Accessing Visual Software Knowledge Graph
The Visual Software Knowledge Graph in Tanzu Application Catalog makes it easy to organize complex security metadata, with continuous SBOM scanning that helps you quickly discover and act on vulnerability remediations in your open source software.
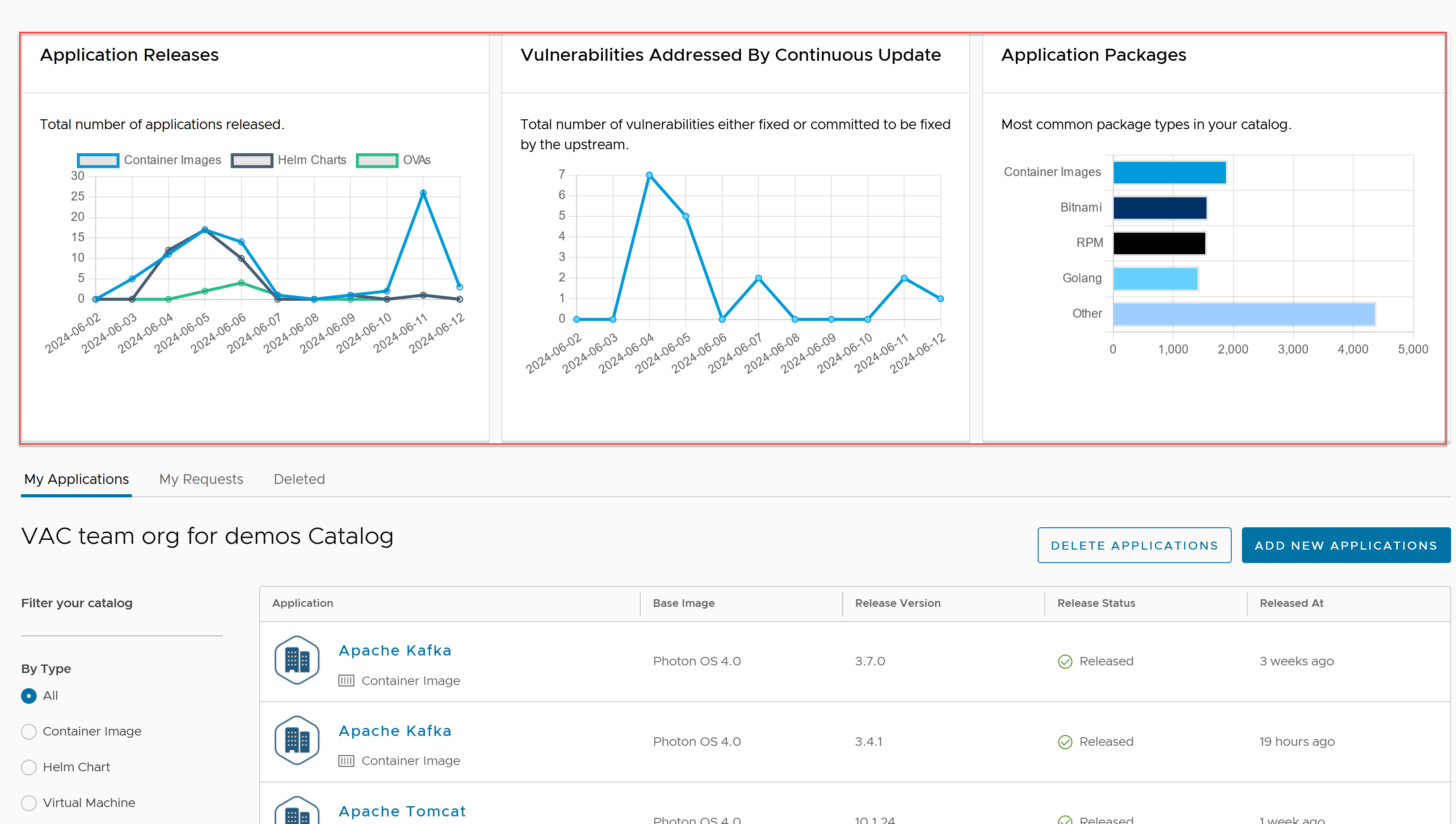
The following information is available: * Application releases: This is the number of new application versions that have been built, verified, and delivered into your registry or registries per day. * Vulnerabilities addressed by continuous update: The number of vulnerabilities that we have patched every day by releasing those updates into your registries. That number also includes future patches that upstream providers have officially committed to delivering. * Application packages: Shows the top package manager contributions to your OSS ecosystem to give you a sense of your reliance on and exposure to various open source ecosystems.
