This topic describes how to configure a Non SD-WAN Destination of type Microsoft Azure Virtual Hub via Edge in SASE Orchestrator.
To configure a Non SD-WAN Destination of type Microsoft Azure Virtual Hub via Edge in SASE Orchestrator:
Prerequisites
- Ensure you have configured a Cloud subscription. For steps, see Configure API Credentials.
- Ensure you have created Virtual WAN and Hubs in Azure. For steps, see Configure Azure Virtual WAN for Branch-to-Azure VPN Connectivity.
Procedure
- In the SD-WAN service of the Enterprise portal, go to Configure > Network Services, and then under Non SD-WAN Destinations, expand Non SD-WAN Destinations via Edge.
- In the Non SD-WAN Destinations via Edge area, click the New button.
The New Non SD-WAN Destinations via Edge dialog box appears.
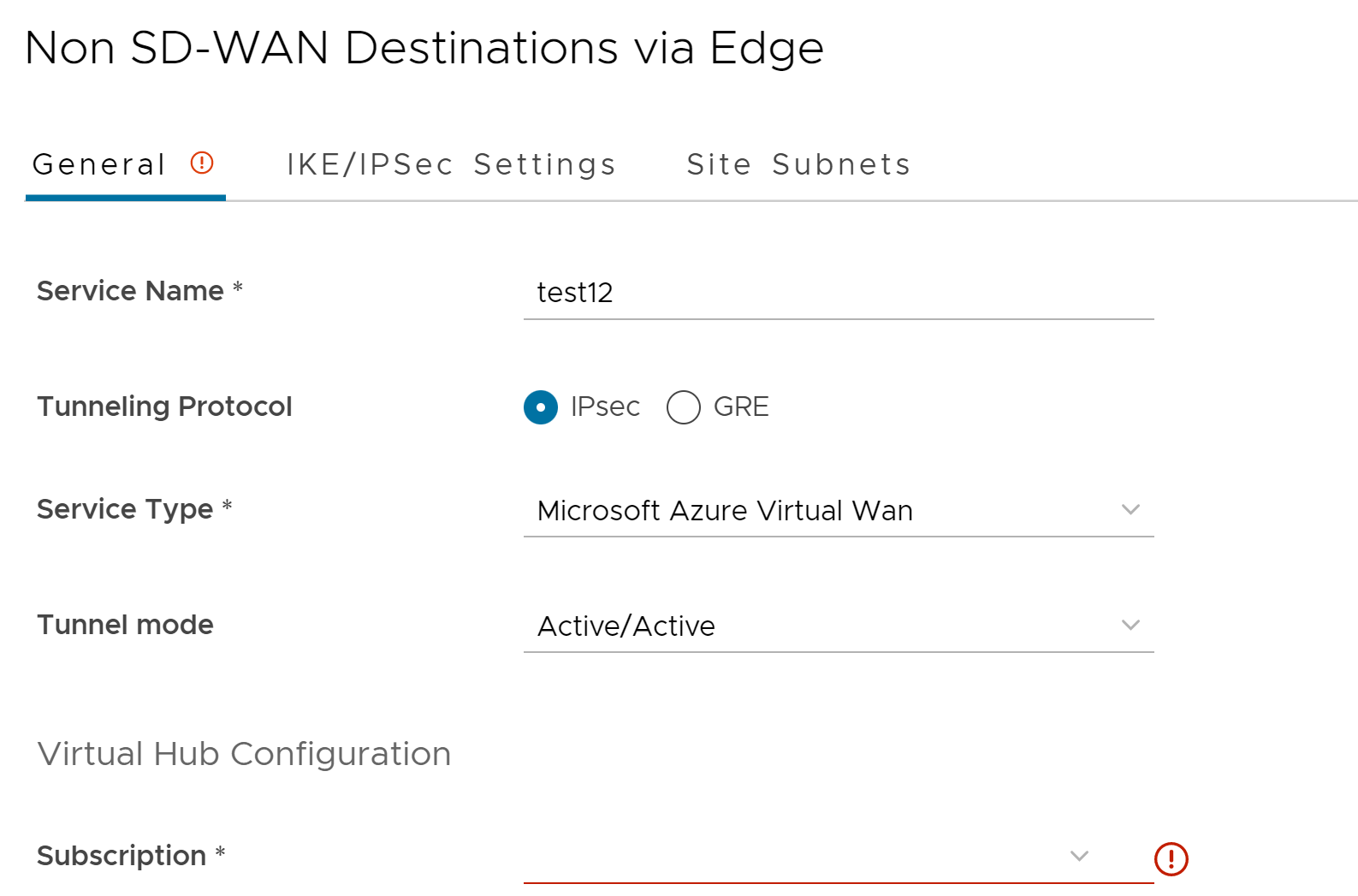
- Enter the Service Name and Service Type of the Non SD-WAN Destination. Once you enter the Service Type as Microsoft Azure Virtual Hub, Virtual Hub Configuration section is displayed.
- From the Subscription drop-down menu, select a cloud subscription. The application fetches all the available Virtual WANs dynamically from Azure.
- From the Virtual WAN drop-down menu, select a virtual WAN. The application auto-populates the resource group to which the virtual WAN is associated.
