The My Account page allows you to configure basic user information, SSH keys, and API tokens. You can also view the current user's role and the associated privileges.
Ensure to configure privileges for a user to access Edges in a secure manner. You must choose Basic access level for the user. You can configure the access level when you create a new user (under User Management), and choose to modify it at a later point in time. Ensure that you have Superuser role to modify the access level for a user.
- Click the User icon in the Global Navigation located at the top right of the screen.
- The User Information panel is displayed as shown below:
- Click the My Account button. The following screen appears:
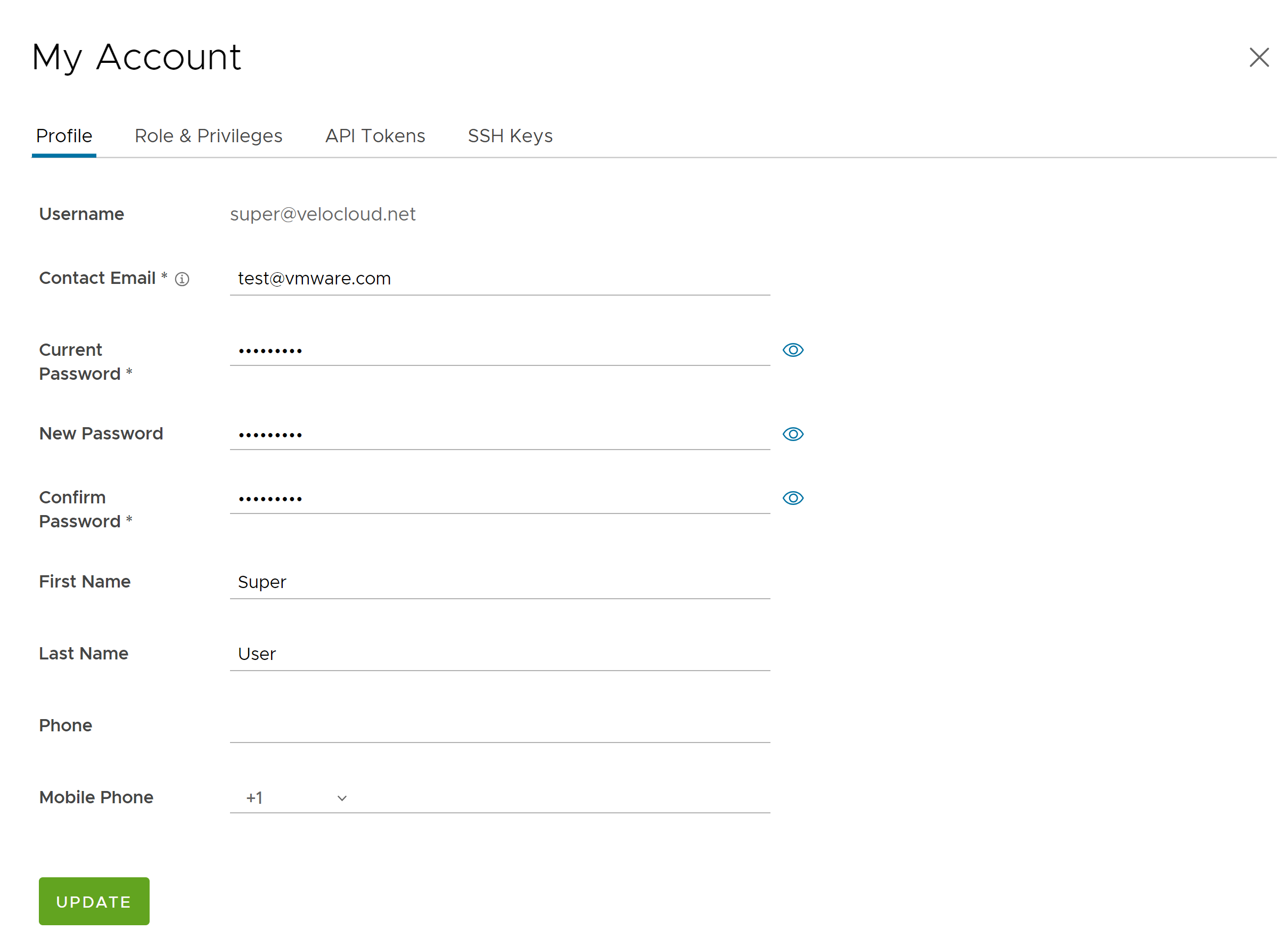
- The Profile tab is displayed by default. You can update the following basic user details:
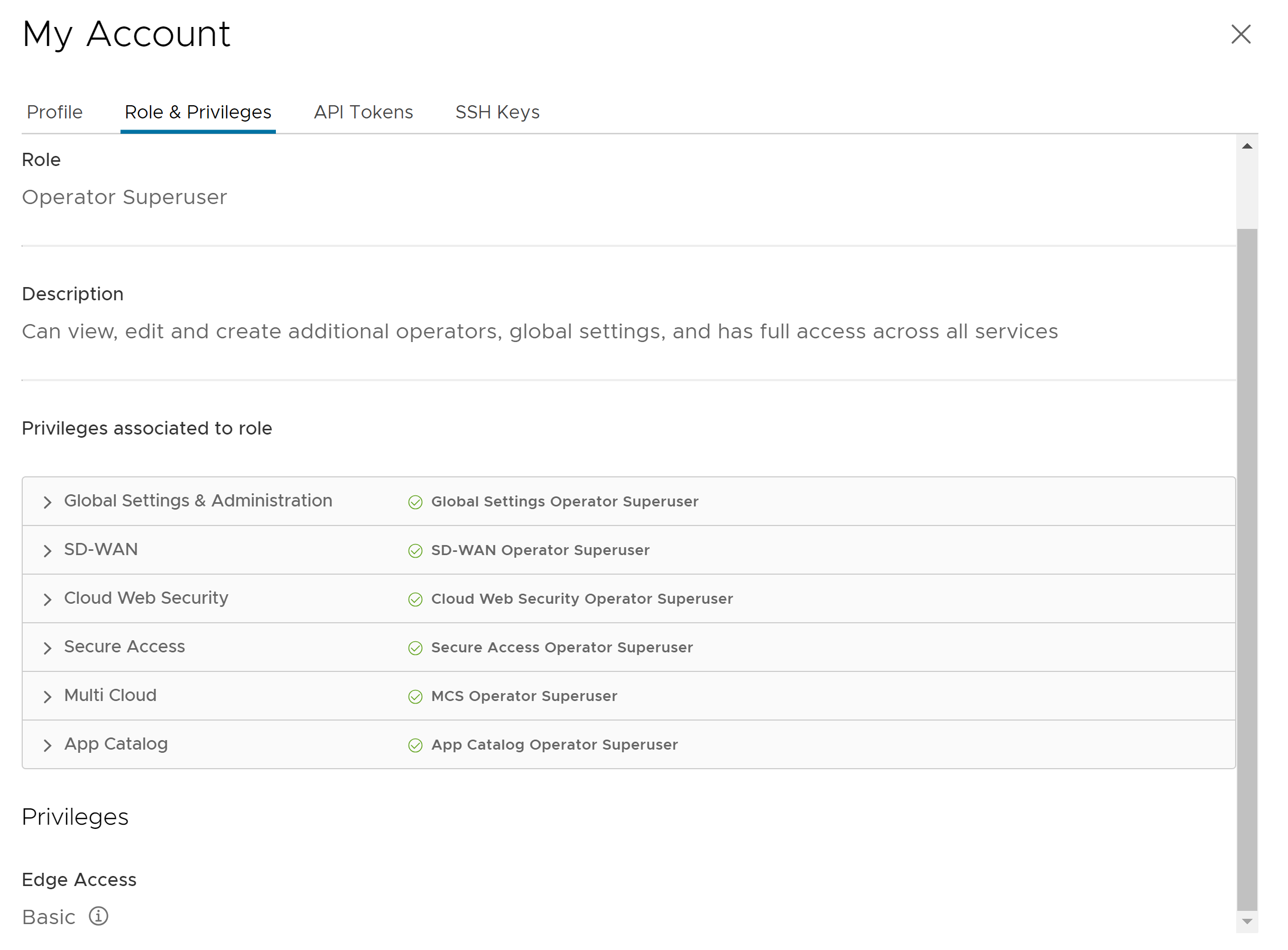
Option Description Username Displays the username and it is a read-only field. Contact Email Enter the primary contact email address of the user. Current Password Enter the current password. New Password Enter the new password. Note: Starting from the 4.5 release, the use of the special character "<" in the password is no longer supported. In cases where users have already used "<" in their passwords in previous releases, they must remove it to save any changes on the page.Confirm Password Re-enter the new password. First Name Enter the first name of the user. Last Name Enter the last name of the user. Phone Enter the primary phone number of the user. Mobile Phone Enter the mobile number of the user along with the country code. - Click the Role tab to view the existing user role and description. It also displays the privileges associated with the user role.