Once you are logged into Tanzu Application Catalog, you can click on individual artifacts to see information specific to each application in graphs and tabular format.
Overview
The Overview tab offers a high-level summary of each application within your catalog.
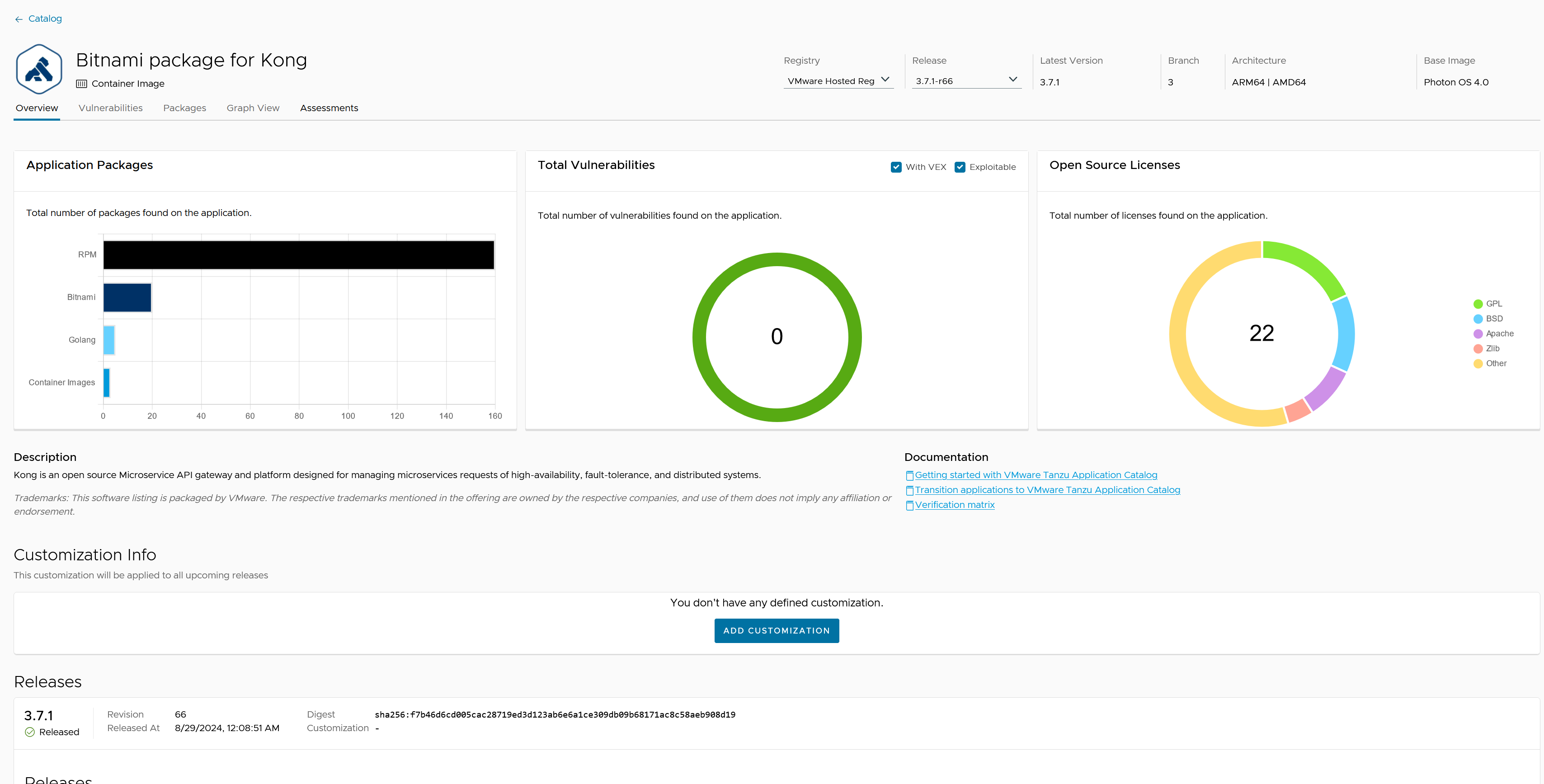
This tab is designed to provide you with essential information at a glance, covering both the current state and the entire history of your catalog. You have the ability to browse all the releases of your applications and compare different versions. To check an older application release, follow these steps: 1. Navigate to the Application’s Details Page: Access the details page of the application you are interested in. 2. Select a Release: At the top of the page, you will find a drop-down menu that lists all available releases. Choose the release you want to explore from this menu.
