The reference architecture describes the basic topology, use cases, and functionality of the EFS components when activated for accessing applications in a multi-cloud environment, whether it be for branch-to-branch traffic, branch-to-hub traffic, or when accessing SaaS applications on the public cloud.
Topology
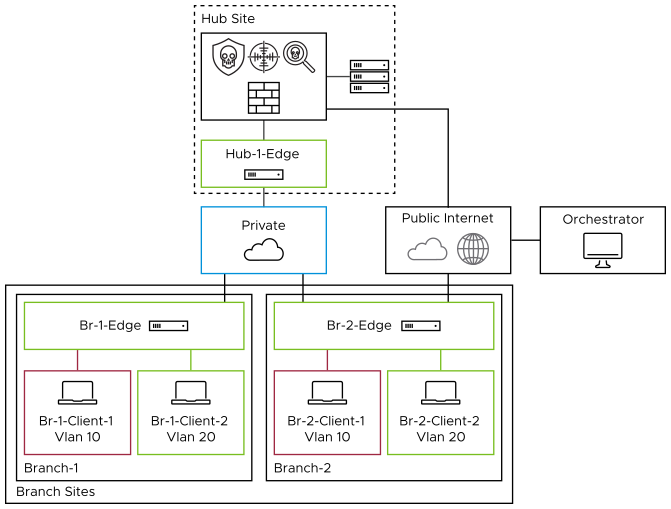
Use Cases
| Use Case | Description |
| Private Access | Private Access refers to those inter and intra-branch communications. While perimeter security is essential, internal traffic protection with VMware EFS ensures that potential threats within the network are promptly identified and neutralized, thus maintaining the integrity and confidentiality of organizational assets. |
| Internet Access without Secure Web Gateway (SWG) | Direct Internet Access (DIA) provides direct connectivity to the Internet, which can improve efficiency and user experience. However, it also introduces new security challenges. Deploying VMware EFS ensures that this convenience does not come at the cost of security, safeguarding your Enterprise from potential threats. |
| Internet Access with Secure Web Gateway (SWG) |
A more comprehensive approach for securing Internet/SaaS traffic would be to pair VMware EFS with Symantec Cloud Secure Web Gateway and its many security capabilities, such as sandboxing, SSL decryption, URL and content filtering, Data Loss Prevention (DLP), and Cloud Access Security Broker (CASB). |
EFS Features
IDS/IPS
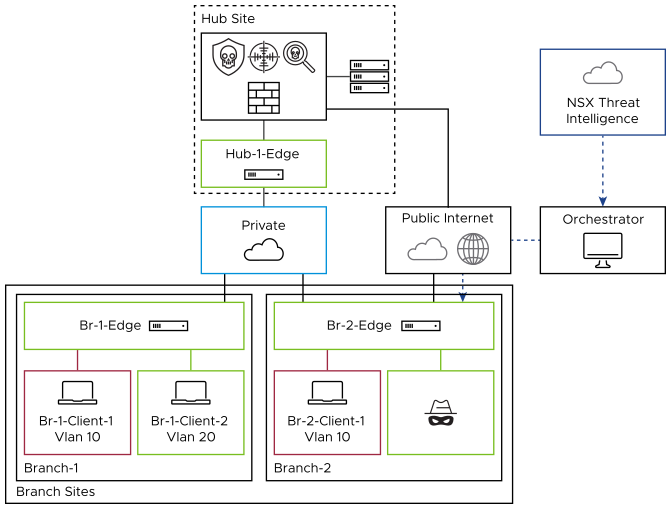
VMware Hosted Logging
Regionally hosted logging is included in the base VMware SD-WAN license. This means that logs are stored in the same region as the Orchestrator (virtual controller). By default, 15 GB of logs per Enterprise or seven days of logs per Edge, whichever comes first, will be kept. Logs can be viewed under the Firewall Logs section of the dashboard. There are options to search and filter for the specific data needed for troubleshooting or investigating. From this view, there is also a button to export the logs locally into a CSV format.

