When you create a new Gateway, you are automatically redirected to the Configure Gateways page, where you can configure the properties and other additional settings for the Gateway.
To configure an existing Gateway:
Procedure
- In the Operator portal of the SASE Orchestrator, click the Gateway Management tab and go to Gateways in the left navigation pane.
The Gateways page displays the list of available Gateways.
- Click the link to a Gateway that needs to be configured for additional settings. The details of the selected Gateway are displayed in the Configure > Gateways page.
- In the Overview tab, you can configure the following details:
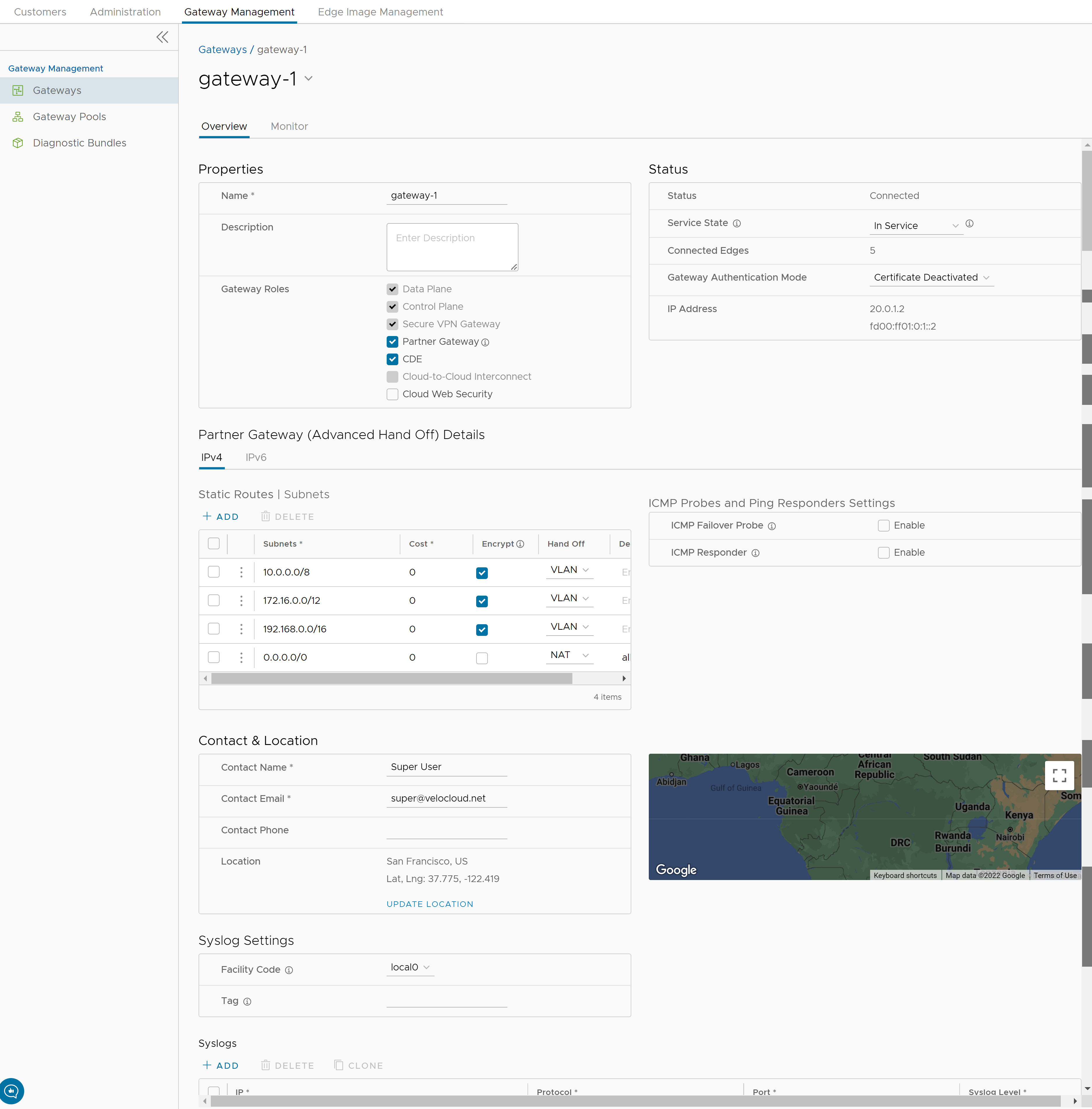
Option Description Properties Displays the existing Name and Description of the selected Gateway. If required, you can modify the information. You can also configure the Gateway Roles, as required:- Data Plane - Enables the Gateway to operate in the Data plane and is selected by default.
