This section describes about monitoring and inspecting network traffic patterns to detect threats and troubleshoot performance issues.
The Branch Attack Surface
An adversary has numerous ways to gain initial access to an Enterprise's network. Some of those ways include the following:
- Internet of Things (IoT) - These devices have become ubiquitous as there seems to be a race to turn everything “smart.” Everything wants access to the network, such as sensors, printers, security cameras, door locks, and so on. Unfortunately, security is usually an afterthought when creating these devices.
- Employees - Employees are prime targets for adversaries to leverage for initial access. Disgruntled employees can sell access to your network, and inattentive employees can be susceptible to phishing campaigns.
- Physical Security - Physical security vulnerabilities could provide opportunities for malicious actors to gain access to machines or open ports. This could allow them to steal data, launch attacks, or disrupt operations. It is important to implement strong physical security measures to protect against these risks.
- Network Devices - Network devices that are not patched offer adversaries the means to spread through the network. This is because unpatched devices may contain vulnerabilities that can be exploited by attackers. Once an attacker has gained access to an unpatched device, they can then use it to move laterally through the network and gain access to other devices. This can lead to a data breach, financial loss, or even physical damage. Therefore, it is important to keep all network devices up to date with the latest security patches.
Protecting internal traffic is as important as securing the network perimeter. Adversaries have multiple methods of bypassing a robust security stack that protects the boundary between the internal network and the outside world. Without a layered defense, a threat actor essentially has free rein over the internal network. A solid understanding of network segmentation will make it easier to create firewall policies that add the appropriate level of security without compromising performance.
Private Access
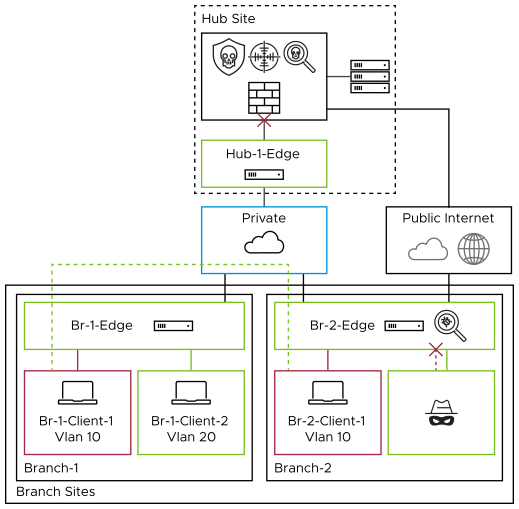
- Doctors' office downloading MRI images from Imaging Center
- IoT device communications
- Application traffic
Lateral Movement - Once an attacker gains access to a machine on an internal network, they will typically need to find a way to move laterally through the network in order to find sensitive information. One common way that an attacker might move laterally is by exploiting vulnerabilities in software that is used internally by the company. VMware EFS can detect and prevent malicious movement that uses known exploits.
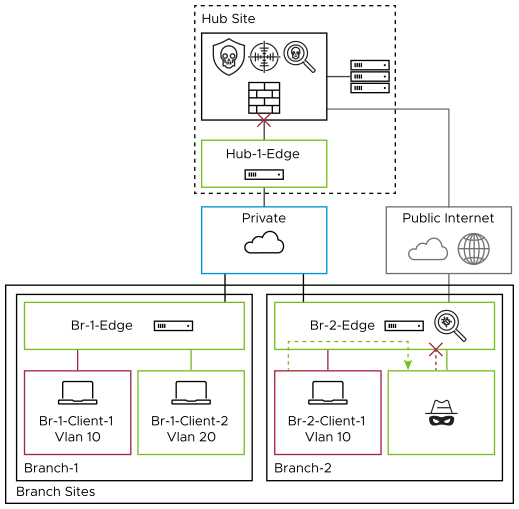
Internet Access without Secure Web Gateway (SWG)
Branches without a direct Internet connection typically access the Internet through a hub site. Hub sites often have dedicated next-generation firewalls (NGFWs) at the perimeter. Leveraging these existing firewalls at the hub can be a more efficient approach.
Branch with Direct Internet Access (DIA)Direct Internet Access (DIA) offers a number of advantages for Enterprises, including:
- Improved performance for cloud-based applications, as traffic does not need to be backhauled to a hub site.
- Potential cost savings, as DIA is typically cheaper than a private MPLS connection.
- The ability to deploy sites quickly, as getting a private MPLS link installed at a branch can take months.
These benefits come with trade-offs concerning security. By adding DIA, you are bypassing the perimeter security. VMware EFS provides similar protection as you would find on the perimeter, so you realize all the benefits that come with DIA while stopping malicious activity.
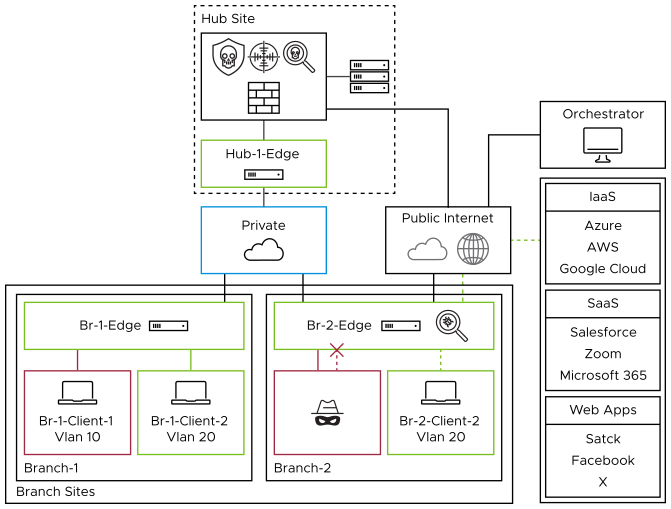
Branch with Internet Access with Secure Web Gateway (SWG)

VMware EFS can be combined with Symantec Cloud Secure Web Gateway (SWG) to provide a more well-rounded security approach. VMware EFS protects your network from malicious activity by analyzing traffic patterns against signatures of known threats and anomalous behavior. In contrast, Symantec Cloud SWG primarily focuses on Internet-bound traffic, with features such as SSL Decryption, DLP, CASB, and URL and Content Filtering. Together, they provide a multi-tiered defense, protecting internal network operations and external web interactions from various cyber threats.
To configure a Symantec Cloud SWG policy, see here.