- Click the API Tokens tab. The following screen is displayed.
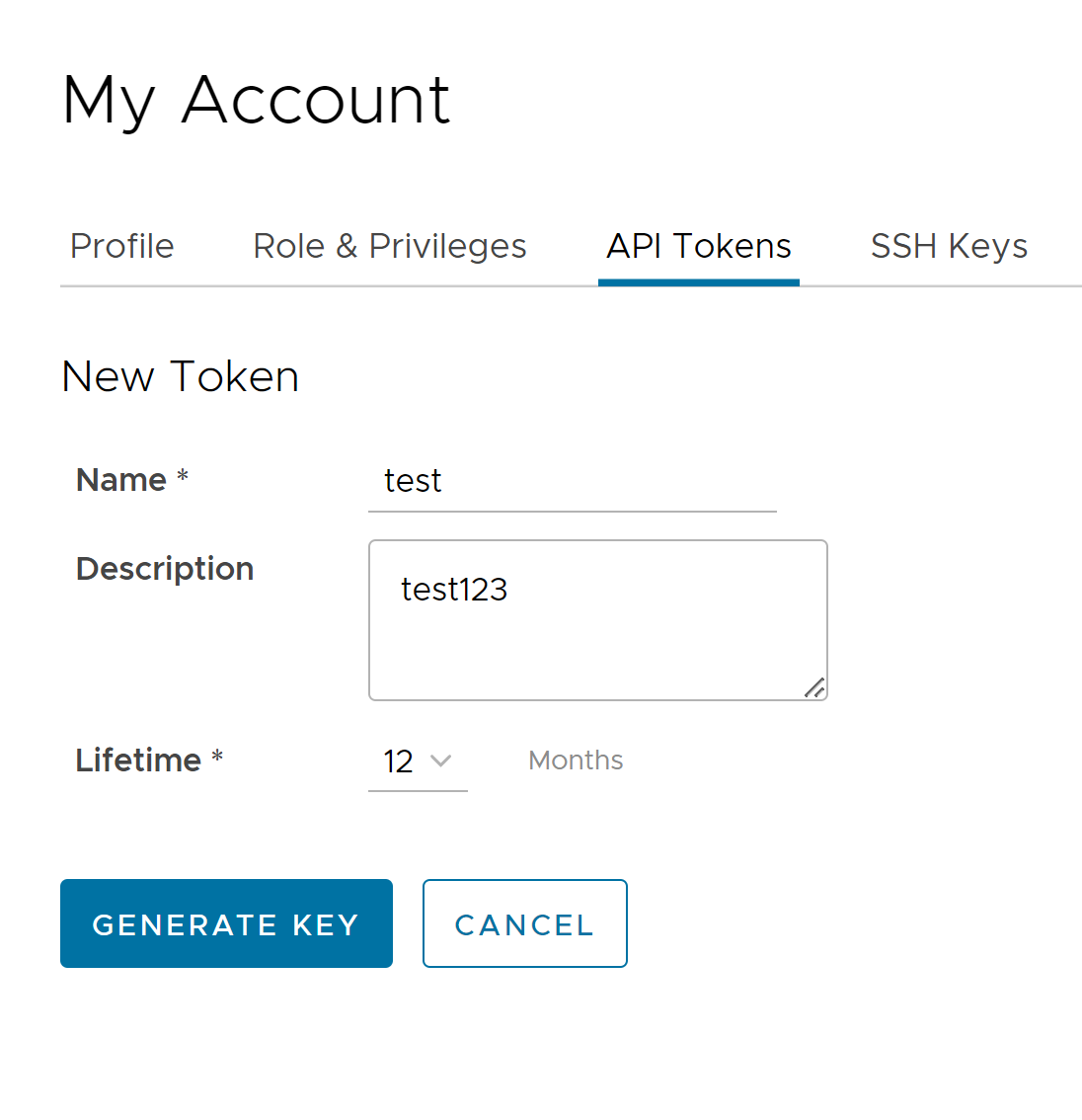
- Enter a Name and Description for the token, and then choose the Lifetime from the drop-down menu.