This functionality includes access to the entire software knowledge graph, allowing you to: * Compare Releases: Analyze different versions of the application to identify changes, improvements, or regressions. * Assess Upgrade Needs: Determine if your running applications require updates based on the comparison of releases. The Overview tab, with its comprehensive historical data and comparison capabilities, is an invaluable tool for maintaining the security and efficiency of your applications in the Tanzu Application Catalog.
Vulnerabilities
The Vulnerabilities tab provides a detailed summary of each application’s security status within your catalog. Leveraging the software knowledge graph, the Software Bill of Materials (SBOM) for each application is scanned for Common Vulnerabilities and Exposures (CVEs) every few hours.
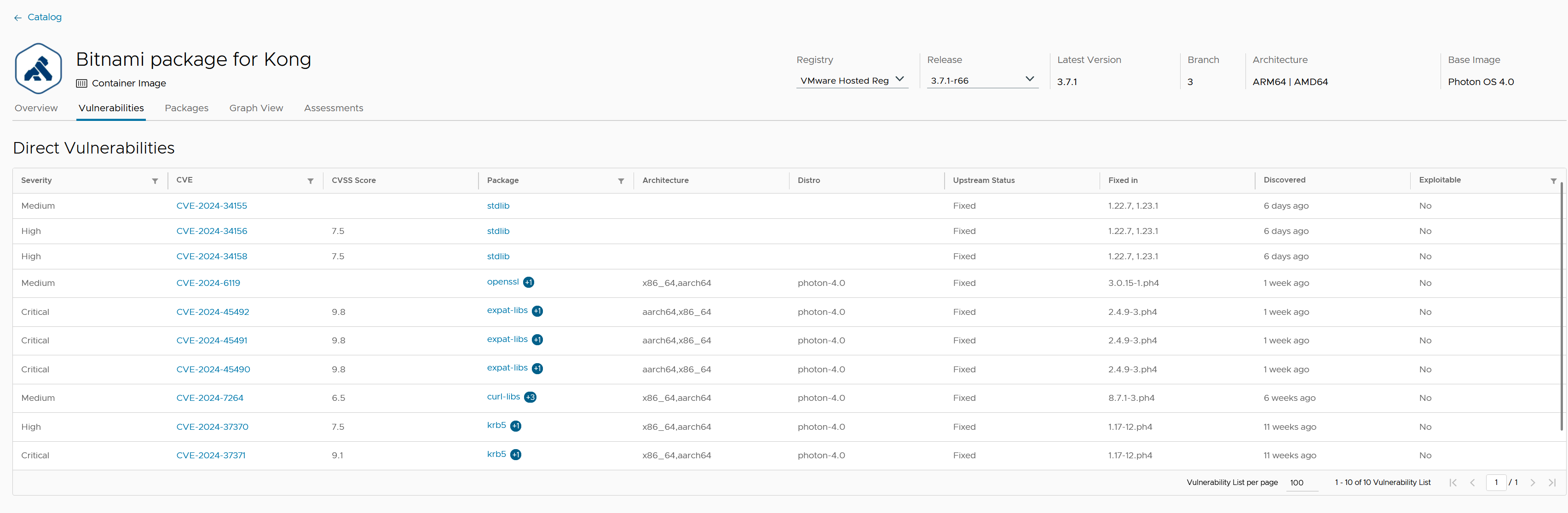
Click on the vulnerability link, for example, in the vulnerabilities section of any of your application releases, to view details about that particular vulnerability displayed in the user interface.
