displays the type as Generic IKEv2 Router (Route Based VPN). You cannot edit this option. Enable Tunnel(s) Click the toggle button to initiate the tunnel(s) from the SD-WAN Gateway to the Generic IKEv2 Router VPN Gateway. Tunnel Mode Active/ Hot-Standby mode supports to set up a maximum of 2 tunnel endpoints or Gateways. Active/Activemode supports to set up a maximum of 4 tunnel endpoints or Gateways. All Active tunnels can send and receive traffic through ECMP. ECMP Load Sharing Method Flow Load Based (Default) Flow load based algorithm maps the new flow to the path with least number of flows mapped among the available paths to the destination. Hash Load Based algorithm takes input parameters from 5-tuple (SrcIP, DestIP, SrcPort, DestPort, Protocol). These inputs can be any or all or any subset of this tuple based on user configuration. Flow is mapped to the path based on hash value with selected inputs. VPN Gateway 1 Enter a valid IP address. VPN Gateway 2 Enter a valid IP address. This field is optional. VPN Gateway 3 Enter a valid IP address. This field is optional. VPN Gateway 4 Enter a valid IP address. This field is optional. Public IP Displays the IP address of the Primary VPN Gateway. PSK The Pre-Shared Key (PSK) is the security key for authentication across the tunnel. The SASE Orchestrator generates a PSK by default. If you want to use your own PSK or password, enter it in the text box. Encryption Select either AES-128 or AES-256 as the AES algorithm key size to encrypt data. The default value is AES-128. DH Group Select the Diffie-Hellman (DH) Group algorithm from the drop-down menu. This is used for generating keying material. The DH Group sets the strength of the algorithm in bits. The supported DH Groups are 2, 5, and 14. The default value is 2. PFS Select the Perfect Forward Secrecy (PFS) level for additional security. The supported PFS levels are deactivated, 2, and 5. The default value is 2. Authentication Algorithm Select the authentication algorithm for the VPN header. Select one of the supported Secure Hash Algorithm (SHA) functions from the drop-down menu:
- SHA1
- SHA256
- SHA384
- SHA512
The default value is SHA 1.
IKE SA Lifetime(min) Time when Internet Key Exchange (IKE) rekeying is initiated for SD-WAN Edges. The minimum IKE lifetime is 10 minutes and maximum is 1440 minutes. The default value is 1440 minutes. IPsec SA Lifetime(min) Time when Internet Security Protocol (IPsec) rekeying is initiated for Edges. The minimum IPsec lifetime is 3 minutes and maximum is 480 minutes. The default value is 480 minutes. DPD Type The Dead Peer Detection (DPD) method is used to detect if the Internet Key Exchange (IKE) peer is alive or dead. If the peer is detected as dead, the device deletes the IPsec and IKE Security Association. Select either Periodic or onDemand from the drop-down menu. The default value is onDemand. DPD Timeout(sec) Enter the DPD timeout value. The DPD timeout value will be added to the internal DPD timer, as described below. Wait for a response from the DPD message before considering the peer to be dead (Dead Peer Detection). Prior to the 5.1.0 release, the default value is 20 seconds. For the 5.1.0 release and later, see the list below for the default value.- Library Name: Quicksec
- Probe Interval: Exponential (0.5 sec, 1 sec, 2 sec, 4 sec, 8 sec, 16 sec)
- Default Minimum DPD Interval: 47.5sec (Quicksec waits for 16 seconds after the last retry. Therefore, 0.5+1+2+4+8+16+16 = 47.5).
- Default Minimum DPD interval + DPD Timeout(sec): 67.5 sec
Note: Prior to the 5.1.0 release, you can deactivate DPD by configuring the DPD timeout timer to 0 seconds. However, for the 5.1.0 release and later, you cannot deactivate DPD by configuring the DPD timeout timer to 0 seconds. The DPD timeout value in seconds will get added onto the default minimum value of 47.5 seconds).Redundant VMware Cloud VPN Select the check box to add redundant tunnels for each VPN Gateway. Changes made to Encryption, DH Group, or PFS of Primary VPN Gateway also apply to the redundant VPN tunnels, if configured. Secondary VPN Gateway Click the Add button, and then enter the IP address of the Secondary VPN Gateway. Click Save Changes. The Secondary VPN Gateway is immediately created for this site and provisions a VMware VPN tunnel to this Gateway.
Local Auth Id Local authentication ID defines the format and identification of the local gateway. From the drop-down menu, choose from the following types and enter a value: - FQDN - The Fully Qualified Domain Name or hostname. For example: vmware.com
- User FQDN - The User Fully Qualified Domain Name in the form of email address. For example: [email protected]
- IPv4 - The IP address used to communicate with the local gateway.
- IPv6 - The IP address used to communicate with the local gateway.
Note:- If you do not specify a value, Default is used as the local authentication ID.
- The default local authentication ID value is the SD-WAN Gateway Interface Public IP.
Sample IKE / IPsec Click to view the information needed to configure the Non SD-WAN Destination Gateway. The Gateway administrator should use this information to configure the Gateway VPN tunnel(s). Location Click Edit to set the location for the configured Non SD-WAN Destination. The latitude and longitude details are used to determine the best Edge or Gateway to connect to in the network. Site Subnets Use the toggle button to activate or deactivate the Site Subnets. Click Add to add subnets for the Non SD-WAN Destination. If you do not need subnets for the site, select the subnet and click Delete. Note:- To support the datacenter type of Non SD-WAN Destination, besides the IPsec connection, you must configure Non SD-WAN Destination local subnets into the VMware system.
- If there are no site subnets configured, deactivate Site Subnets to activate the tunnel.
Note: When AWS initiates the rekey tunnel with a VMware SD-WAN Gateway (in Non SD-WAN Destinations), a failure can occur and the tunnel may not be established, which can cause traffic interruption. In this case, adhere to the following:- IPsec SA Lifetime(min) timer configurations for the SD-WAN Gateway must be less than 60 minutes (recommended value = 50 minutes), to match the AWS default IPsec configuration.
- DH Group and PFS values must be matched.
- Click Save Changes.