- Click Generate Key.
- Click the SSH Keys tab to configure a Secure Shell (SSH) key-based authentication.
The SSH key-based authentication is a secure and robust authentication method to access VMware SD-WAN Edges. It provides a strong, encrypted verification and communication process between users and Edges. The use of SSH keys bypasses the need to manually enter login credentials and automates the secure access to Edges.When using key-based authentication to access Edges, a pair of SSH keys are generated - Public and Private.Note:
- Both the Edge and the Orchestrator must be using Release 5.0.0 or later for this feature to be available.
- Users with Operator Business or Business Specialist account roles cannot access Edges using key-based authentication.
The public key is stored in the database and is shared with the Edges. The private key is downloaded to your computer, and you can use this key along with the SSH username to access Edges. You can generate only one pair of SSH keys at a time. If you need to add a new pair of SSH keys, you must delete the existing pair and then generate a new pair. If a previously generated private key is lost, you cannot recover it from the Orchestrator. You must delete the key and then add a new key to gain access.
Based on their roles, users can perform the following actions:- All users, except users with Operator Business or Business Specialist account roles, can create and revoke SSH keys for themselves.
- Operator Super users can manage SSH keys of other Operator users, Partner users, and Enterprise users, if the Partner user and Enterprise user have delegated user permissions to the Operator.
- Partner Super users can manage SSH keys of other Partner users and Enterprise users, if the Enterprise user has delegated user permissions to the Partner.
- Enterprise Super users can manage the SSH keys of all the users within that Enterprise.
- Super users can only view and revoke the SSH keys for other users.
Note: Enterprise and Partners Customers without SD-WAN service access are not able to configure or view SSH keys related details.