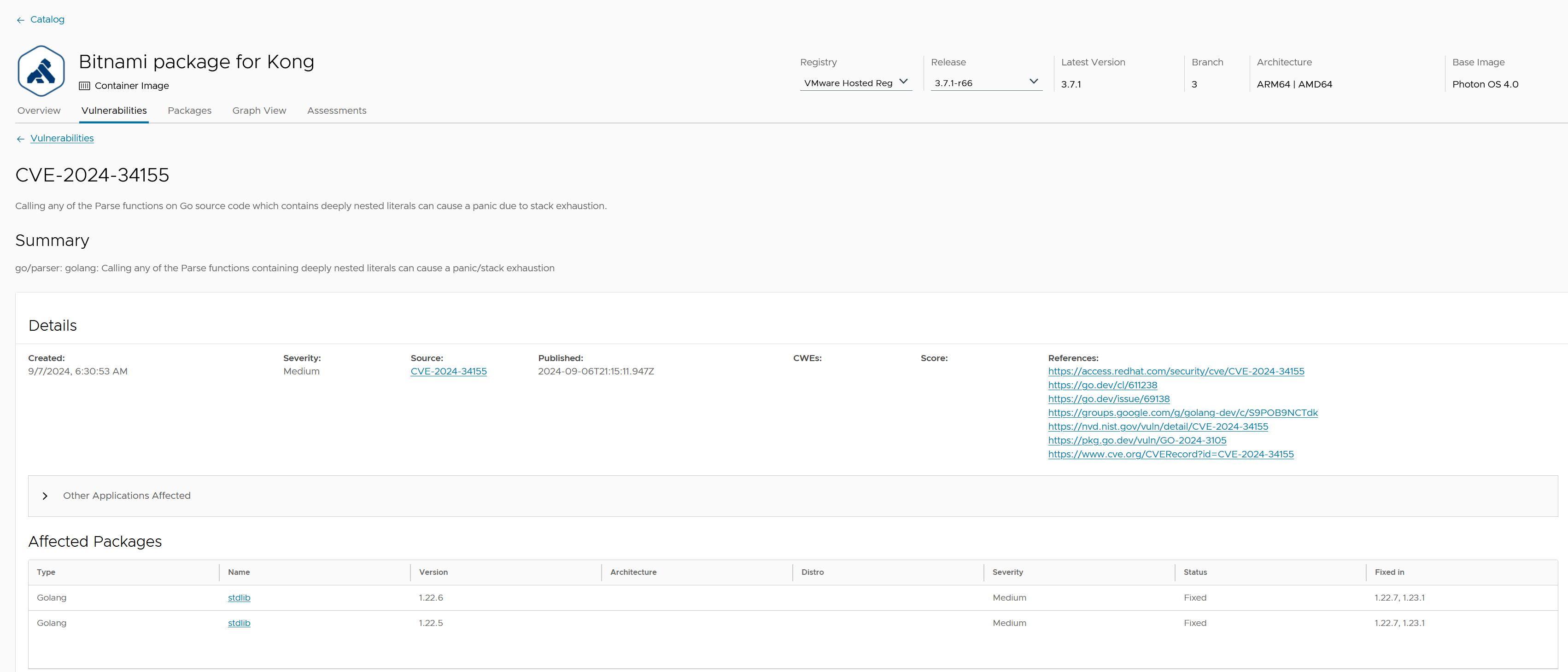
When you scroll down through the page you will find a list of any assessments that has collected about a vulnerability, including the impact and whether it might affect you or not. 