- Control Plane - Enables the Gateway to operate in the Control plane and is selected by default.
- Secure VPN Gateway - Select the option to use the Gateway to establish an IPsec tunnel to a Non SD-WAN Destination.
- Partner Gateway - Select the checkbox to allow the Gateway to be assigned as a Partner Gateway for Edges. If you select this option, configure the additional settings in the Partner Gateway (Advanced Handoff) Details section.
- CDE - Enables the Gateway to operate in Cardholder Data Environment (CDE) mode. Select this option to assign the Gateway for customers who require to transmit PCI traffic.
- Cloud-to-Cloud Interconnect - Select the option to enable cloud-to-cloud-interconnect (CCI) tunnels on the VMware SD-WAN Gateways.
Note: This Gateway Role option is shown if the
session.options.enableZscalerCcisystem property is set toTrue. - Cloud Web Security - Enables an Operator User with either a Superuser or Standard role to configure a SD-WAN Gateway for a Cloud Web Security (CWS) role. For more information, see VMware SD-WAN Cloud Web Security Configuration Guide published at https://docs.vmware.com/en/VMware-Cloud-Web-Security/index.html.
Status You can configure the following details: - Status - Displays the status of the Gateway which reflects the success or failure of periodic heartbeats sent to the Orchestrator. The following are the available statuses:
- Connected - Gateway is heart beating successfully to the Orchestrator.
- Degraded - Orchestrator has not heard from the Gateway for at least one minute.
- Offline - Orchestrator has not heard from the Gateway for at least two minutes.
- Service State - Select the Service State of the Gateway from the following available options:
- In Service - The Gateway is connected, and it is available for Primary or secondary tunnel assignments. When the Service state of the Gateway is switched from the 'Out Of Service' to 'In Service' state, the Primary or Secondary assignments, Super Gateways, Edge-to-Edge routes are recalculated for each Enterprise using the Gateway.
- Pending Service - The Gateway is connected, and it is pending for tunnel assignments.
- Out of Service - The Gateway is not connected or not available for any assignments. All the existing assignments are removed.
- Quiesced - The Gateway service is quiesced or paused. No new tunnels or NSD sites can be added to the Gateway. However, the existing assignments would still remain in the Gateway. Select this state for backup or maintenance purposes.
Note: The Quiesced and Out of Service states are only applicable for Cloud Gateway deployment.
When the Service state is Quiesced, Orchestrator provides a self-service migration functionality that allows you to migrate from your existing Gateway to a new Gateway without your Operator’s support.
For more information, see Quiesce Gateways.
Note: Self-service migration is not supported on Partner Gateways.
- Connected Edges - Displays the number of Edges connected to the Gateway. This option is displayed only when the Gateway is activated.
- Gateway Authentication Mode - Select the authentication mode of the Gateway from the following available options:
- Certificate Deactivated - Gateway uses a pre-shared key mode of authentication.
- Certificate Acquire - This option is selected by default and instructs the Gateway to acquire a certificate from the certificate authority of the SASE Orchestrator, by generating a key pair and sending a certificate signing request to the Orchestrator. Once acquired, the Gateway uses the certificate for authentication to the SASE Orchestrator and for establishment of VCMP tunnels.
Note: After acquiring the certificate, the option can be updated to Certificate Required.
- Certificate Required - Gateway uses the PKI certificate. Operators can change the certificate renewal time window for Gateways using the system property
gateway.certificate.renewal.window.