Click the SSH Keys tab, and then click the Generate Key button. The following screen appears: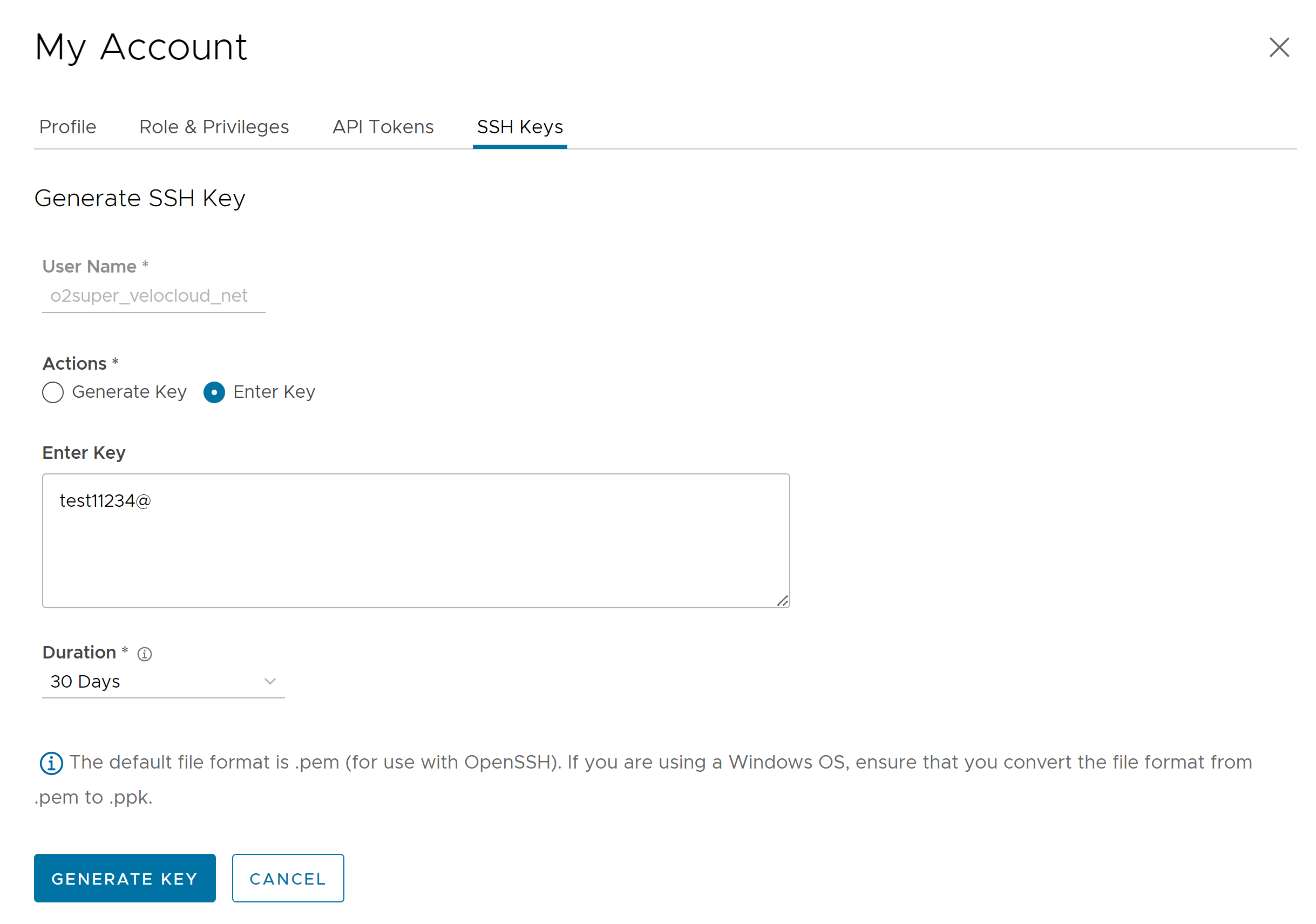
Option Description User Name Displays the username and it is a read-only field. Actions Select either one of the following options: - Generate key: Use this option to generate a new pair of public and private SSH keys.
Note: The generated key gets downloaded automatically. The default file format in which the SSH key is generated is .pem. If you are using a Windows operating system, ensure that you convert the file format from .pem to .ppk, and then import the key. For instructions to convert .pem to .ppk, see Convert Pem to Ppk File Using PuTTYgen.
- Enter key: Use this option to paste or enter the public key if you already have a pair of SSH keys.
PassPhrase If Generate key option is selected, then you have to enter a unique passphrase to further safeguard the private key stored on your computer. Note: This is an optional field and is available only if you select the Generate Key action.Duration Select the number of days by when the SSH key must expire. - Click Generate Key.
Note: Only one SSH Key can be created per user.
- To deactivate an SSH token, click the Revoke button. A pop-up window appears, to confirm the revoke operation. Select the check box, and then click Revoke to permanently revoke the key.
The SSH keys for a user are automatically deleted when:
- You change the user role to Operator Business or Business Specialist because these roles cannot access Edges using key-based authentication.
- You delete a user from the Orchestrator.
Note: When a user is deleted or deactivated from the external SSO providers, the user can no longer access the Orchestrator. But the user's Secure Edge Access keys remain active until the user is explicitly deleted from the Orchestrator as well. Therefore, you must first delete the user from the IdP, before deleting from the Orchestrator.
What to do next:
Ensure that you enable secure Edge access for the Enterprise and switch the authentication mode from Password-based to Key-based. See Enable Secure Edge Access for an Enterprise.