- From the Virtual Hub drop-down menu, select a Virtual Hub. The application auto-populates the Azure region corresponding to the Hub
- Click the IKE/IPSec Settings tab and configure the following parameters:
Option Description IP Version Select an IP version (IPv4 or IPv6) of the current Non SD-WAN Destination from the drop-down menu. Primary VPN Gateway Public IP Enter a valid IPv4 or IPv6 address. This field is mandatory. View advanced settings for IKE Proposal: Expand this option to view the following fields. Encryption Select the AES algorithm key size from the drop-down list, to encrypt data. The available options are AES 128, AES 256, AES 128 GCM, AES 256 GCM, and Auto. The default value is AES 128. DH Group Select the Diffie-Hellman (DH) Group algorithm from the drop-down list. This is used for generating keying material. The DH Group sets the strength of the algorithm in bits. The supported DH Groups are 2, 5, 14, 15, 16, 19, 20, and 21. The default value is 14. Hash Select one of the following supported Secure Hash Algorithm (SHA) functions from the drop-down list: - SHA 1
- SHA 256
- SHA 384
Note: This value is not available for the Microsoft Azure Virtual Wan Service Type.
- SHA 512
Note: This value is not available for the Microsoft Azure Virtual Wan Service Type.
- Auto
The default value is SHA 256.
IKE SA Lifetime(min) Enter the time when Internet Key Exchange (IKE) rekeying is initiated for Edges. The minimum IKE lifetime is 10 minutes and maximum is 1440 minutes. The default value is 1440 minutes. Note: Rekeying must be initiated before 75-80 % of lifetime expires.DPD Timeout(sec) Enter the DPD timeout value. The DPD timeout value will be added to the internal DPD timer, as described below. Wait for a response from the DPD message before considering the peer to be dead (Dead Peer Detection). Prior to the 5.1.0 release, the default value is 20 seconds. For the 5.1.0 release and later, see the list below for the default value.- Library Name: Quicksec
- Probe Interval: Exponential (0.5 sec, 1 sec, 2 sec, 4 sec, 8 sec, 16 sec)
- Default Minimum DPD Interval: 47.5sec (Quicksec waits for 16 seconds after the last retry. Therefore, 0.5+1+2+4+8+16+16 = 47.5).
- Default Minimum DPD interval + DPD Timeout(sec): 67.5 sec
Note: For the 5.1.0 release and later, you cannot deactivate DPD by configuring the DPD timeout timer to 0 seconds. The DPD timeout value in seconds gets added into the default minimum value of 47.5 seconds.View advanced settings for IPsec Proposal: Expand this option to view the following fields. Encryption Select the AES algorithm key size from the drop-down list, to encrypt data. The available options are None, AES 128, and AES 256. The default value is AES 128. PFS Select the Perfect Forward Secrecy (PFS) level for additional security. The supported PFS levels are 2, 5, 14, 15, 16, 19, 20, and 21. The default value is 14. Hash Select one of the following supported Secure Hash Algorithm (SHA) functions from the drop-down list: - SHA 1
- SHA 256
- SHA 384
Note: This value is not available for the Microsoft Azure Virtual Wan Service Type.
- SHA 512
Note: This value is not available for the Microsoft Azure Virtual Wan Service Type.
The default value is SHA 256.
IPsec SA Lifetime(min) Enter the time when Internet Security Protocol (IPsec) rekeying is initiated for Edges. The minimum IPsec lifetime is 3 minutes and maximum is 480 minutes. The default value is 480 minutes. Note: Rekeying must be initiated before 75-80 % of lifetime expires.Secondary VPN Gateway Add - Click this option to add a secondary VPN Gateway. Following fields are displayed. Public IP Enter a valid IPv4 or IPv6 address. Remove Deletes the Secondary VPN Gateway. Keep Tunnel Active Select this check box to keep the Secondary VPN tunnel active for this site. Tunnel settings are the same as Primary VPN Gateway Select this check box if you want to apply the same advanced settings for Primary and Secondary Gateways. You can choose to enter the settings for the Secondary VPN Gateway manually. Note:Non SD-WAN Destination via Edge of type Microsoft Azure Virtual WAN automation supports only IKEv2 protocol with Azure Default IPsec policies (except GCM mode), when SD-WAN Edge act as an Initiator and Azure act as a Responder during an IPsec tunnel setup.
- The Secondary VPN Gateway is created immediately for this site and provisions a VMware VPN tunnel to this Gateway.
- Click the Site Subnets tab and configure the following:
Option Description Add Click this option to add a subnet and a description for the Non SD-WAN Destination. Delete Click this option to delete the selected Subnet. Note: To support the datacenter type of Non SD-WAN Destination, besides the IPSec connection, you must configure Non SD-WAN Destination local subnets into the VMware system. - Click Save .
The Microsoft Azure Non SD-WAN Destination is created and a dialog box for your Non SD-WAN Destination appears.
What to do next
- Configure Cloud VPN for Profiles
- Associate the Microsoft Azure Non SD-WAN Destination to an Edge and configure tunnels to establish a tunnel between a branch and Azure Virtual Hub. For more information, see Associate a Microsoft Azure Non SD-WAN Destination to an SD-WAN Edge and Add Tunnels.
For information about Azure Virtual WAN Edge Automation, see Configure SASE Orchestrator for Azure Virtual WAN IPsec Automation from SD-WAN Edge.