Note: When Gateway certificate is revoked, the Gateway does not receive certificate revocation list (CRL) as it loses TLS connection immediately. Anyway, the Gateway is still operable.Note: The current QuickSec design checks CRL time validity. The CRL time validity must match with current time of Edges for the CRL to have impact on new established connection. To implement this, ensure to update Orchestrator time properly to match with date and time of Edges. - IP Address - Displays the public IP address that public WAN links of an Edge use to connect to the Gateway. This IP address is used to uniquely identify the Gateway. If you have configured the Gateway with both IPv4 and IPv6 addresses, this field displays both the IP addresses.
If you have created IPv4 only Gateway or if there is an existing IPv4 Gateway upgraded from previous versions, you can enter the IPv6 address to support the dual stack. After you save the changes, the IPv6 address is not sent to the Edges immediately. You can trigger the rebalance operation to push the IPv6 address to the customer and the associated Edges manually or the IPv6 address is sent to the Edges during the next Control Plane update.
Note: Adding IPv6 address is a one-time activity and once you save the changes, you cannot modify the IP addresses.Caution: An incorrectly configured IPv6 address, when pushed to Edges, might lead to failure of the IPv6 tunnelling to the IPv6 Gateway. In such cases, you need to deactivate the Gateway and create a new one to activate both the IPv4 and IPv6 addresses.
Contact & Location Displays the existing contact details. If required, you can modify the information. NSD IP Portability Beginning with the 6.0 Orchestrator release, selecting this option will activate NSD IP Portability for the Gateway. Portable NSD IPs allow an Operators to move NSD configurations to different Gateways in the POP without requiring the customer to reconfigure their tunnels. When the NSD Portability check box is selected, the Orchestrator fetches the following data such as SASE PoP name, NSD Virtual IPv4 Address, and NSD Virtual IPv6 Prefix currently assigned to the Gateway from the Global Services Manager (GSM) and displays it. Click Refresh POP to retrieve the current and updated data.Note: For the "NSD Portability" feature to work as designed, the Operators must ensure that the Gateways are associated with the corresponding PoPs in GSM.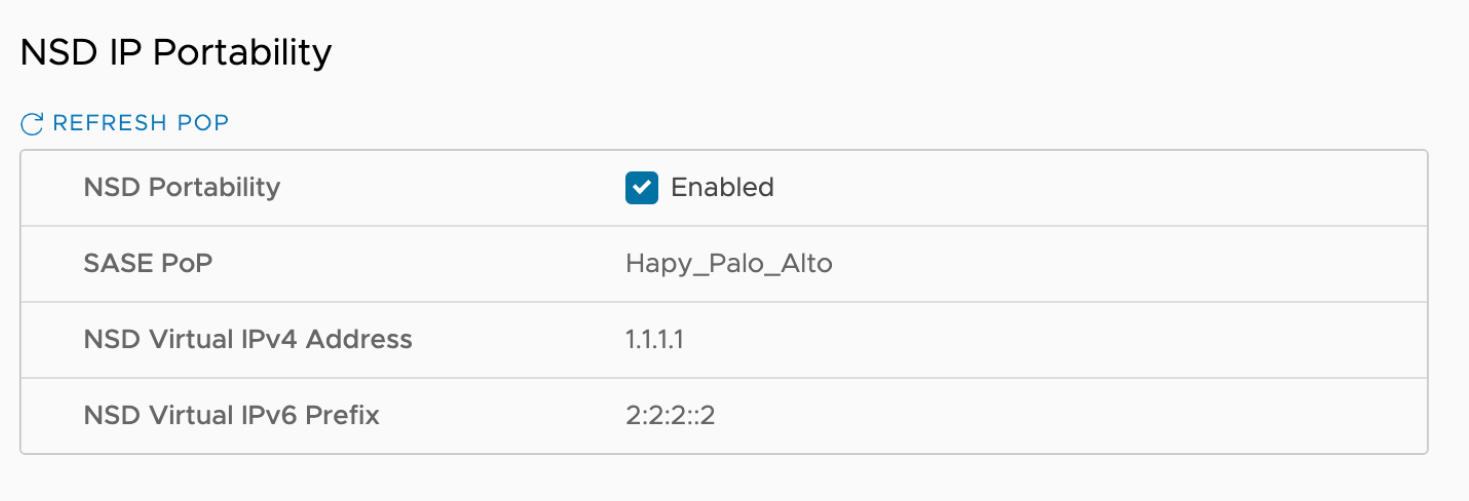 Important: There are two important caveats with NSD IP Portability:
Important: There are two important caveats with NSD IP Portability:- NSD peers must operate as an IKE responder. In the past, some configurations would permit an initiator-only setup, but that will no longer function.