Packages
In the Packages tab, you can see the packages included in the artifact, the number of vulnerabilities grouped by severity, and a chart showing the open source licenses included. You’ll also see tabs that take you to tables showing specific vulnerabilities in the artifacts and which specific packages are bundled.
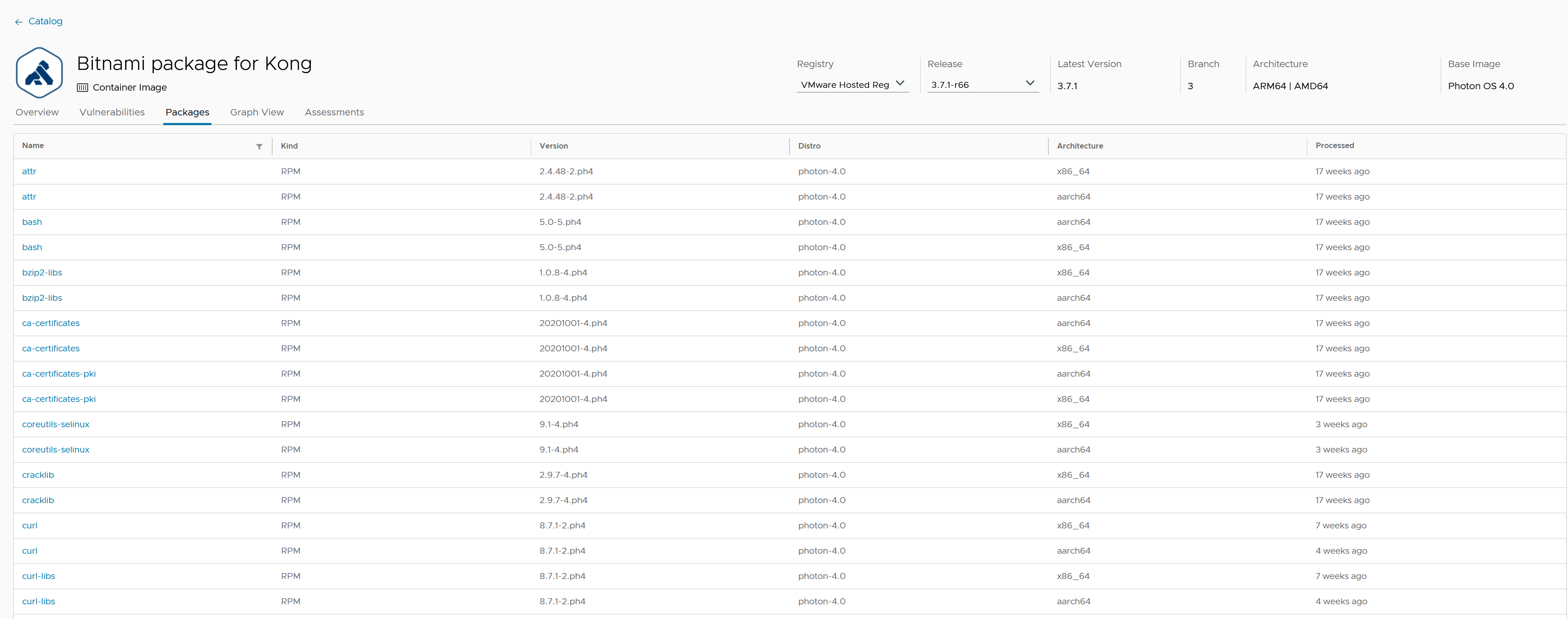
Filters can be used on several fields so you can drill down on specific packages you’re looking for.
Graph view
The Graph view tab gives you a birds eye view of the inter-dependencies between packages, containers, and the underlying systems.