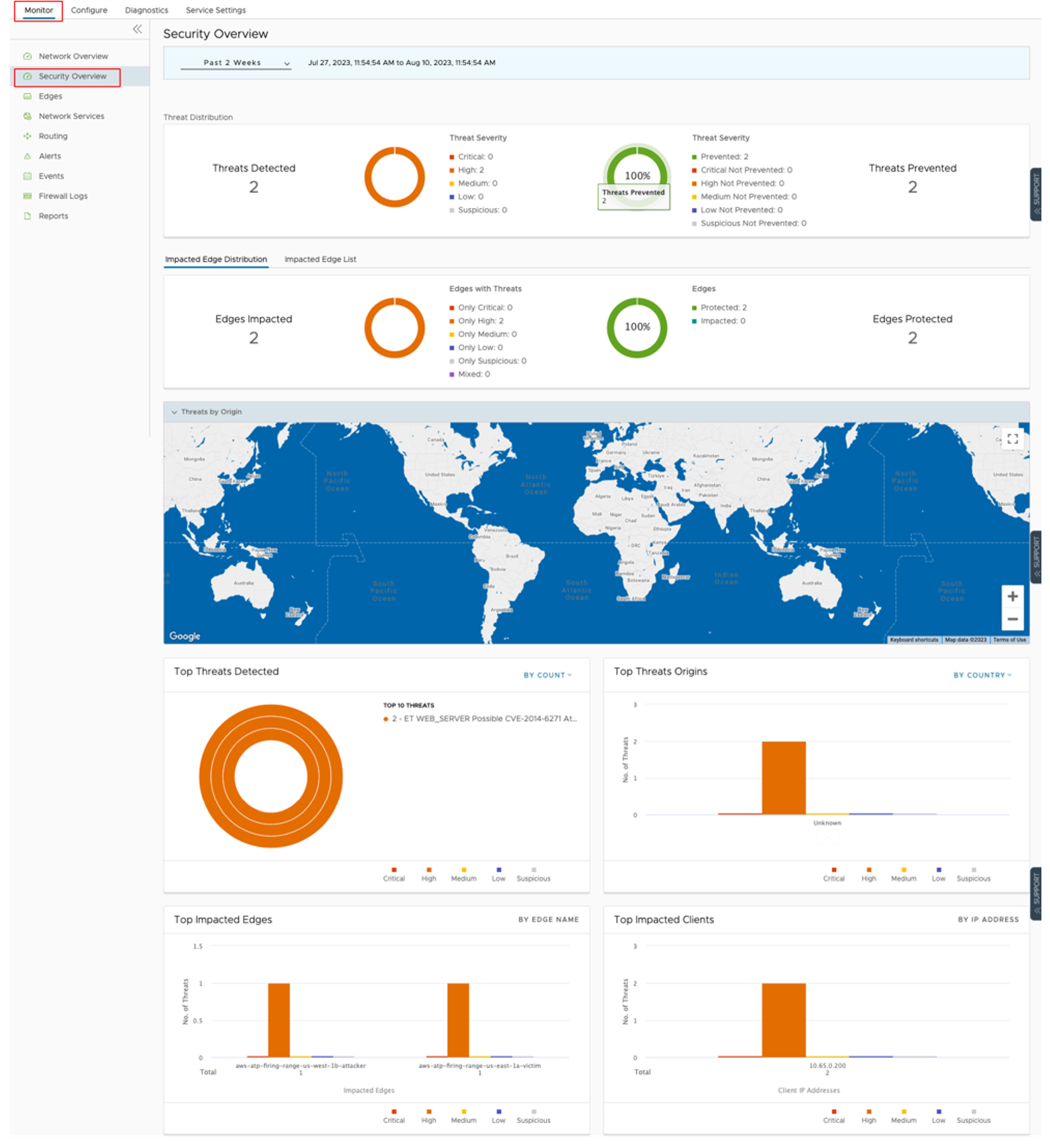
Security Overview Dashboard
The Security Overview dashboard provides a comprehensive overview of your Enterprise's threat landscape. A quick response is essential in addressing threats. This dashboard displays threats and their severity, the source of attacks, and the affected Edges, allowing you to take corrective action quickly.
Solution Components
- VMware Edge Cloud Orchestrator (Hosted by VMware or On-prem)
- On-prem deployments require additional conversation and configuration. Contact the SD-WAN Support Team.
- VMware SD-WAN Edge. All actively selling Edge types (physical and virtual) support Enhanced Firewall Services (EFS).
System Requirements
To benefit from Enhanced Firewall Services (EFS), an additional license (VCX-EFW-100M-12P-C) must be purchased and activated.