- Peers must allow NAT-T (NAT Traversal). The current implementation of NSD Portable IP uses NAT which is internal to the POP.
Syslog Settings Beginning with the 4.5 release, Gateways can export NAT information via a remote syslog server or via telegraf to the desired destination. For more information, see the Configure NAT Entry Syslog for Gateways section in the VMware SD-WAN Operator Guide published at https://docs.vmware.com/en/VMware-SD-WAN/index.html. Customer Usage Displays the usage details of different types of Gateways assigned to the customers. Pool Membership Displays the details of the Gateway pools to which the current Gateway is assigned. Partner Gateway (Advanced Handoff) Details This section is available only if you select the Partner Gateway check box. You can configure advanced handoff settings for the Partner Gateway. For more information, see the Partner Gateway (Advanced Handoff) Details section below. Cloud Web Security This section allows you to configure the Generic Network Virtualization Encapsulation (Geneve) endpoint IP address and Points-of-Presence (PoP) name for Cloud Web Security, if the Cloud Web Security Gateway Role is enabled. Partner Gateway (Advanced Handoff) DetailsYou can configure the following advanced handoff settings for the Partner Gateway:
Caution: It is recommended not to push IPv6 configurations to Partner Gateways that are running with Software version earlier than 5.0.Option Description Static Routes | Subnets – Specify the subnets or routes that the SD-WAN Gateway should advertise to the SD-WAN Edge. This is global per SD-WAN Gateway and applies to ALL customers. With BGP, this section is used only if there is a shared subnet that all customers need to access and if NAT handoff is required. Remove the unused subnets from the Static Route list if you do not have any subnets that you need to advertise to the SD-WAN Edge and have the handoff of type NAT.
You can click the IPv4 or IPv6 tab to configure the corresponding address type for the Subnets.
Subnets Enter the IPv4 or IPv6 address of the Static Route Subnet that the Gateway should advertise to the Edge. Cost Enter the cost to apply weightage on the routes. The range is from 0 to 255. Encrypt Select the checkbox to encrypt the traffic between Edge and Gateway. Hand off Select the handoff type as VLAN or NAT. Description Optionally, enter a descriptive text for the static route. ICMP Probes and Ping Responders Settings ICMP Failover Probe – The SD-WAN Gateway uses ICMP probe to check for the reachability of a particular IP address and notifies the SD-WAN Edge to failover to the secondary Gateway if the IP address is not reachable. This option supports only IPv4 addresses. VLAN Tagging Select the VLAN tag from the drop-down list to apply to the ICMP probe packets. The following are the available options: - None – Untagged
- 802.1q – Single VLAN tag
- 802.1ad / QinQ(0x8100) / QinQ(0x9100) – Dual VLAN tag
Destination IP address Enter the IP address to be pinged. Frequency Enter the time interval, in seconds, to send the ping request. The range is from 1 to 60 seconds. Threshold Enter the number of times the ping replies can be missed to mark the routes as unreachable. The range is from 1 to 10. ICMP Responder - Allows the SD-WAN Gateway to respond to the ICMP probe from the next hop router when the tunnels are up. This option supports only IPv4 addresses. IP address Enter the virtual IP address that will respond to the ping requests. Mode Select one of the following modes from the drop-down list: - Conditional – SD-WAN Gateway responds to the ICMP request only when the service is up and when at least one tunnel is up.
- Always – SD-WAN Gateway always responds to the ICMP request from the peer.
Note: The ICMP probe parameters are optional and recommended only if you want to use ICMP to check the health of the SD-WAN Gateway. With BGP support on the Partner Gateway, using ICMP probe for failover and route convergence is no longer required. For more information on configuring BGP support and handoff settings for a Partner Gateway, see Configure Partner Handoff. - After configuring the required details, click Save Changes.