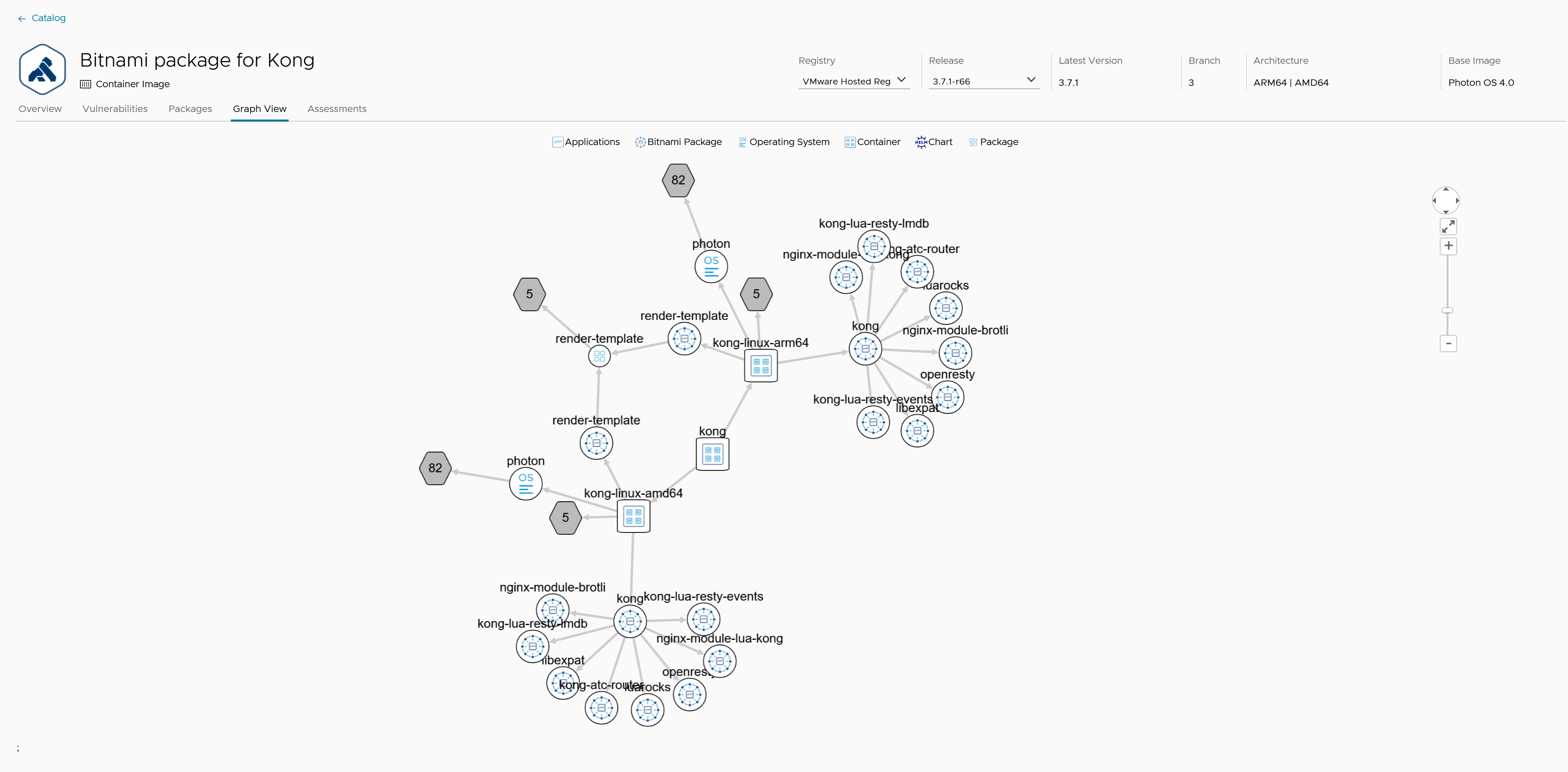
It helps your track:
- Dependencies: It shows how various packages rely on one another.
- Containers: It shows which containers are using or hosting specific packages.
- Source Information: It shows which other containers or packages are sourcing the package in question.
This visual representation is essential when managing or troubleshooting complex systems where different software components need to work together within containerized environments.
Assessments
The “Assessments” tab offers a comprehensive evaluation of vulnerabilities related to the package. It helps users to quickly determine the security status of their software and make informed decisions about updates and mitigations. This is designed to help users understand the status and impact of various Common Vulnerabilities and Exposures (CVEs) affecting the package.
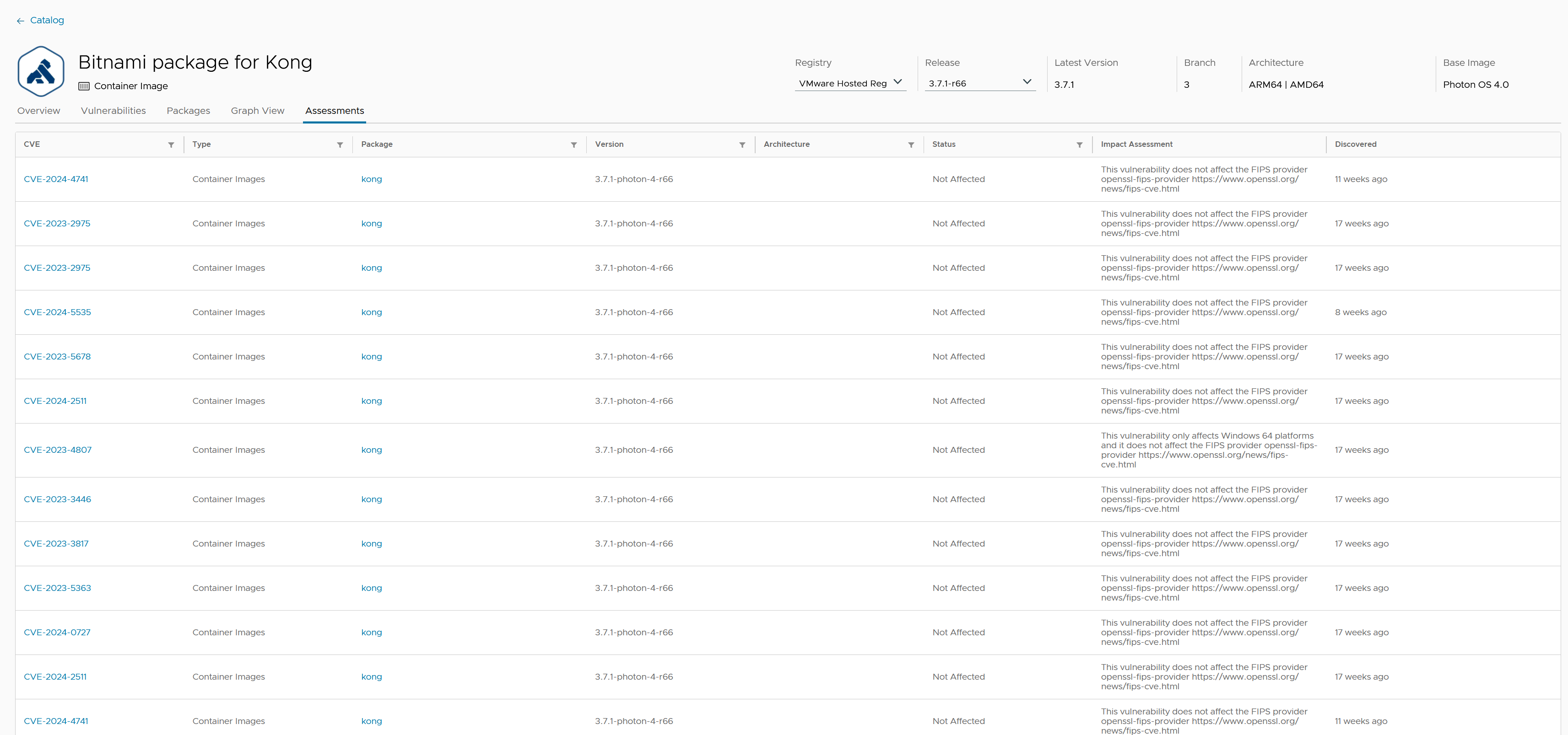 Click on each CVE entry, to view detailed information about the specific vulnerability.
Click on each CVE entry, to view detailed information about the specific vulnerability.